A vulnerability that was only recently found and given the name “Migraine” is connected to macOS migration functionality and represents a significant risk. It gives attackers with root access the ability to avoid macOS’s System Integrity Protection (SIP), which in turn grants them complete control over the compromised device. The security vulnerability, which has been given the moniker “Migraine,” was discovered by experts at Microsoft Threat Intelligence, who immediately informed Apple of their discovery. After further investigation, a tracking identification known as CVE-2023-32369 was issued to the vulnerability.
System Integrity Protection (SIP) is an essential security precaution that macOS implements. Its purpose is to effectively restrict the capabilities of a root user in order to prevent them from doing any acts that might compromise the overall integrity of the system. The primary goal of Apple’s System Integrity Protection (SIP) is to restrict alterations to macOS-protected components to just those processes that have been digitally signed by Apple or that have been validated as having certain entitlements. Examples of these processes include Apple software updates and installers.If SIP is bypassed, there is a possibility that the following severe repercussions may occur:
- Install rootkits
- Develop malicious software that will last.
- Increase the area that may be attacked.
This strategy guarantees that only trustworthy entities who have the appropriate authority are able to make modifications to essential components of the system. SIP ensures that the integrity of the operating system is preserved by rigorously regulating access to macOS components. This also reduces the likelihood that untrusted parties would make illegal changes or attempt to tamper with the system.
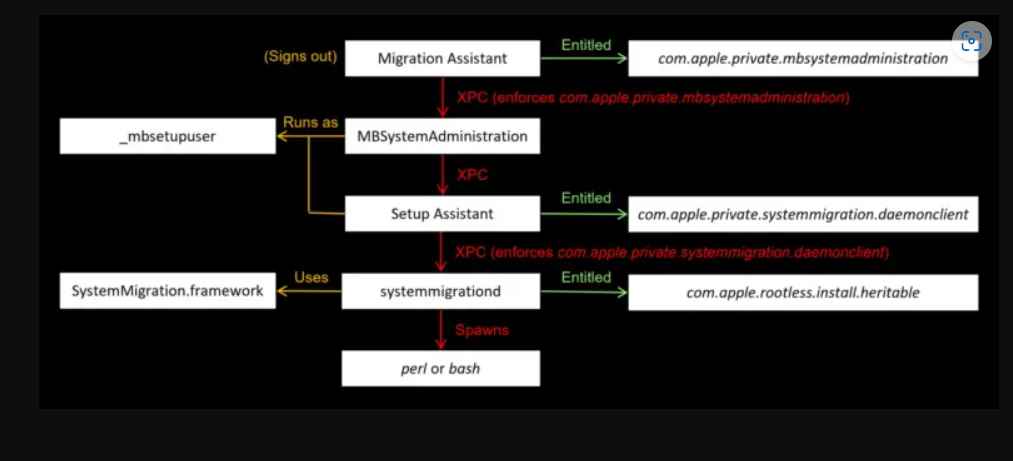
Researchers from Microsoft revealed that attackers who have root capabilities have the potential to bypass SIP security protections by attacking the macOS Migration Assistant program. This can be done by exploiting a vulnerability in the utility. This program uses something called the “systemmigrationd daemon” and has the com.apple file extension.The rootless.install.heritable entitlement provides the means to sidestep SIP.
On May 18, 2023, Apple took action to address the reported vulnerability by integrating a fix into previously issued security upgrades. These updates had been made available by Apple. Therefore, users have the ability to safeguard their systems by swiftly applying these updates in order to reduce the likelihood of possible dangers.
Although it is not feasible to disable SIP without first restarting the system and logging into macOS Recovery, both of which require having direct physical access to the device that has been hacked.
When SIP protection is defeated, not only are the security mechanisms of System Integrity Protection circumvented, but it also gives unfettered access to the victim’s private data by overriding Transparency, Consent, and Control (TCC) regulations. This is because bypassing SIP protection circumvents the security measures of System Integrity Protection. This vulnerability may be used by threat actors to change TCC databases, allowing them to entirely evade the control systems and obtain unauthorized access to critical information.

Working as a cyber security solutions architect, Alisa focuses on bug bounty and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.
