A recent security report mentions that the threat actor identified as Guildma has developed new features thinking of attacking new targets with multiple hacking variants. Ghimob, its latest creation, targets mobile banking applications, cryptocurrency exchange platforms and other technological developments in Germany, Portugal and some sectors of Latin America.
Kaspersky security specialists mention that Ghimob is powerful malware with which threat actors could access remotely compromised devices in order to complete financial transactions using victims’ devices, so the security systems of banking or cryptocurrency platforms could not detect malicious activity.
“When hackers manage to access the compromised device, they can enable an overlay black screen or open a browser window so that the user cannot see the arbitrary actions that criminals take on their financial platforms,” the report by specialists mentions.
One thing that has caught the eye of Ghimob is its use of Cloudflare-protected backed C&C, hiding your real C&C with DGA and other methods. Moreover, although it does not seem to work as malware-as-a-service (MaaS), Ghimob has much more advanced features than similar malware variants like BRATA or Basbanke.
About their infection method, Kaspersky experts mention that threat actors use malicious URLs to infect Windows and Android systems. These URLs contain the Ghimob installer depending on the target system. On Android, the downloaded APK is passed through the installer of a legitimate application, although it remains to be said that this APK is not downloaded from Google Play. After installation, the application will abuse accessibility mode on the target system to gain persistence, disable its manual uninstallation and allow a banking Trojan to search for sensitive information.
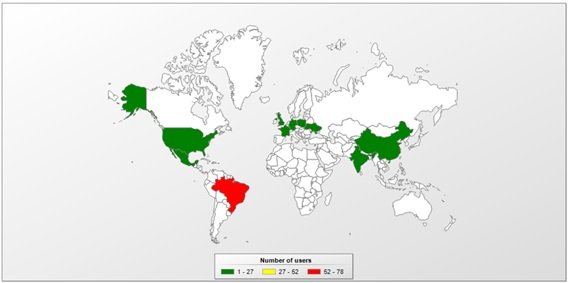
The data collected by Kaspersky shows that a large part of the victims of this attack reside in Brazil, although it is not the only place where malicious activity related to Ghimob has been detected.
To allure potential victims, threat actors write an email as if it were sent by a creditor, while the malicious APK pretends to be Google Defender, Google Docs or any other trusted application.
If the attack is successful, the malware will attempt to detect common emulators, verify the presence of a debugger attached to the process and manifest file, as well as look for a debuggable flag. If any of these are present, the malware is simply removed.
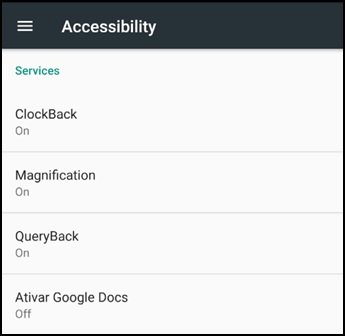
On the other hand, in case of passing the checks the user will find a default Android accessibility window, as the malware depends on this accessibility for its proper functioning.

From the outset experts linked this campaign to Guildma, a well-known banking Trojan first detected in Brazil. Specialists recommend that financial institutions improve their security mechanisms and drive the implementation of anti-fraud technology to prevent attacks by this family of mobile Trojans.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
