Jenkins, which is sometimes referred to as the “engine” of DevOps, provides users with a vast number of tools that enable them to monitor and control the software delivery processes at any point in the program’s lifetime. Context menus are one of the features that can be found in the Jenkins application. These menus may be used to access different user interface (UI) components such as connections to jobs, builds, or breadcrumbs. Unfortunately, if these features are left unsecured, they may also provide a foothold to attackers, which reduces the effectiveness and speed of the system. To put things more specifically, here is where the CVE-2023-35141 vulnerability comes into play.
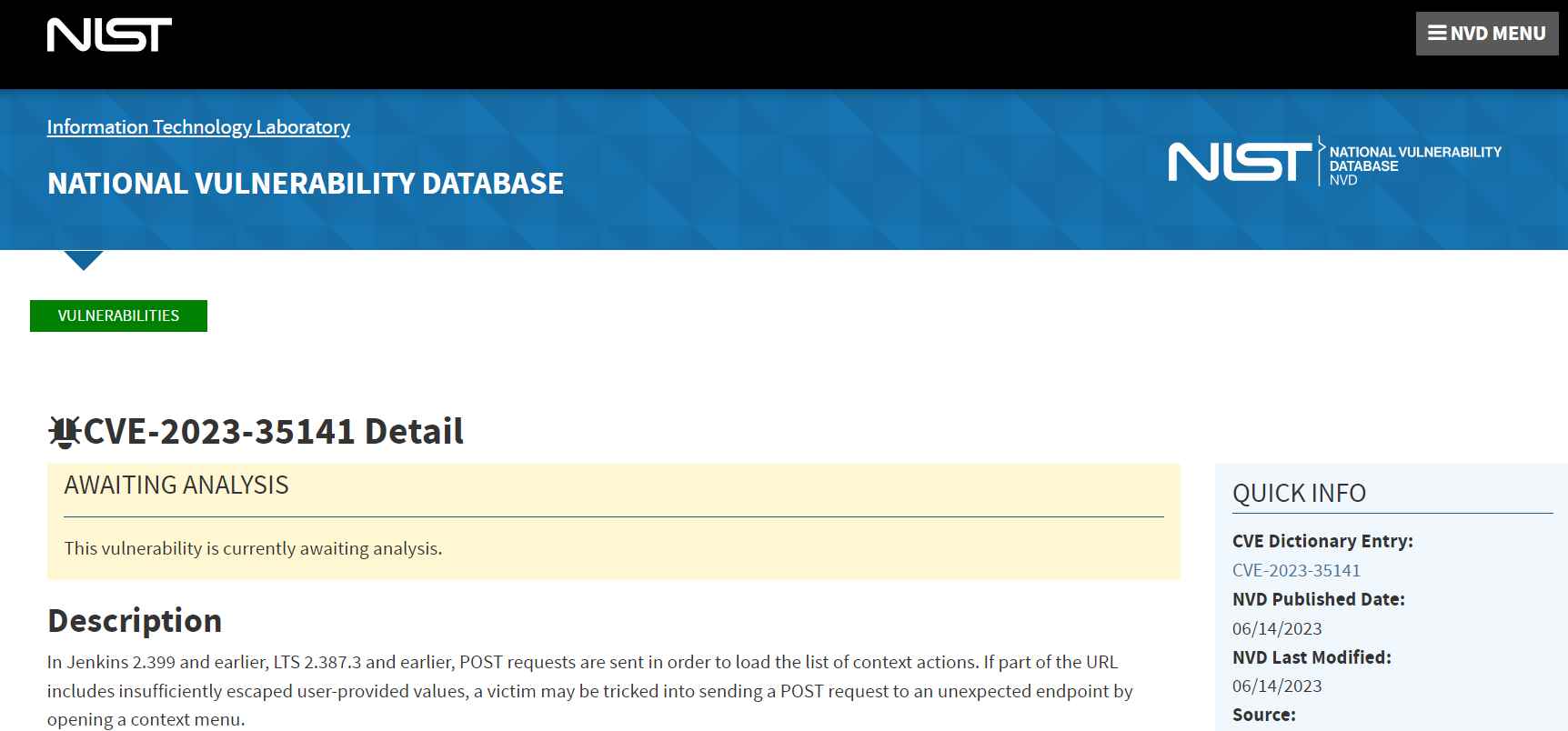
Because of a flaw in the way CSRF (Cross-Site Request Forgery) security is bypassed, a vulnerability known as CVE-2023-35141 has emerged from the shadows. This vulnerability has been given a value of 8.0 on the Common Vulnerability Scoring System, which indicates a very high risk. POST requests are the method of choice for loading the list of context actions in Jenkins versions 2.399 and before, as well as in LTS versions 2.387.3 and prior. An unsuspecting victim might be duped into submitting a POST request to an undesired endpoint, such as the Script Console, merely by opening a context menu if a portion of the URL contains user-provided data that have not been adequately escaped.
As of the time this warning was published, the engineers working on Jenkins are fully aware that the context menu URLs for label expressions do not appropriately have their characters escaped. This vulnerability may be exploited by attackers who have the Item/Configure rights, which presents a significant threat to the application’s security. This is a scary truth that must be faced. The Jenkins development team has been putting forth a lot of effort to patch up this security flaw. The issue has been resolved, and the patch can be found in Jenkins 2.400 and LTS 2.401.1. These versions now transmit GET requests in order to load the list of context actions, which successfully mitigates the dangers that were presented by the CSRF protection bypass issue.
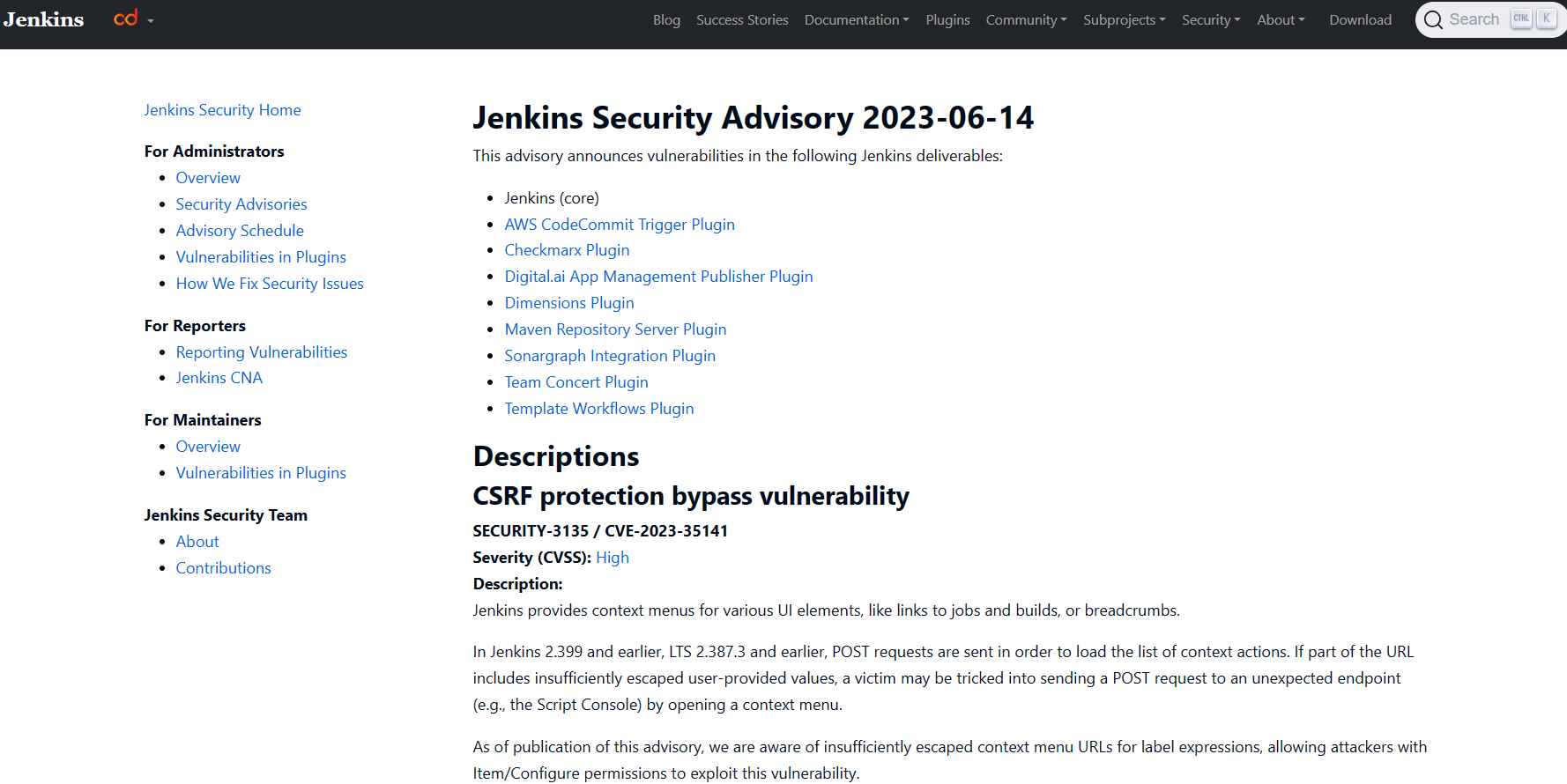
In addition to addressing this vulnerability, the most recent versions of Jenkins also include a fix for six other security flaws that were discovered inside its plugins. This not only indicates the alertness of the creators, but also their dedication to guaranteeing the safety of the product. It is highly recommended that users of Jenkins upgrade their Jenkins software to either version 2.400 or LTS 2.401.1 as the best course of action.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
