Argo CD is a well-known open-source GitOps continuous delivery solution for Kubernetes. It is used to monitor operating applications and compares their real state, which assists administrators in synchronizing running apps with their planned state.
The vulnerability, which has been assigned the tracking number CVE-2023-23947 and has a CVSS score of 9.1, is caused by insufficient permission. The problem first appeared in Argo CD version v2.3.0-rc1, which saves cluster access settings as Kubernetes Secrets. This version of Argo CD is responsible for introducing the problem. An adversary might use this to change out-of-bounds cluster secrets, which would enable them to elevate their privileges or damage the operation of Argo CD. A serious bypass security limitation (CVE-2023-22482) was addressed and patched by Argo CD one month ago. An attacker might use this issue to enable the API to accept certain incorrect tokens.
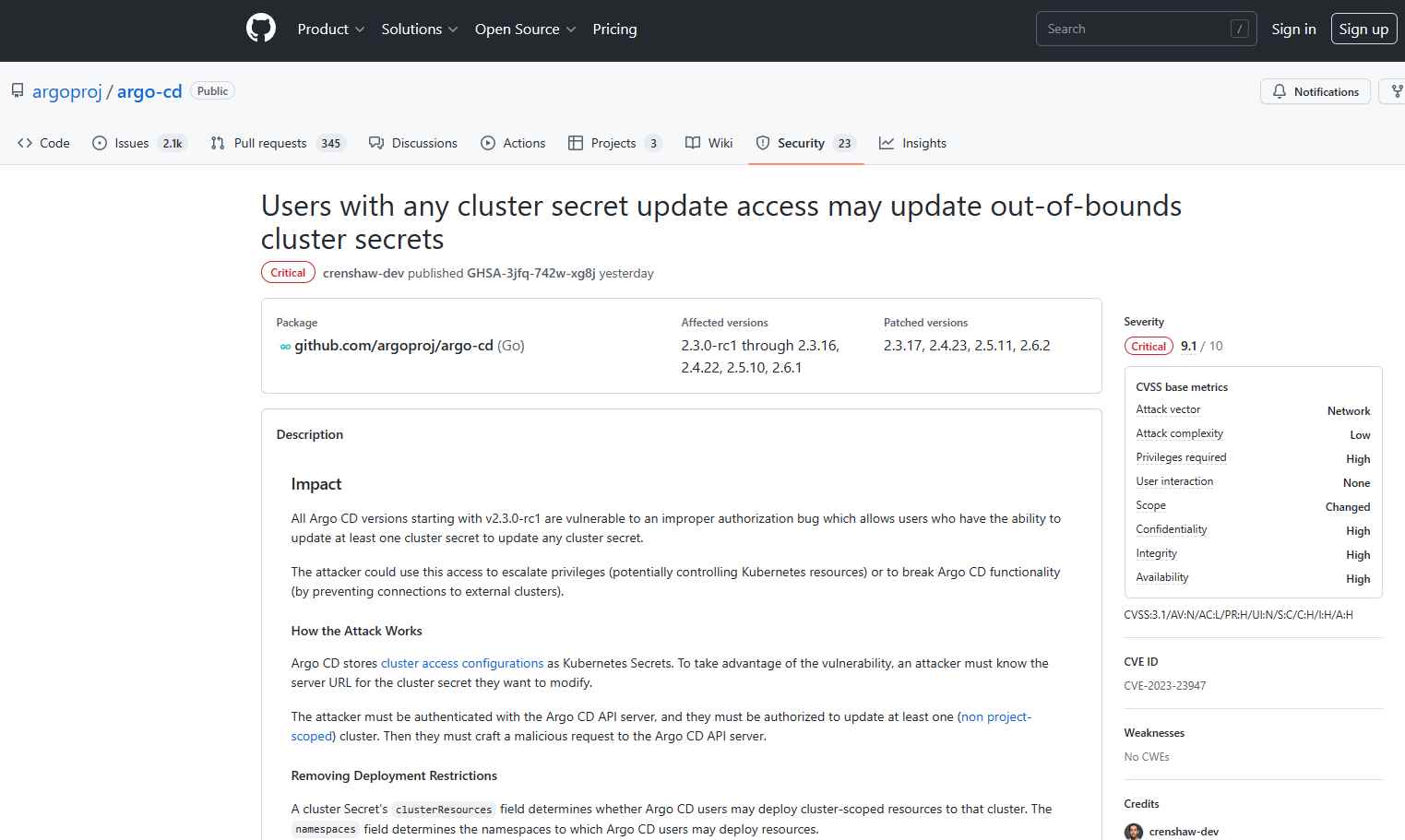
In order to exploit the vulnerability, an attacker has to be aware of the server URL corresponding to the cluster secret that they want to change. The attacker has to be authenticated with the Argo CD API server, and they have to be given permission to update at least one cluster that is not project-scoped. The next step for them is to concoct a nefarious request and send it to the Argo CD API server.
The vulnerability known as CVE-2023-23947 was fixed in Argo CD versions 2.3.17, 2.4.23, 2.5.11, and 2.6.2, which were all released recently.

Users of the Argo CD platform are strongly encouraged to upgrade as quickly as possible to a patched version of the software. Methods of mitigation include controlling resource management using AppProjects and RBAC, as well as limiting the number of people that have access to cluster update.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
