Although advances in cryptography are continuous and considerable, researchers are always working on developing methods to decipher even the most advanced technologies. This time, ethical hacking specialists from the International Institute of Cyber Security (IICS) will show you how to use Ciphey, a fully automated decryption tool.
Ciphey uses a deep neural network with a simple filtering system to determine the type of encryption used. It then uses a custom language verification interface for natural language processing that can detect when a given text is already decrypted.
FEATURES
According to ethical hacking specialists, Ciphey’s main features include:
- Supports more than 50 encryption variants such as binary, Morse and Base64, plus classic ciphers like Caesar, Affine encryption, Wigener encryption and modern encryption like the XOR key, among others
- Artificial intelligence specially created for augmented search (AuSearch), which will determine the encryption used. This process takes no more than 5 seconds
- Ciphey’s specially constructed natural language processing module can determine whether a entered text has already been decrypted or not, whether the text is JSON, CTF or simple English, Ciphey will yield results in a matter of milliseconds
- Multilingual support for German and English (United States, United Kingdom, Australia)
- Incredibly fast C++ core
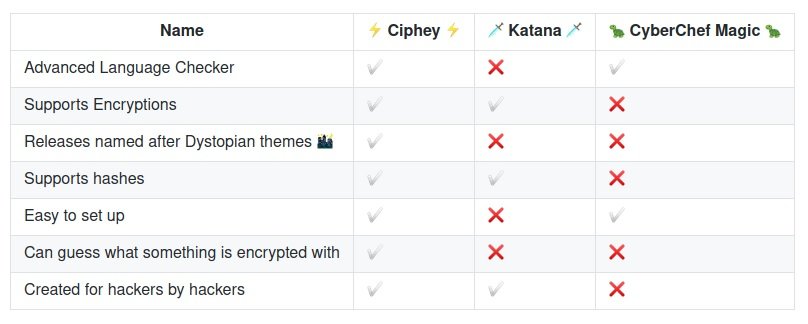
COMPARATIVE TABLE: CIPHEY – KATANA – CYBERCHEF MAGIG
INSTALLATION
pip3 install -U ciphey
USAGE
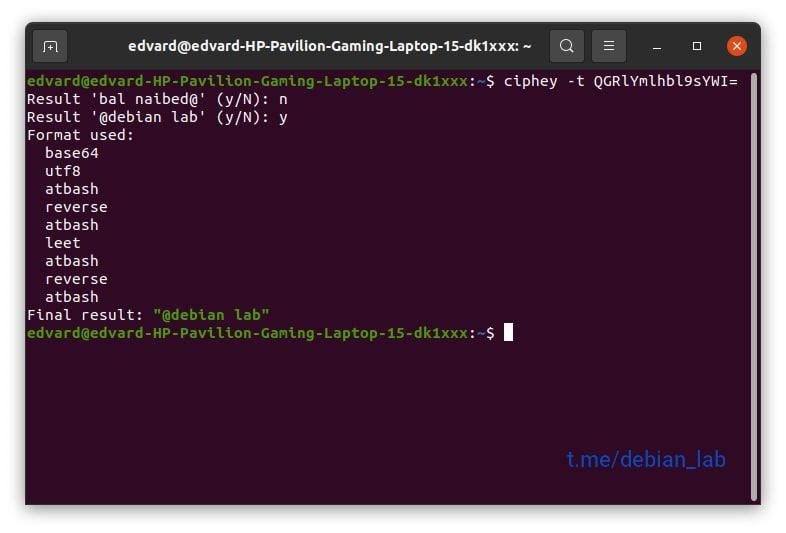
ciphey [options]
-t <encrypted text>, --text <encrypted text>
In this section you insert the encrypted text for which we want to decrypt, as mentioned by experts in ethical hacking.
CONCLUSIONS
Ciphey is a new and modern text decryption utility that supports a lot of encryption types and should be used if you have encrypted text and do not know how to decrypt it, mentioned by ethical hacking experts. To learn more about cybersecurity risks, malware variants, vulnerabilities, ethical hacking and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
