Essential Addons for Elementor, one of the most popular plugins for WordPress’s Elementor editor, has been found to have a serious security flaw that has been brought to light. On websites that are vulnerable to the vulnerability, which has been given the number CVE-2023-32243, it is possible for an attacker to get elevated privileges. An experienced security professional has just now made public the exploit code for CVE-2023-32243, which allows an unauthenticated user’s privilege level to be raised to that of any other user on a WordPress website. If the vulnerability is successfully exploited, a threat actor may be able to reset the password of any user, provided that they are aware of the user’s username. This would need the threat actor to have access to the user’s username. It is suspected that this flaw has been present since at least version 5.4.0.
A configuration error exists in the way that Essential Addons for Elementor handles authentication, and this is the root cause of the vulnerability. This vulnerability may be exploited by the attacker by submitting a specially crafted request to the plugin’s application programming interface (API). After the vulnerability has been exploited, the attacker will be able to run arbitrary PHP code on the website that is vulnerable, which may give them total control of the website.
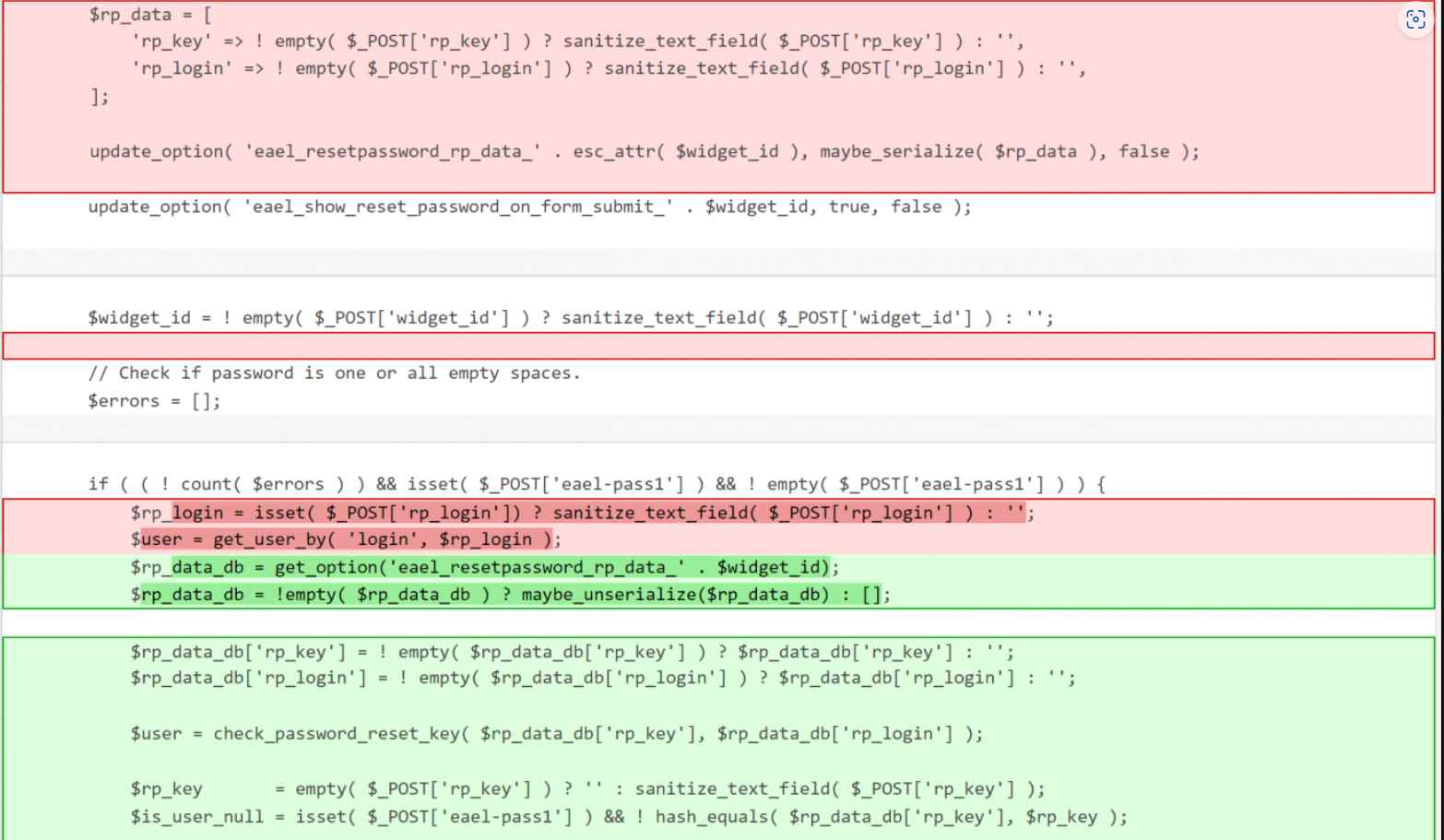
Patchstack researcher Rafie Muhammad notes in its study that the attacker has to specify a random value in the POST ‘page_id’ and ‘widget_id’ inputs so that the plugin does not issue an error message that might raise suspicion on the website admin. In other words, the attacker needs to hide their tracks.
To verify the password reset request and establish a new password on the ‘eael-pass1’ and ‘eael-pass2’ parameters, the attacker must also give the right nonce value on the ‘eael-resetpassword-nonce’ parameter. This is done by using the ‘eael-resetpassword-nonce’ parameter.
Essential Addons for Elementor version 5.7.2, which was made available for download on May 11, 2023, includes a patch that closes the security hole. All WordPress site administrators who are using the Essential Addons for Elementor plugin are strongly encouraged to upgrade it as soon as humanly feasible.
Follow these steps to ensure that your Essential Addons for Elementor are always up to date:
Launch your browser and log in to your WordPress dashboard.
Proceed to the page that lists Plugins.
To see the installed plugins, choose the “Installed Plugins” tab.
Look for “Essential Addons for Elementor” in a search engine.
To immediately update the plugin, select it and then click the “Update Now” button.
To confirm the update, click the “Update” button on the toolbar.
What to do in the event that you are unable to keep Essential Addons for Elementor up to date
In the event that you are unable to keep Essential Addons for Elementor up to date, you may take the following precautions to reduce the possibility of being exploited:
Disable Essential Addons for Elementor.
Install a security plugin that will prevent efforts to exploit vulnerabilities.
Keep an eye out for any indications that your site has been compromised.
WordPress websites are exposed to a significant risk due to a security flaw in a plugin called Essential Addons for Elementor. All WordPress site administrators who are using the Essential Addons for Elementor plugin are strongly encouraged to upgrade it as soon as humanly feasible. In the event that you are unable to install the latest version of the plugin, you may reduce the potential for exploits by following the instructions mentioned above.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
