New COVID-bit attack allows hacking into air-gapped device or network
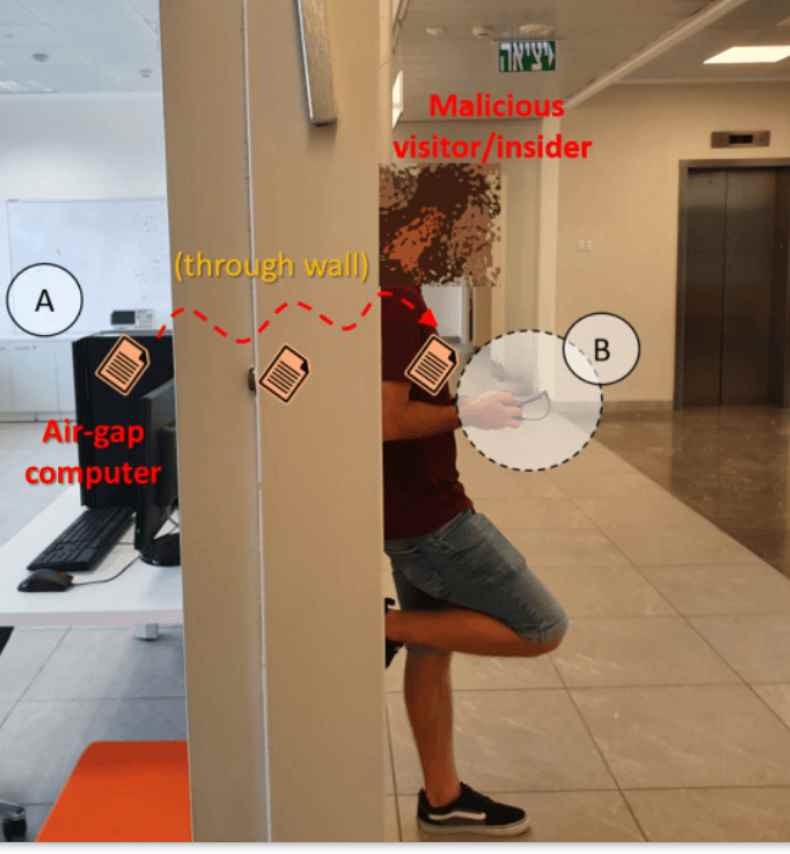
For reasons of safety, computers that are separated by an air gap are not connected to the Internet or any other network. Typically, they are used in energy infrastructures, governmentRead More →