A SpiderLabs researcher has published an analysis of WinZip 24 network communications in which he detected the sending of update verification requests in unencrypted HTTP format. This could allow threat actors to abuse this update process in order to send malware to compromised devices.
The following is a WireShark screenshot of the update request:
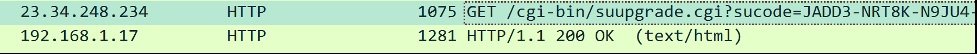
Because HTTP is a non encrypted text format, any user with access to that traffic would be able to intercept, manipulate, and even hijack it.
In other words, anyone on the same network as the user running a vulnerable version of WinZip could use some attack variant such as DNS poisoning to trick the application into installing a malicious update. As a result, the target user could inadvertently throw arbitrary code into their system.
The vulnerable application could also expose sensitive information (registered user name, registration code and other data in the query string) to hackers, as it is a non encrypted channel.
The problems do not end there, as the researcher also discovered that WinZip 24 opens pop-ups when executed in test mode. Because the content of these sales is HTM with JavaScript, malicious hackers can manipulate this content and execute arbitrary code.
The following is an example of pop-ups in WinZip 24:

How to mitigate the exploitation risk?
The reports were revealed through SpiderLabs’ responsible disclosure program. WinZip users can prevent these risks by upgrading to the latest version of this tool (WinZip v25). It should be remembered that this process has a cost that must be covered at the time of the update is installed.
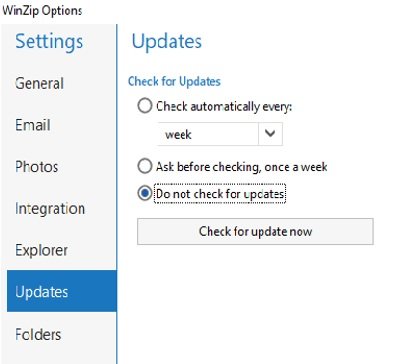
This version uses HTTPS correctly, so it is not vulnerable to such attacks. Users who do not wish to upgrade to version 25 must manually check the available mitigation methods.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
