FileWave MDM is a multi-platform mobile device management solution that allows IT administrators to manage, monitor, and view all of the company’s devices. MDM supports a wide range of devices, from iOS and Android smartphones, MacOS and Windows tablets, laptops and smart devices such as televisions.
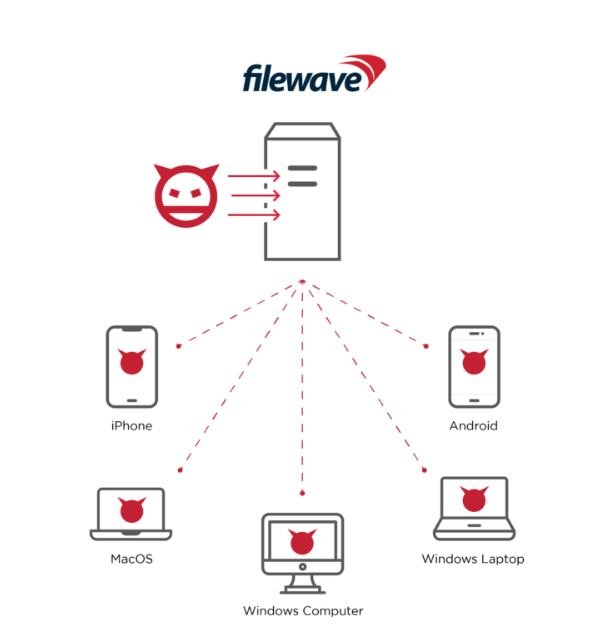
Through MDM, administrators can view and manage device configurations, locations, security settings, push mandatory software and updates to devices, change device settings, lock, and, when necessary, remotely wipe devices. A threat actor who is able to hack the MDM would be in a powerful position to control all devices, allowing the attacker to compromise confidential data such as a device’s serial number, the user’s email address and full name, address, geo-location coordinates, IP address, device PIN codes etc. Furthermore, threat actors could exploit MDM capabilities to install malware or ransomwares or backdoors, and even gain access to the device directly through remote control protocols.
During the research, the experts were able to identify critical vulnerabilities in the authentication process of the FileWave MDM product suite, allowing a hacker to create an exploit that bypasses authentication requirements in the platform and achieve administrator access to the platform. By exploiting this authentication bypass vulnerability, researchers were able to take full control over any internet-connected MDM server. In the research, they discovered more than 1,100 such servers, each containing hundreds of managed devices. Claroty Team82 has disclosed two critical vulnerabilities, CVE-2022-34907 and CVE-2022-34906, in FileWave’s mobile device management (MDM) system. The vulnerabilities are remotely exploitable and enable a threat actor to bypass authentication mechanisms and gain full control over.
- CVE-2022-34907, an authentication bypass flaw exists in FileWave MDM before version 14.6.3 and 14.7.x, prior to 14.7.2.
- CVE-2022-34906, a hard-coded cryptographic key, exists in FileWave MDM prior to version 14.6.3 and 14.7.x, prior to 14.7.2.
In order to showcase this vulnerability and the harm it can cause, the team created a standard FileWave setup, and enrolled 6 devices. Then, using this vulnerability, allowed them to easily attack and infect all internet-accessible instances managed by the FileWave MDM, below, allowing full control of all managed devices, gaining access to users’ personal home networks, organizations’ internal networks, and much more.
Lastly,they installed malicious packages on each controlled device, popping a fake ransomware virus on each of those managed devices.
FileWave patched the vulnerability in version 14.7.2, which it released earlier this month.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
