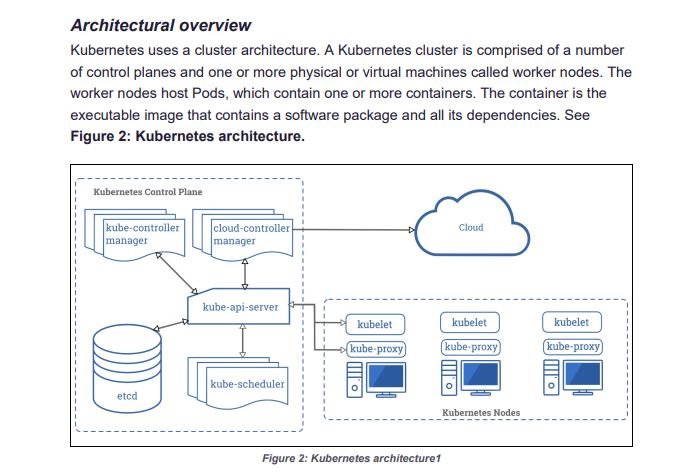
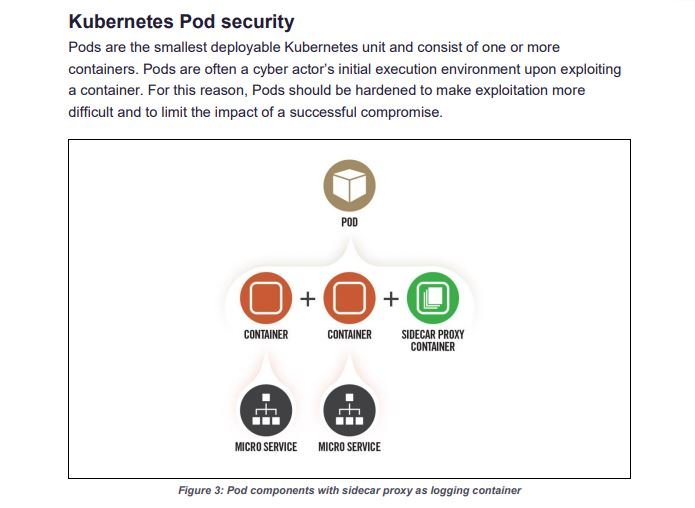
A recent report from the Cybersecurity and Infrastructure Security Agency (CISA) points to the detection of multiple errors that allow the deployment of denial of service (DoS) attacks, theft of sensitive information and cryptojacking in deployments of Kubernetes, the open source container system for deploying applications in the cloud.
These systems are compromised by supply chain attacks, deployed by threat actors and even by internal malicious users. The notice was issued by CISA and investigators from the National Security Agency (NSA).

In the alert, the agencies point out some of the security risks associated with Kubernetes deployments, as well as share some tips for administrators and developers to create a better security environment.
This set of measures applies to both public agencies and private organizations, says a statement from the Department of Defense, the Defense Industrial Base and Homeland Security Systems.
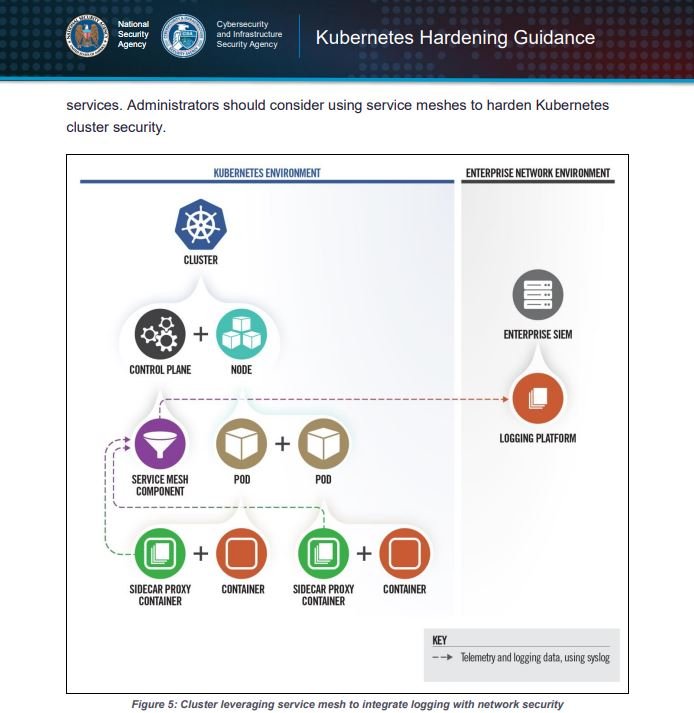
Recommended security measures include constant scanning of containers for any exploitable security flaws, restricting privileges to users, isolating specific networks, installing firewall solutions, and implementing authentication mechanisms reliable enough to mitigate the most common attacks.
In addition, CISA and NSA recommend that administrators follow the guidance provided and keep their systems updated to the latest versions available. The full report on these Kubernetes flaws is available on the official CISA website.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.