A couple of months ago, CloudSEK researchers identified a new and unusual strain of ransomware. Dubbed GoodWill, this new variant of encryption malware appears to pursue very different targets than other cybercriminal operations.
According to the report, the operators of the GoodWill ransomware seek to have their victims perform charity work instead of paying a ransom, showing an exceptional commitment to social causes.
Their focus on charity doesn’t mean this is a less dangerous ransomware variant than others; according to experts’ samples, this malware can evade dynamic analysis and exploit the function AES_Encrypt to encrypt infected files using the AES algorithm.
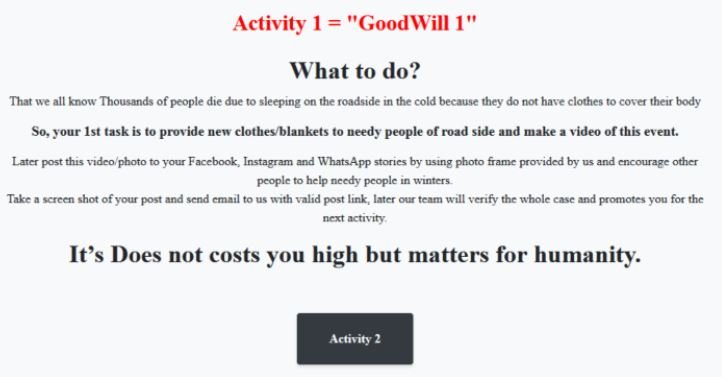
Upon completion of the infection, the ransomware encrypts documents, photos, videos, databases, and other essential files on the target system. When the ransom note appears, victims are suggested to perform three actions to access the decryption keys:
- Donate new clothes to the homeless, record the action in photos or videos and post it on social media
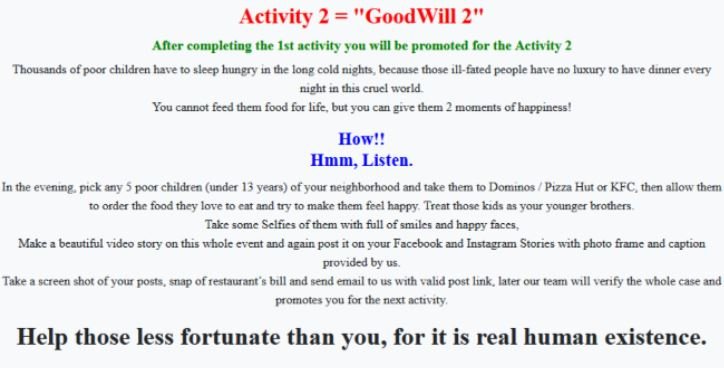
- Take five children in poverty to Dominos, Pizza Hut or KFC; the victim must also take evidence of this
- Financially help anyone who needs urgent medical care but can’t afford it
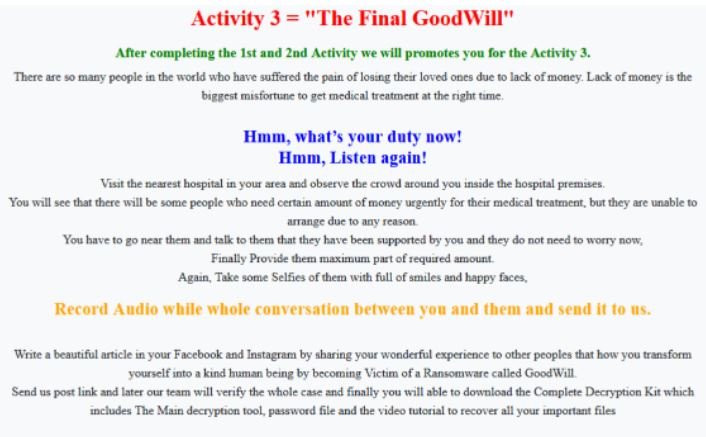
GoodWill operators mention that, after checking the evidence submitted by the victims, they will proceed to share a decryption kit, which includes the primary tool, the corresponding keys and a video with the instructions to complete the recovery process.
On the origin of the ransomware, the researchers made interesting findings by analyzing the chains. For example, the string “error hai bhaiya” is written using Hindi and English, indicating that the developers are of Indian origin.

Another string identified as “.gdwill” indicates that the extension used in infected files is .gdwill.

CloudSEK also identified the following network artifacts associated with GoodWill. These are ransomware tunnels that are also subdomains of Ngrok.io:
- http://9855-13-235-50-147(.)ngrok(.)io/ (panel de control de GoodWill)
- http://9855-13-235-50-147(.)ngrok(.)io/alertmsg(.)zip
- http://9855-13-235-50-147(.)ngrok(.)io/handshake(.)php
- http://84a2-3-109-48-136(.)ngrok(.)io/kit(.)zip
Two IP addresses (3.109.48.136 and 13.235.50.147) used as subdomains were extracted from these artifacts. These addresses are located in Mumbai, India.
There is not much information about successful attacks and the effectiveness of decryption tools delivered by hackers, although this could change if GoodWill operators manage to infect more targets.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
