Currently there are multiple varieties of tools for pentesting work, mainly for scanning the target system. This time, pentesting experts from the International Institute of Cyber Security (IICS) will show you how to use REDHAWK from your smartphone, as this scanning tool will give us all kinds of information about the target, including the type of lens, weaknesses and settings in general using the Termux emulator.
Remember that this material was made for entirely academic purposes, so IICS is not responsible for any misuse that may be given to the tool.
DOWNLOAD AND INSTALLATION
To get started, as usual, we’ll update Termux and its contents with the following commands:
apt update && apt upgrade
Download from Github:
apt install git
Download PHP:
apt install php
Download the script:
git clone https://github.com/Tuhinshubhra/RED_HAWK
Next we will run the following command:
cd RED_HAWK
php rhawk.php
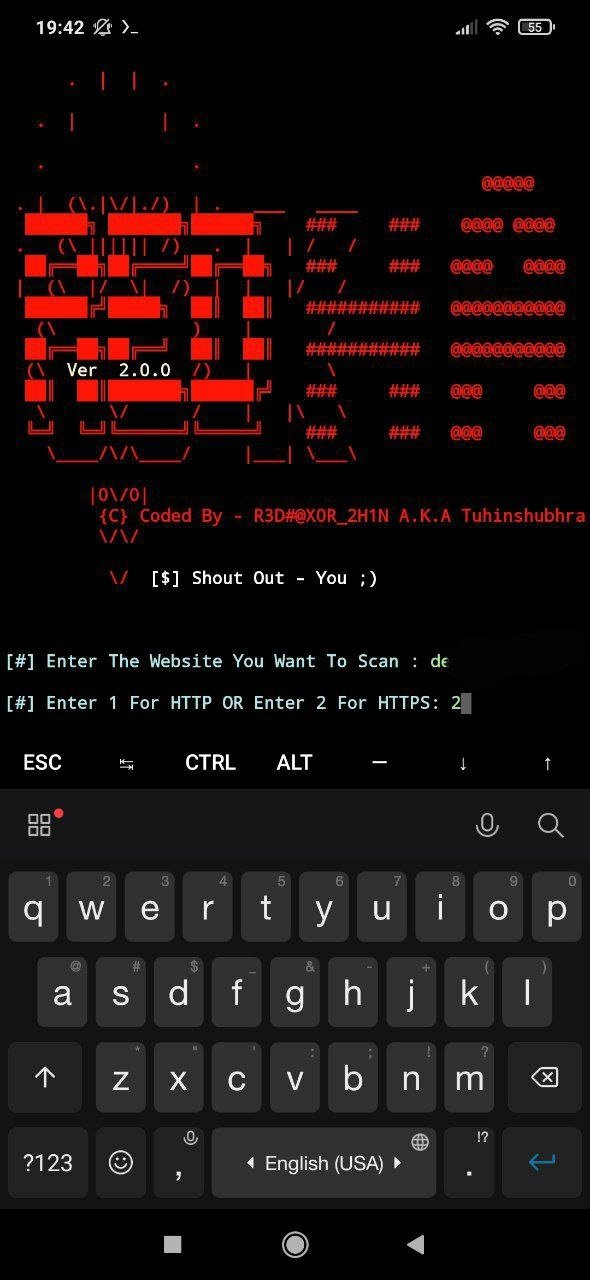
After launching the tool, we enter the target URL (without HTTP/HTTPS) and select http/ https as the following item:
Next, we need to select the check type.
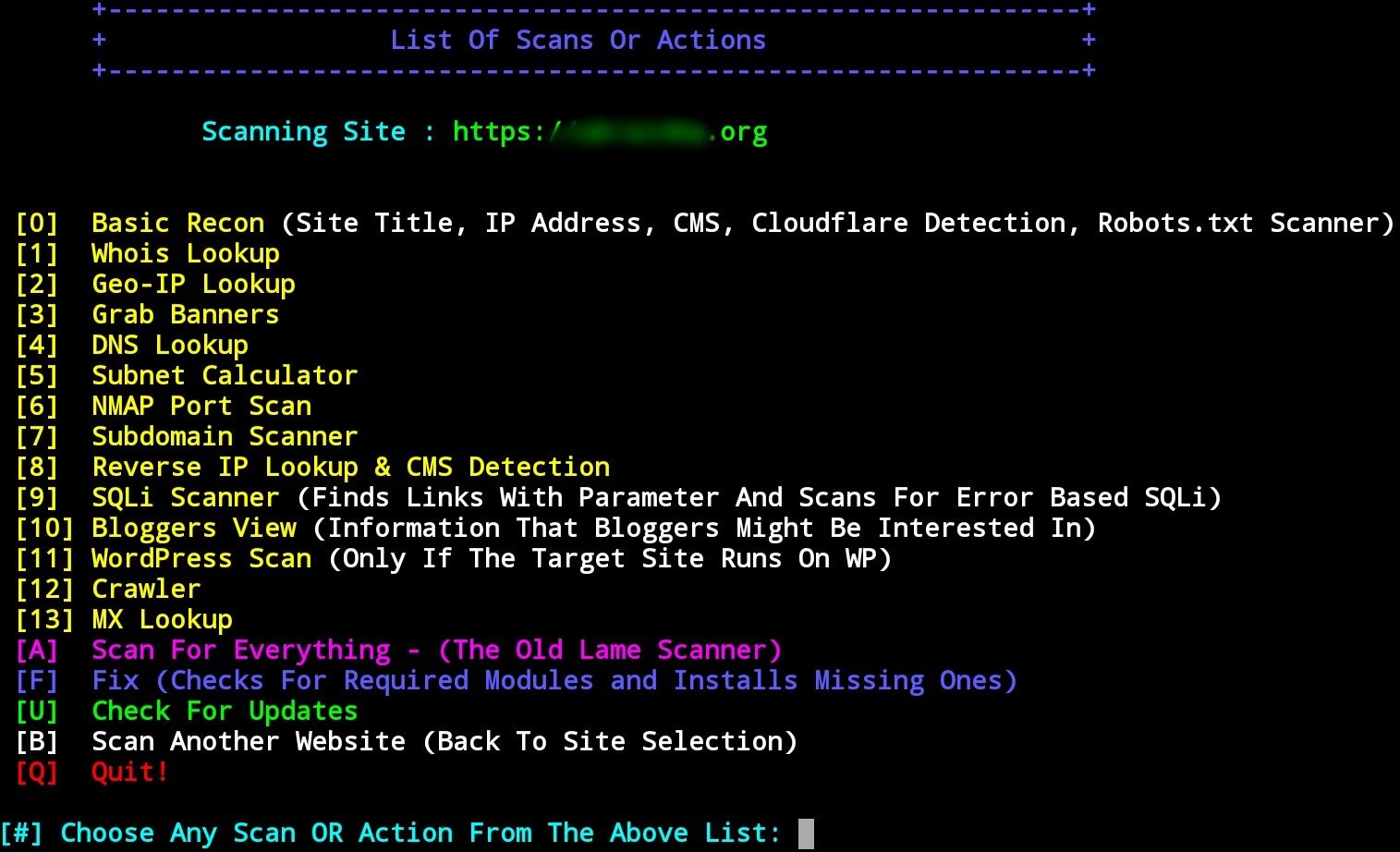
As pentesting experts show us, REDHAWK has multiple target website verification options:
- BASIC SCAN:
- Website name
- IP address
- Web server discovery
- CMS discovery
- Cloudflare discovery
- robots.txt scanner
- Whois search
- Search by geo-IP
- Banner analysis
- DNS lookup
- Subnet calculator
- Nmap port scan
- SUBDOMAIN SCANNER:
- Subdomain
- IP address
- REVERSE IP SEARCH AND CMS DISCOVERY:
- Host name
- IP address
- CMS
- Scanner based on SQLi errors
- BLOGGERS VIEW:
- HTTP response code
- Site name
- Alexa ranking
- Domain authority
- Authority of the page
- Extractor of links to social media
- Link extraction
- WORDPRESS TRACKING:
- Scan confidential files
- Version detection
- Vulnerability Scanner Version
- Crawler
- MX search
- SCAN ALL
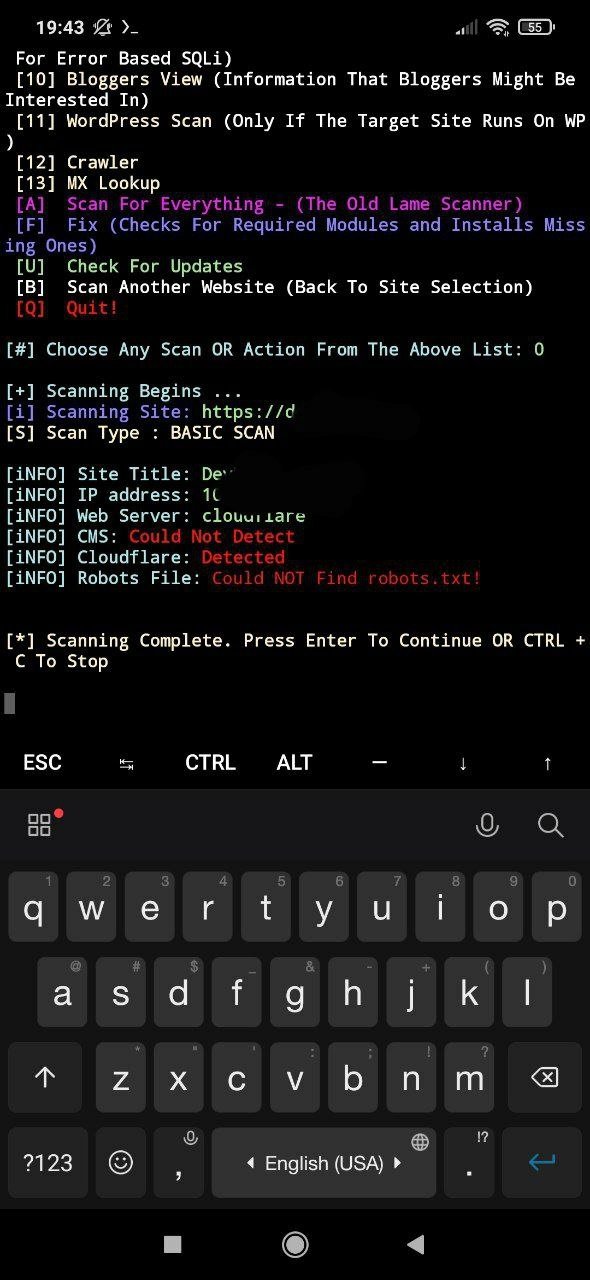
For example, by choosing basic scanning, pentesting experts may discover that Cloudflare is installed on the site, allowing you to learn how to bypass this feature in a possible attack.
And that’s it. It seems very simple, but this tool will allow you to learn countless qualities of a specific platform before deploying a pentesting process. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
