A team of cybersecurity specialists has released a report related to the exploitation of a critical vulnerability in the Secure Boot component, which would allow altering the boot upload process prior to the start of an operating system. The boot process is based on components known as bootloaders, responsible for loading the firmware of all hardware components on a device.
The flaw, dubbed “BootHole”, resides in the GRUB2 bootloader, one of the most commonly used implementations currently, used in Linux, Windows, and macOS distributions based on BSD systems.
BootHole was detected a few months ago by experts from security firm Eclypsium, who mention that the flaw allows threat actors to alter the vulnerable component in order to insert and execute malicious code during the boot process, allowing you to insert code to take control of the target system. In addition, it is reported that hackers could modify the values of grub.cfg, the vulnerable file, to trigger buffer overflow scenarios in the GRUB2 bootloader.
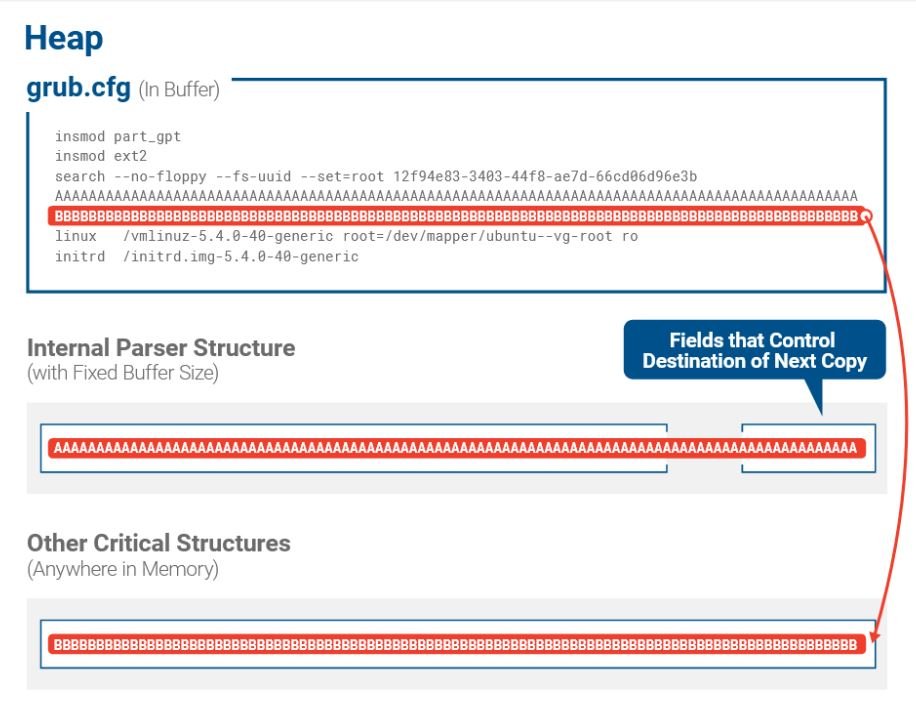
Finally, Eclypsium mentioned that the flaw can be exploited to manipulate the component and replace it with a malicious version. Although these processes are protected with secure boot mechanisms, experts mention that the vulnerability can be exploited with relative ease.
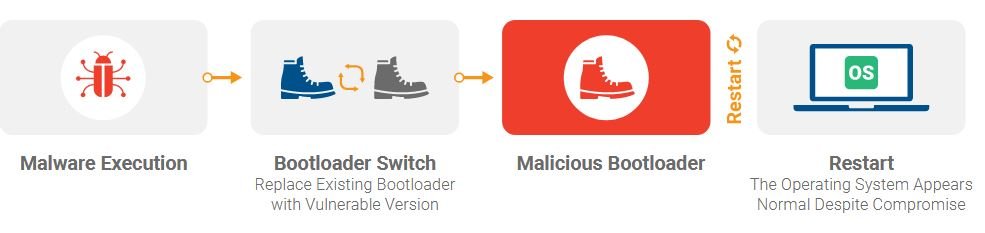
Despite being a highly risky attack technique, BootHole has its limitations. For example, a threat actor requires administrator access to access and manipulate the grub.cfg file, although there is also more than one method for hackers to access this file.
The flaw was tracked as CVE-2020-10713, and has been notified to all actors in the hardware and software security environment. Eclypsium believes that all Linux distributions might be affected by this failure, as they all use GRUB2 bootloaders with external grub.cfg file command reading. In addition, the firm mentions that updates must be released for deployments of Microsoft, Oracle, Red Hat, Debian, among other companies.
Despite constant security alerts and the release of security patches, the experts concluded by mentioning that correcting this type of failure is a highly complex process for companies, so fully mitigating the risk of exploitation could take a few years.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
