Cryptocurrency related frauds increased alongside the growing interest on this activity and can affect even experimented users. That’s exactly what happened to Diego Romero, a digital asset enthusiast with a couple years trading in traditional platforms; a few weeks ago he gave a chance to a peer-to-peer (P2P) exchange that turned to be a complex scam.
A P2P exchange platform allows users to trade directly between themselves with no intermediaries, besides allowing them to choose the payment method (PayPal, M-Pesa or even cash). Romero invested $100,000 USD in a P2P platform and now he has no idea of where his money could be.
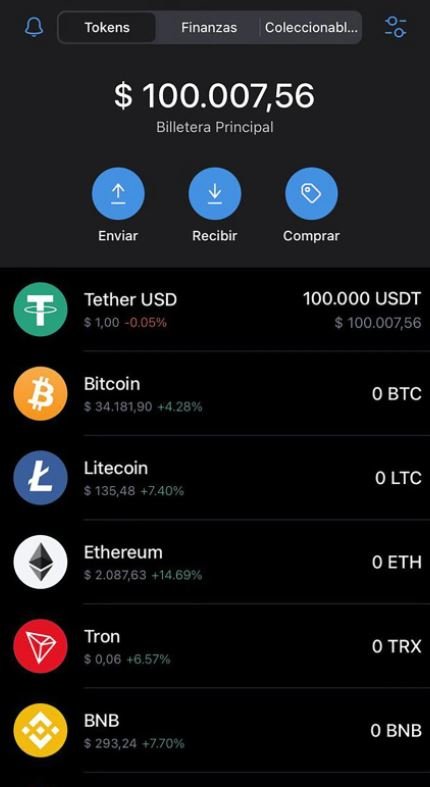
“I had never invested with a P2P broker. They got my attention by offering everything at zero cost. I gave my money to the broker and he gave me $100,000 USDT, the mother cryptocurrency that allows buying Bitcoin, Ethereum and other virtual asset options”, Romero mentioned.
Apparently, the broker told him that P2P transactions required a certain digital wallet: “He told me that I couldn’t use my Binance virtual wallet and I had to mandatory download one called Trust Wallet. That is a lie because both work on the same network and work the same way.” The broker then asked Romero to lend him his phone to scan a QR code and start the cryptocurrency transfer.
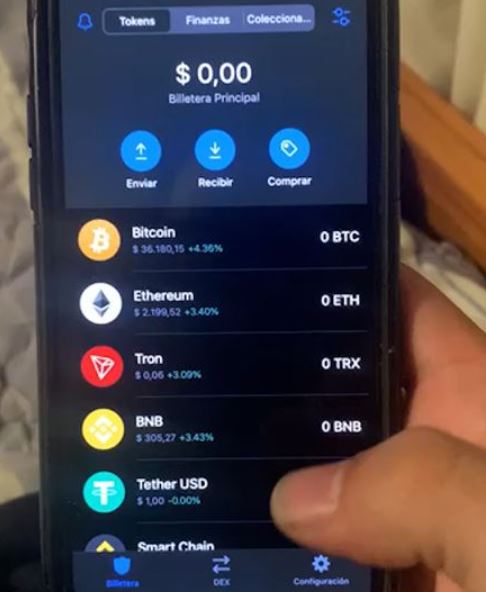
“When I left the place of our meeting he used this information to get into my virtual wallet and cash out all of my resources”, the victim assures.
About the supposed broker, he offers his services via a Linkedin profile, where he calls himself a “freelance cryptocurrency trader” working since 2017. The fraudster also assures he had worked as a hardware and software developer for several tech firms.
“He deceives his customers arguing that he works closely with Argentinian fintech Lemon Cash and is very active on LinkedIn. Me and my friends are trying to spread the voice about this criminal, thus preventing more people become victims of this fraud”, Romero concludes.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
