Let’s Encrypt is currently the most important certification authority for Transport Layer Security (TLS) encryption thanks to its sophisticated automated processes for validating, signing, installing and renewing certificates for secure websites.
Recently, cybersecurity specialists have started pointing out that, in September 2021, the root certificate that Let’s Encrypt currently uses will expire, which has generated multiple doubts and concerns in the cybersecurity community. In this regard, researcher Scott Helme prepared a report that includes everything you need to know about this certificate, known as IdentTrust DST Root CA X3.
According to the expert, all certificates that power HTTPS on the Internet are issued by a Certificate Authority (CA), a term that refers to a trusted entity recognized by its device or operating system. Below is the list of “Trusted Root Certificate Authorities” on Windows 10 systems, one of the most widely used computing implementations in the world:
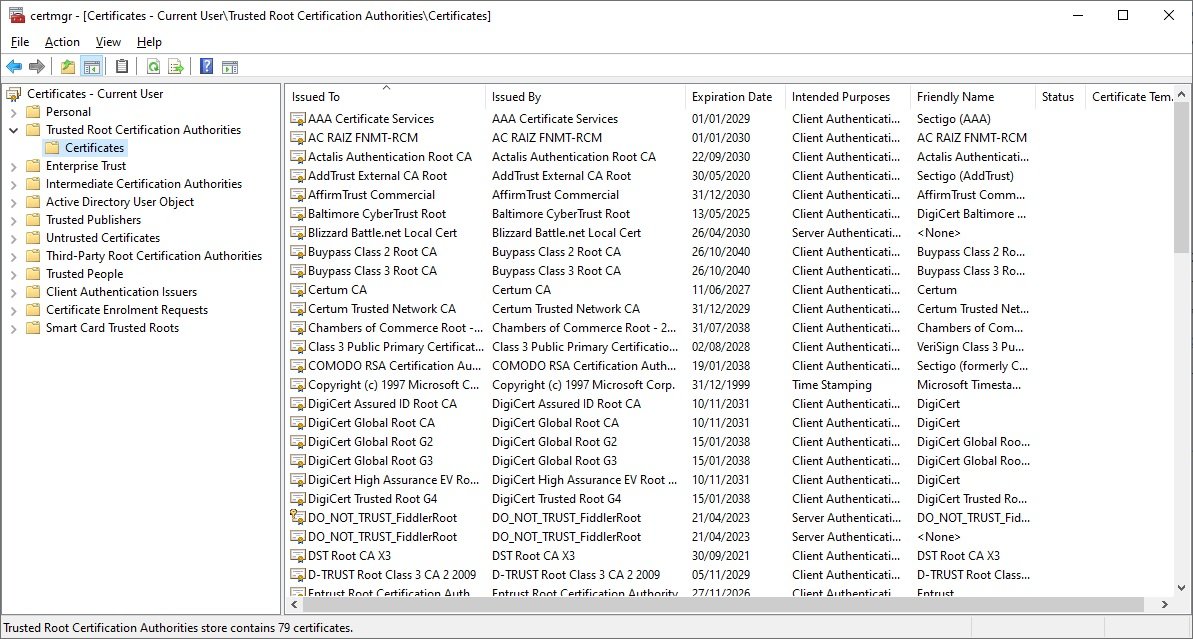
The manufacturer includes these certificates along with the operating system and they receive patches and maintenance as part of the same operating system update process. It is here that we can find IdenTrust DST Root CA X3, with the potential to generate problems in the near future.
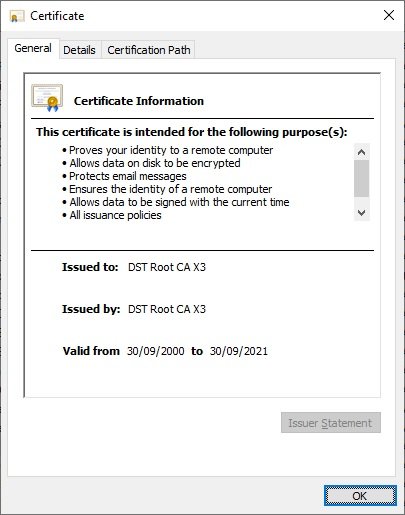
By verifying the information of the certificate, we can see that it will no longer be valid on September 30, 2021, a period of time that the researcher identified as “notAfter”.
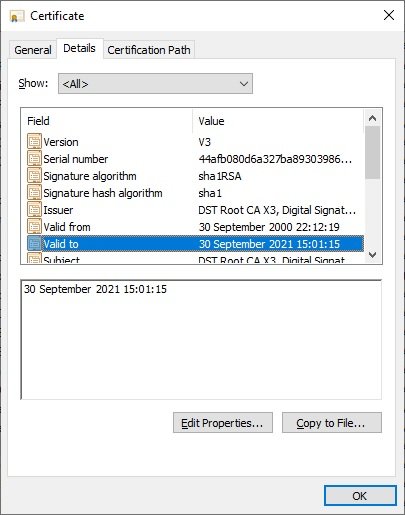
When this certificate expires, customers (including millions of websites) will no longer trust the certificates issued by this CA, which could create all sorts of inconveniences for organizations, developers, and users.
The problem grows due to the remarkable growth that Let’s Encrypt has experienced during the last years, reaching up to 2 billion certificates issued at the beginning of 2021; it is thanks to this CA that much of the known Internet works, so even the slightest problem in IdentTrust DST Root CA X3 could have disastrous consequences.
The expert adds that this does not have to do with Let’s Encrypt practices and policies, but is related to the way in which technological implementations receive updates.
It is important to mention that it is not yet clear the magnitude of the problems that the expiration of this certificate could cause, although it is mentioned that the incident could be worse than what happened in the expiration of AddTrust, which expired in May 2020 and caused failures in websites, email clients and applications.
On the potentially affected customers, the expert drew up a list of organizations that will most likely experience failures when IdenTrust DST Root CA X3 expires:
- OpenSSL, version 1.0.2 and earlier
- Windows XP SP3 and earlier
- macOS v10.12.1 and earlier
- iOS 10 and earlier (iPhone 5 is the oldest model capable of operating iOS 10)
- Android v7.1.1 and earlier (v2.3.6 will be able to work if the ISRG Root X1 cross sign is provided)
- Mozilla Firefox pre-v50
- Ubuntu v16.04 and earlier
- Debian 8 and earlier
- Java 8 v8u141 and earlier
- Java 7 v7u151 and earlier
- NSS v3.26 and earlier
- Amazon FireOS (Silk web browser)
Helme mentions that other platforms listed below could experience crashes, although the detection of potential errors has not yet been confirmed:
- Cyanogen v10 and earlier
- Jolla Sailfish OS v1.1.2.16 and earlier
- Kindle v3.4.1 and earlier
- Blackberry v10.3.3 and earlier
- PlayStation 4 with firmware v5.00 and earlier
- IIS
As the researcher mentions, there is still a lack of research on the potential risk that the expiration of the certificate could have; nonetheless, he also ensures that the risk should not be dismissed nor should all responsibility be left to Let’s Encrypt.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
