ETH Zurich cybersecurity experts report finding a new cyberattack variant that would allow threat actors to trick point of sale (POS) terminals and make them transact with Mastercard cards as if they were Visa cards. This attack would be based on a PIN evasion condition, which allows hackers to abuse stolen Visa cards to make purchases in high quantities without using the victim’s PIN.
Although in the description of the attack this situation could be taken as a simple confusion of payment operators, experts claim that the consequences of an attack would be disastrous: “Cybercriminals could use this attack in conjunction with other variants of Visa attack to abuse Mastercard cards, which operate with ‘contactless’ technology,” the report states.
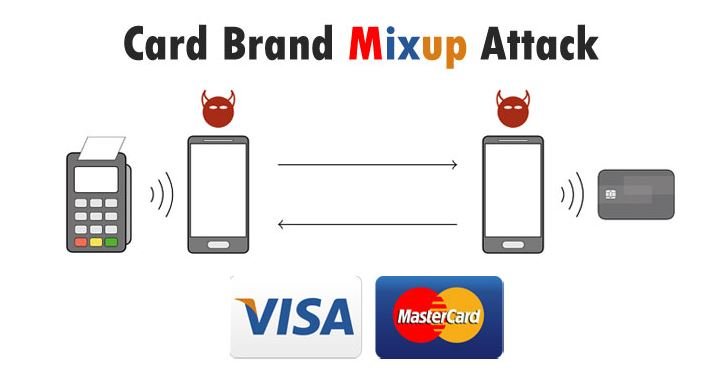
Experts note that this attack involves exploiting serious vulnerabilities in the contactless protocol of Mastercards: “Broadly speaking, this is made possible by the use of malicious Android apps to deploy a Man-in-The-Middle (MiTM) condition on a retransmission process, allowing this app to initiate communication between the terminal and the card, as well as intercept NFC communications and cause a mismatch between the two systems.”
In other words, making a payment using Visa or Mastercard requires an authorization request, which is sent to the corresponding payment network. The POS terminal recognizes the card brand thanks to a key generated by the combination of the card number and a card type identifier; eventually this information activates a single kernel for the transaction in question. It should be noted that an EMV kernel is a set of functions that provide the logic required for the processing of contactless transactions.
In this attack, hackers take advantage of the non-authenticated identifiers used in the process in the POS terminal, allowing the system to be tricked into activating a faulty kernel: “This simultaneously performs a Visa transaction on the POS terminal and a Mastercard transaction with the card”, experts add.
All of this may sound complex and dangerous, although it should also be noted that a successful attack requires some prerequisites to be met, which undoubtedly hinders its active exploitation. The risk still cannot be dismissed as such an attack would not require root privileges on the affected systems or exploitation on Android systems for the installation of the malicious app.
In response to this report, Mastercard implemented some network-level security mechanisms, which in theory should completely eliminate the possibility of these attacks being presented in real-world scenarios.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
