Specialists from an Iranian security firm report the discovery of a one-of-a-kind rootkit hidden within the firmware of HP Integrated Lights-Out (HP iLO) devices, abused in the wild to erase the servers of the target organizations. Identified as iLOBleed, this rootkit was discovered by researchers at Tehran-based Amnpardaz and revealed in a report published this week.
Experts mention that iLOBleed specifically targets HP iLO devices, implementations that can be added to servers or workstations as add-on boards. These computers include their own processor drive, storage space, and a network card, all running independently of the local operating system.
The main functions of these devices include connecting to remote systems, deploying maintenance and upgrade operations, and other tasks. Its inherent characteristics have made this one of the most widely used business products today.
The Amnpardaz report notes that, since 2020, multiple incidents have been detected in which a threat actor managed to compromise enterprise networks by hiding inside iLO devices as a way to survive operating system reinstallations and maintain persistence within vulnerable networks.
To avoid detection, attackers disguise the iLOBleed rootkit as a module for the iLO firmware, in addition to creating a user interface for a fake system update: “The malware simulates the update process, although it has difficulty displaying versions of this fake update in the iLO web UI and elsewhere, but there is a problem,” the experts say.
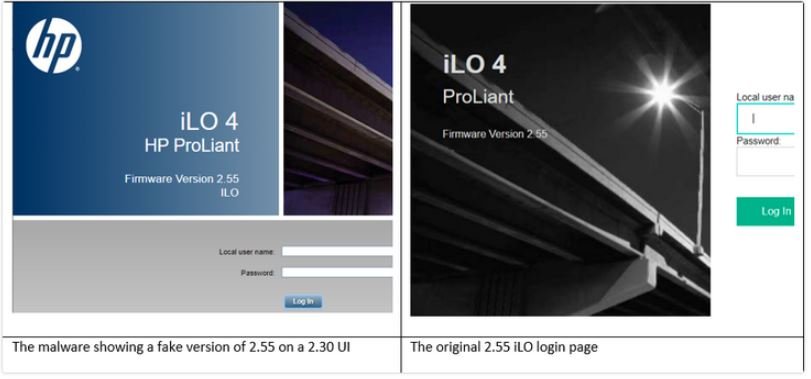
Even though the rootkit provides full control of the infected hosts, the hackers behind this campaign seem to have used it only to erase the data on the compromised systems, also eliminating any trace of the attackers. The attack is able to replicate the data erasure process an indeterminate number of times.
Experts consider this rootkit as a highly sophisticated work and potentially developed by advanced hackers. Although the identity of the threat actors behind this campaign is not known, Amnpardaz researchers do not hesitate to label the attackers as an advanced persistent threat (APT) group.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
