A group of threat actors sponsored by the Chinese government has begun deploying a phishing campaign using malware capable of intercepting classified information about diplomatic missions from countries around the world and even the Vatican. Hackers, identified as TA416, are using an updated version of the PlugX Remote Access Trojan, which has been rewritten using the Golang programming language.
This hacking group, also known as Mustang Panda or RedDelta, has attacked multiple diplomats and organizations around the world that have some connection with the Chinese government. Last July, a group of experts reported that China had deployed a hacking campaign against the Vatican and organizations in the United States, Africa and Asia.
Experts at security firm Proofpoint say TA416 updated its version of PlugX by rewriting part of it in Golang. Other hacking groups have used their own versions of this malware in previous campaigns, demonstrating its versatility.
Although experts were unable to identify the initial attack vector, they discovered that hackers have resorted to using built-in malicious emails from services such as Google Drive and Dropbox in order to deploy the infection.
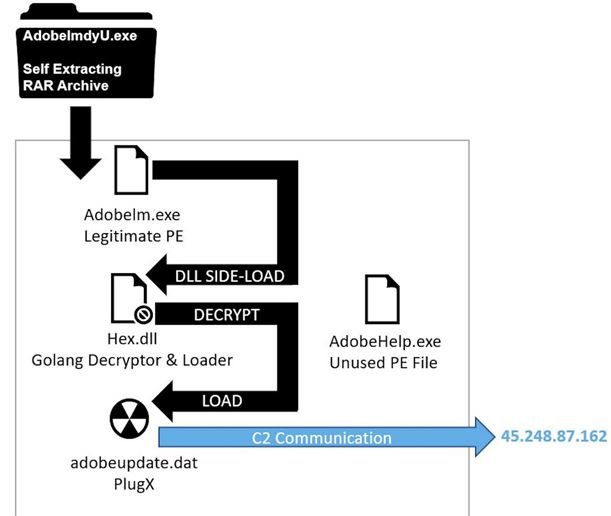
In recently detected attacks, cybercriminals have used two RAR compression files in order to hide the malware. If these files are downloaded by the victims, four files will be opened inside the host devices in order to install the PlugX Trojan. Experts also found C&C servers for shared IP addresses discovered in other campaigns associated with hackers.
Most of the phishing emails from the last campaign appear to have been sent between September 16 and October 10. These messages use social engineering lures, as a reference to a renewed interim agreement announced in September between the Vatican Holy See and the Chinese Communist Party, as a way to lure a victim into opening the malicious message.
“We see a forged email header in fields that seem to mimic Union of Catholic Asia News journalists,” the specialists add. “This confluence of social engineering thematic content suggests an ongoing focus on issues related to the evolving relationship between the Catholic Church and the Chinese Communist Party.”
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
