A new report from the most important cybersecurity agencies in the West includes a list of the 30 vulnerabilities most exploited by state hacking groups throughout 2020. This report was prepared in collaboration with the U.S. Cybersecurity and Infrastructure Security Agency (CISA).
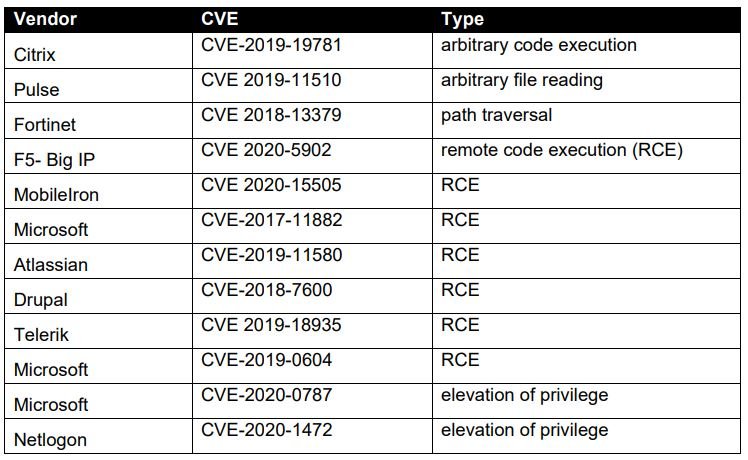
The list is headed by CVE-2019-19781, described as an arbitrary code execution vulnerability in Citrix Application Delivery Controller. Despite the fact that the vulnerability has already been addressed, incidents of exploitation continue to be detected.
Unsurprisingly, the second, third, and fourth place is filled by flaws in Pulse Secure VPN, Fortinet, and F5 Big IP, which frequently make headlines on news websites dedicated to the cybersecurity community. Like the first place on the list, these flaws are still frequently exploited even though security patches have already been released for their correction.
In this regard, the director of operations of the United Kingdom National Cyber Security Centre (UK NCSC) Paul Chichester said: “Our commitment is to work with our partners to raise awareness about the main cybersecurity risks worldwide, which will allow organizations to correctly address these errors.”
Although vpn vulnerability abuse is a very conventional attack, there are other methods of entry to vulnerable systems, including exploiting flaws that allow privilege escalation and remote code execution errors. These attacks were abused by Chinese hackers to compromise business networks in Australia.
On the other hand, experts believe that 2021 will end up being an equally complicated year in terms of cybersecurity. During the first months of the year, state threat actors have focused on the abuse of flaws in Microsoft Exchange, vulnerabilities in Pulse Secure and in the Accellion FTA file sharing platform. Other products affected by state hackers and cybercriminal groups are Qualys security solutions, vCenter products and other similar solutions.
The agencies that produced the report also gave some advice for system administrators to mitigate the risk of exploitation.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
