While last week we talked about the false security feeling cloud services provide, today we see again how making use of cloud services is far from meeting the current cybersecurity requirements of companies.
Amazon made a publication informing its customers about a flaw in the Amazon EKS IAM authentication system:
A security researcher recently reported a problem in the AWS IAM Kubernetes Authenticator, used by the Amazon Elastic Kubernetes service. Service (EKS). The researcher identified a parameter validation problem in the plugin when it is configured to make use of the “AccessKeyID” template parameter in the string content of the request. The issue would have allowed a knowledgeable attacker to escalate privileges within a Kubernetes cluster.
AWS Security Bulletins
What is EKS?
According to official AWS documentation, Amazon Elastic Kubernetes (EKS) is a managed service (that is, by AWS, not the customer) that can be used “to run Kubernetes on AWS without the need to install, operate, or maintain it.”
CVE-2022-2385
The flaw causing the vulnerability is located in a specific line of code in the IAM authentication mechanism for Kubernetes:
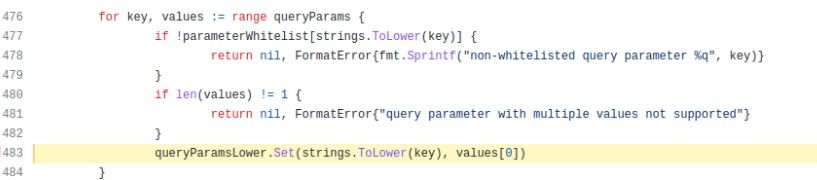
The expected behavior of the above code snippet is a validation of the capitalization of the parameter that is received, that is , the use of upper and lower case. However, this validation was not being carried out correctly, making it possible to send duplicate parameters.
This flaw in the authentication process could allow an attacker to bypass existing protections against attacks in which a valid data transmission is fraudulently repeated (replay attacks).
The vulnerability has been present since the first commit on October 12, 2017, which means that both the writable action and cluster identification tokens have been exploitable from day one.
Specifically, the exploitation of the username through the “AccessKeyID” parameter would have been possible since September 2, 2020, when AWS introduced this feature in the service.
However, it is worth mentioning that only those clients that use the “AccessKeyID” parameter are affected by the vulnerability, and Amazon released a patch that solved it on June 28, so those users that use AWS IAM Authenticator for Kubernetes in the Amazon EKS service do not need to take any mitigation measures.
This is not the case, however, for customers who manage their own Kubernetes clusters and make use of “AccessKeyID”, a situation in which AWS IAM Authenticator must be updated to version 0.5.9.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
