In December 2021 a Canadian-based medical services firm was attacked by two ransomware operations employing remarkably different tactics, leaving the affected infrastructure in critical condition. According to the Sophos report, Karma ransomware hackers stole private information without encrypting the affected systems, while the operators of the Conti ransomware did not hesitate to encrypt the compromised systems, regardless of the type of services provided by the affected firm.
Both cases involve the exploitation of the well-known ProxyShell vulnerability set (CVE-2021-34473, CVE-2021-34523 & CVE-2021-31207), affecting Microsoft Exchange Server and used by multiple ransomware groups, including groups affiliated with Conti, which operates as a ransomware-as-a-service (RaaS) platform. However, very few cases of simultaneous ransomware attacks against the same target are known.
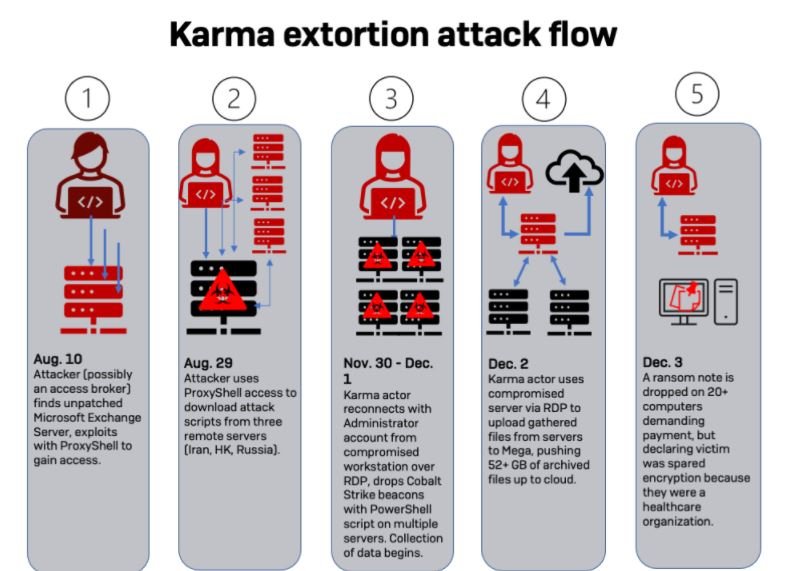
Once they gained the first access to the system, both hacking groups exploited the management shell in Exchange to create an account with administrator privileges from which they retrieved scripts from three remote servers.
A couple of days later, a new series of attacks using ProxyShell were detected on the compromised networks. In this attack, a Web shell was installed on the Exchange Server ISS Server instance. In addition, the first logs of malicious activity indicated that the administrator account created by the hackers was used to access an RDP session in a virtual machine, activity associated with a Karma ransomware attack.
By December 3, employees of the affected company found Karma’s ransom note on about 20 workstations and servers. The ransom note claimed that the data had only been exfiltrated and unencrypted, as Karma was aware that the company provided health services. Although the company was already analyzing the best way to address the attack, the second intrusion was about to be detected.
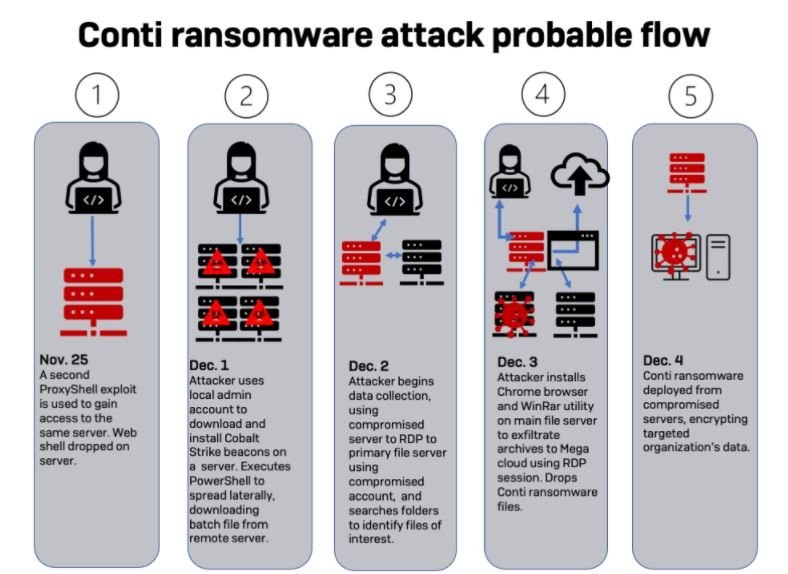
A compromised administrator account managed to install the Chrome browser on the company’s main file server; subsequently, the malware was deployed to one of the organization’s servers. Experts identified the sample as a development of Conti.
Moments after completing the attack, Conti operators disabled Windows Defender and the ransomware began encrypting the files on the system to finally deliver the ransom note.
These attacks represent a severe security risk, as on multiple occasions organizations have been shown to be highly vulnerable to exploitation by these attack vectors. The decisions made by the company are unknown but it is undeniable that a prolonged disruption in its systems could have been disastrous for the health of hundreds of people.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
