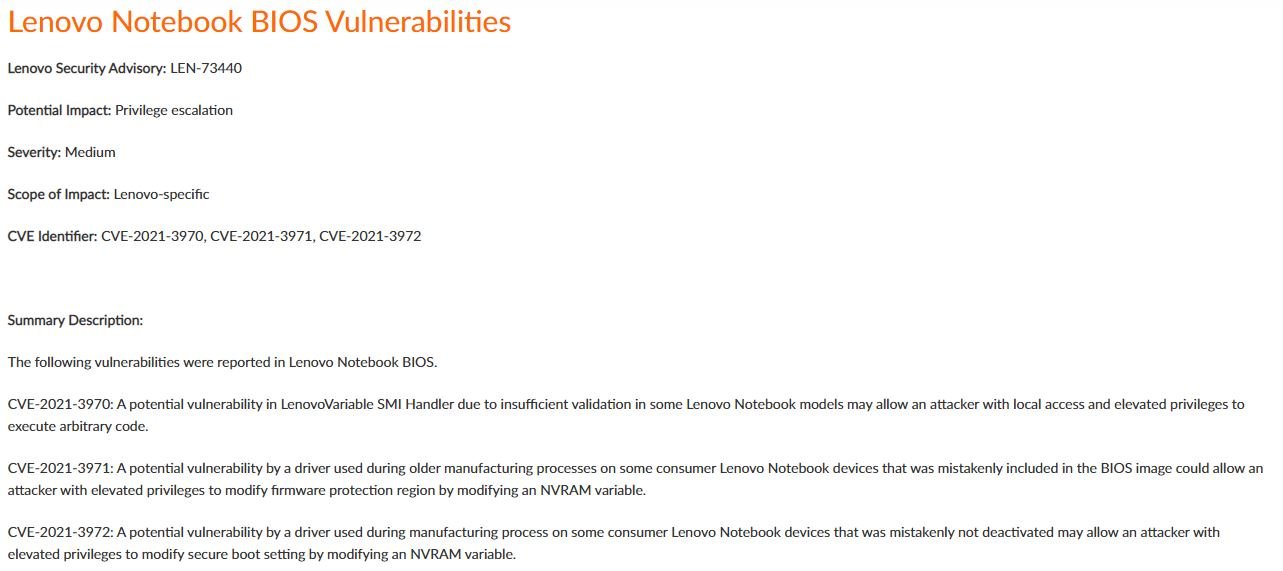
After receiving a report from ESET researcher Martin Smolár, Lenovo security teams announced the correction of three severe vulnerabilities. Tracked as CVE-2021-3970, CVE-2021-3971, and CVE-2021-3972, the flaws could be exploited to execute UEFI malware, either in the form of SPI flash implants like LoJax, or ESP implants like ESPecter.
In UEFI cyberattacks, malicious operations are loaded onto a compromised device at an early stage of the system boot process, so the malware in question is capable of altering configuration data, gaining persistence, and evading security measures that are only loaded at the compromised stage.
In its report, ESET said the flaws affect more than a hundred different models, including IdeaPads, Flex and Yoga laptops and Legion devices, which could impact several million users worldwide. In addition, it is reported that the flaws exist due to the presence of some drivers that were only used during the product development stage.
Tracked as CVE-2021-3970, this is a memory corruption issue that affects the function of the SW SMI driver and is caused by incorrect input validation, allowing attackers to read or write to SMRAM, leading to high-privilege malicious code execution scenarios.
The remaining flaws relate to drivers called SecureBackDoor and SecureBackDoorPeim. Lenovo described the first security flaw as a potential vulnerability of a driver used during older manufacturing processes on some portable devices that was mistakenly included in the BIOS image, allowing threat actors with elevated privileges to modify the firmware protection region by modifying an NVRAM variable.
The second flaw lies in a driver used during the manufacturing process on some Lenovo devices that was left activated by mistake, which would allow threat actors with elevated privileges to modify the secure boot settings.
ESET notified Lenovo of these failures on October 11, 2021; after an evaluation and release of updates, the flaws were publicly disclosed this week. Users of affected deployments are encouraged to update their firmware to the latest version available to mitigate the risk of exploitation.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
