VLC is a free and open-source cross-platform multimedia player that has been downloaded more than one billion times. It can play the majority of multimedia files, as well as DVDs, Audio CDs, and VCDs, and a variety of streaming protocols that are presently being used by tens of millions of users all over the world on all operating systems, including Windows, macOS, and Linux, as well as Android and iOS mobile platforms. VLC can also play most video content protocols.
The buffer overflow vulnerability, designated as CVE-2022-41325 (CVSS score: 7.8) and found by 0xMitsurugi from Synacktiv, is a high-risk issue that lies in the vnc module and may be triggered by using a malicious vnc URL. This vulnerability has a score of 7.8 on the CVSS security rating scale.

As per the researcher “It is possible for an adversary to mislead VLC into allocating a memory buffer that is less than what is anticipated if they have control over a VNC server. When this happens, the attacker has access to a strong relative “write-what-where” primitive. He is able to crash VLC and run malicious script beneath the operating system.”
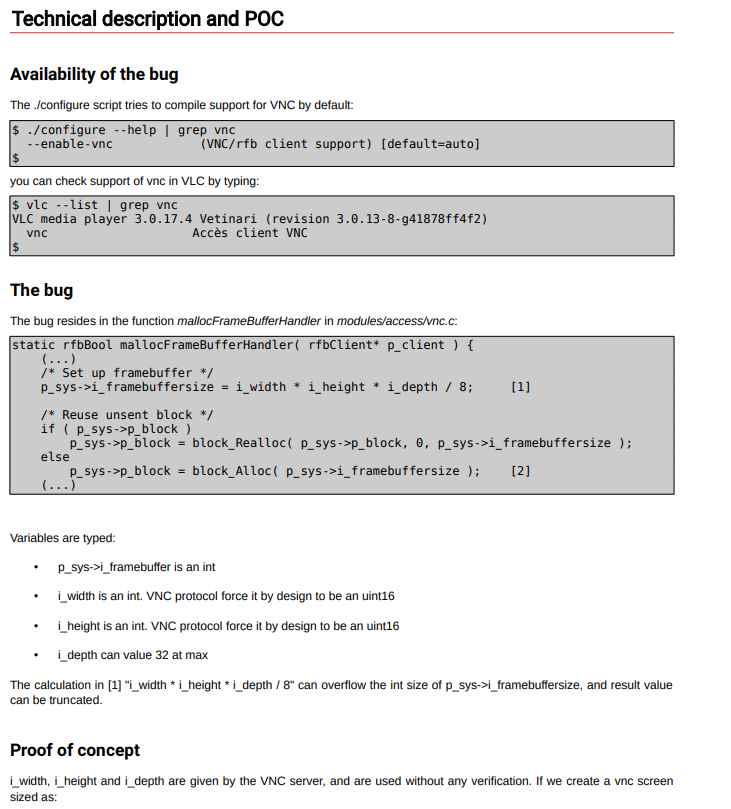
VLC video player versions 3.0.17 and older are vulnerable to the CVE-2022-41325 vulnerability, which was addressed with the release of VLC version 3.0.18. Up to this point, no exploits that take use of this vulnerability in order to execute code have been seen.
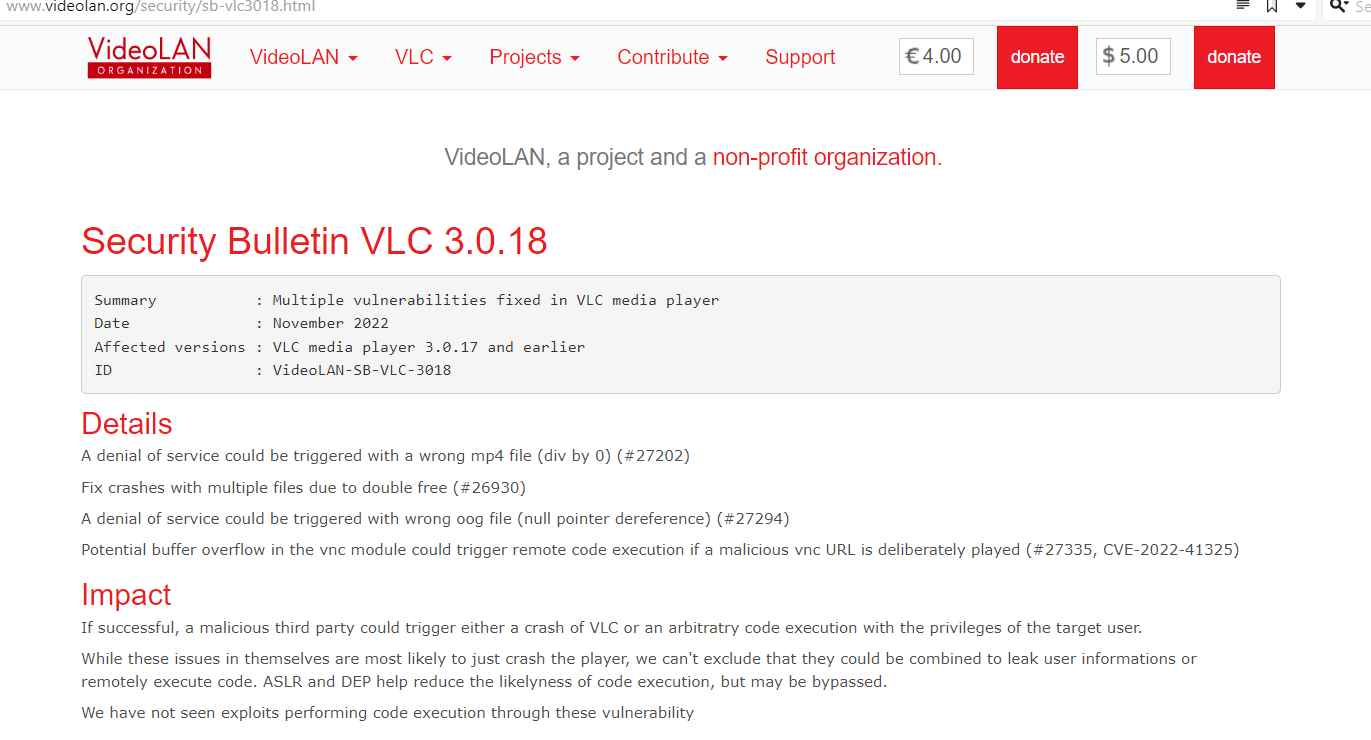
The most recent version further patched three more vulnerabilities, including the following:
The incorrect mp4 file (div by 0) (#27202) might result in a denial of service being initiated.
Crash fixes caused by duplicate free operations while many files are open (#26930).
If the incorrect oog file is used, a null pointer dereference might occur, which would result in a denial of service (#27294)
Impact
In the event that they are successful, hostile third parties have the potential to cause VLC to crash or to execute arbitratry code with the rights of the person they are targeting.
Although each of these vulnerabilities is most likely to result in the player crashing on its own, it is not impossible for them to be combined in a way that exposes user information or allows remote code execution. Both ASLR and DEP work to decrease the likelihood of code being executed, although they may be circumvented.
We are not aware of any exploits that have been used to execute code using these vulnerabilities.
In order to take advantage of these vulnerabilities, the user must first actively access a file or stream that has been specifically constructed.
Workarounds
Until the fix is deployed, the user should avoid opening files that have been provided by untrusted third parties and should avoid viewing untrusted remote websites (or they should deactivate the VLC browser plugins).
The problem is resolved in version 3.0.18 of the VLC media player.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
