Cybersecurity experts report that, despite efforts to take it down, the MyKings botnet is still active and generating an incredible amount of money for its operators nearly five years after it was first detected. In addition, traders continue to resort to all sorts of tricks, including the use of bootkits, cryptojackers and other malicious tools.
Over the past few months, an Avast security team has monitored MyKings-related activity, detecting more than 140,000 attacks operated by this malicious infrastructure, mainly in India, Russia, and Pakistan.
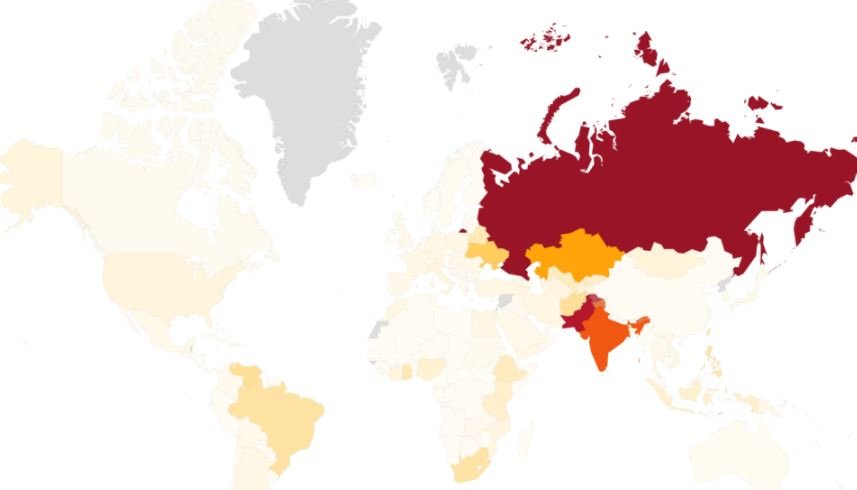
The researchers also managed to find the cryptocurrency addresses associated with MyKings, which they show accumulate digital assets totaling $24.7 million USD. This is not all the capital at the disposal of hackers, as it is estimated that MyKings has more than 20 cryptocurrency addresses under its control.
The analysis only made it possible to find some of the e-wallets and their balances, as threat actors use encryption-based protection, which prevents activities such as mining and analysis.
Another notable feature of this botnet is a new monetization technique, which involves the abuse of the video game sales platform Steam. Using a URL manipulation tool, MyKing operators can hijack monetary transactions on this platform, replacing commercial URLs with malicious addresses, allowing the theft and resale of expensive items for popular video games.
Hackers can also manipulate URLs from the Russian search engine Yandex, allowing them to redirect victims to RAR or ZIP files that supposedly contain photos, but actually deliver a copy of the MyKings malware to the affected systems.
The last time a thorough analysis of MyKings was done was in 2018, when experts discovered that the botnet had nearly 500,000 infected devices. Apparently, MyKings continues to grow at a sustained pace, allowing threat actors to give it careful maintenance while being able to fund other hacking campaigns, so it is critical to gradually disrupt their operations.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
