According to a recent cybersecurity report, the operators of a new botnet known as DreamBus are looking for the minimal application flaws for Linux servers in order to compromise the affected devices and integrate them into this malicious development. As you may remember, the term botnet refers to a set or network of devices (bots) running autonomously and automatically. Botnet operators can control all infected devices or servers remotely.
The report, published by researchers from security firm Zscaler, mentions that this threat was recently detected and has been identified as a variant of SystemdMiner, a botnet tracked in multiple attacks in early 2019. Experts mention that newer versions of DreamBus have significant improvements over the latest SystemdMiner-related reports.
DreamBus operators have targeted some enterprise-level applications running on Linux systems, including PostgreSQL, Redis, Hadoop YARN, Apache Spark, SSH service, and more. Attackers appear to primarily use brute force attacks, proving highly effective against systems with default administrator credentials; attackers also exploit known unmediated vulnerabilities.
In this way attackers obtain an access point to compromised Linux servers, from where they can install mining software to extract Monero from the affected systems, an attack known as “cryptojacking”. Each of the infected servers is then used as a DreamBus bot to launch brute force attacks against other possible targets.
Researchers also mention that DreamBus employs multiple security measures to prevent detection, for example, by having all infected systems communicate with the malicious C&C server through the DNS-over-HTTPS (DoH) protocol. It should be noted that DoH-compatible malware variants are very little used given the difficulty in their configuration. To prevent the C&C server from crashing, threat actors hosted it on the Tor network, suggesting that the botnet is operated through servers in Russia and Eastern Europe.
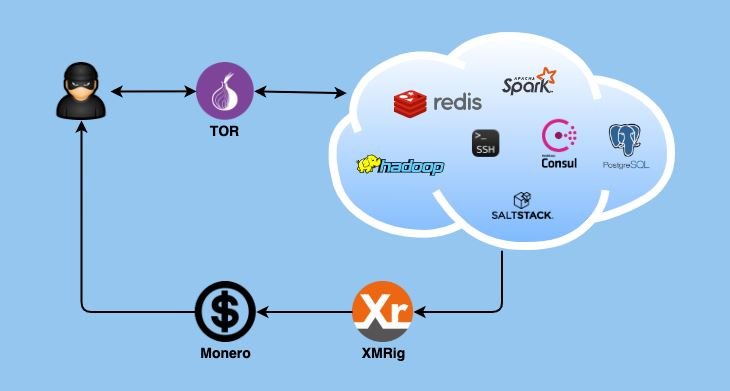
The security report strongly asks target organizations to assess this security risk seriously, as operators could start using more dangerous payloads at any time.
For more information on vulnerabilities, exploits, malware variants, cybersecurity risks and information security courses, feel free to access the International Cyber Security Institute (IICS) website.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
