Palo Alto Networks security team has issued a statement alerting its customers to a remote code execution (RCE) vulnerability in GlobalProtect, mentioning that threat actors can launch malicious code with root privileges.
The vulnerability was tracked as CVE-2021-3064 and could be exploited by authenticated threat actors on the GlobalProtect network. This flaw resides in PAN-OS versions prior to PAN-OS 8.1.17. Palo Alto issued a number of priority patches for enterprise customers on PAN-OS 8.1.17 and later.
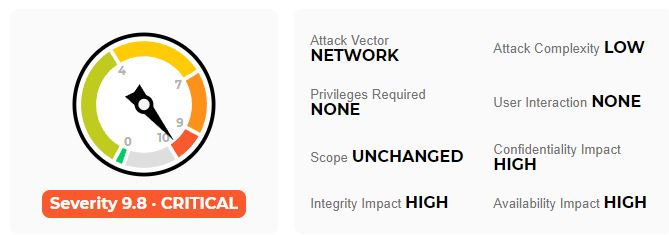
The flaw does not yet receive a score assigned by the Common Vulnerability Scoring System (CVSS).
Representatives of the company mention that no malicious exploitation attempts have been detected linked to this report, although they confirm that the cybersecurity company Randori had incorporated successful exploits into its Red Team solutions
In this regard, Randori Attack Team points out that the vulnerability affects Palo Alto firewalls that use GlobalProtect Portal VPN, allowing remote execution of unauthenticated code in vulnerable installations: “We were able to obtain a shell on the affected target, access sensitive configuration data, extract credentials and other tasks. Once an attacker has control over the firewall, they will have visibility into the internal network and may even perform lateral motion attacks,” the report said.
At the moment neither Palo Alto nor Randori will reveal more technical details about the flaw, this in order to prevent possible exploitation attempts. If the correction process progresses as estimated, complementary reports could emerge in the next 30 days.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
