A recent publication by Avast Threat Labs specialists details the finding of a variant of data stealing malware that remained hidden for years in multiple web browser extensions’ code. Experts mention that this malware, dubbed as CacheFlow, went unnoticed by the cybersecurity community for at least three years.
Experts discovered that the malware was hidden in popular third-party extensions, which contained a backdoor for arbitrary JavaScript download and execution. The purpose of CacheFlow operators was to steal sensitive details, including dates of birth, email addresses, Google account activity and even location details to send it to malicious servers.
Malicious extensions could also replace Google and other search engines links with malicious ones to redirect users to phishing and highly intrusive advertisements websites: “Users went through these compromised websites before reaching the legitimate website they wanted to visit,” says researcher Jan Vojtesek. Operators deployed the infection using dozens of extensions for Chrome and Edge, accumulating a total of 3 million downloads. Popular infected extensions include Instagram Story Downlowader, Video Downloader for Facebook and Vimeo Video Downloader.
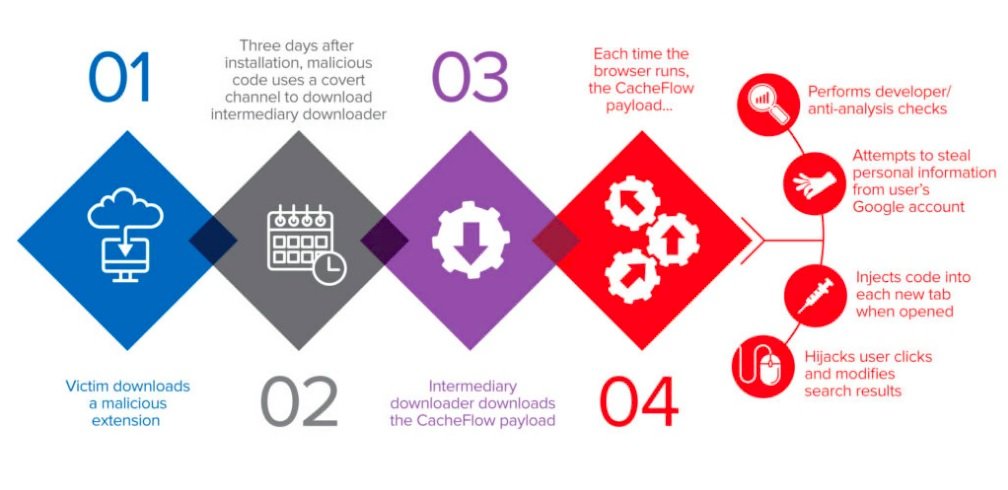
From the cases analyzed, the researchers concluded that the malware remained inactive in the extension until three days after installation. In addition, once that deadline was met, CacheFlow analyzed system activity by trying to assess whether the victim had the knowledge to detect suspicious activity: “For example, if malware detected that developer tools in the browser were activated, it immediately interrupted its malicious processes,” the experts mention.
Another hallmark of CacheFlow is the way infected extensions tried to hide its C&C traffic through an undercover channel using the HTTP Cache-Control header of their scan requests.
This malicious campaign was detected after Avast experts received a report from Czech Republic security expert Edvard Rejthar: “During an in-depth analysis of these extensions we detected a clear trend,” the experts added. On the other hand, some Google Play security reports mentioned anomalous behavior in this kind of tool since 2017.
Both Google and Microsoft removed infected extensions from their platforms after receiving the report in December 2020. Now that malware is known, specialists believe that threat actors are unlikely to use it in subsequent attacks; however, Avast experts point out that this is a clear indication that even the most popular tools can be abused by cybercriminal groups.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
