A couple of months ago ESET researchers reported the detection of a hacking campaign targeting Spanish-speaking countries, mainly Venezuela. The operators of this campaign used a malware known as Bandook and have been active since at least 2015, although it was not until this year when it began to be documented.
This malware is described as a banking Trojan that has existed for more than 10 years and has evolved steadily. Previous hacking campaigns have used this malware to target journalists, activists and political opponents in specific countries. Some reports also point out that Bandook could have been developed by hackers for hire, something that explains the continuous maintenance that this Trojan has received over the years.
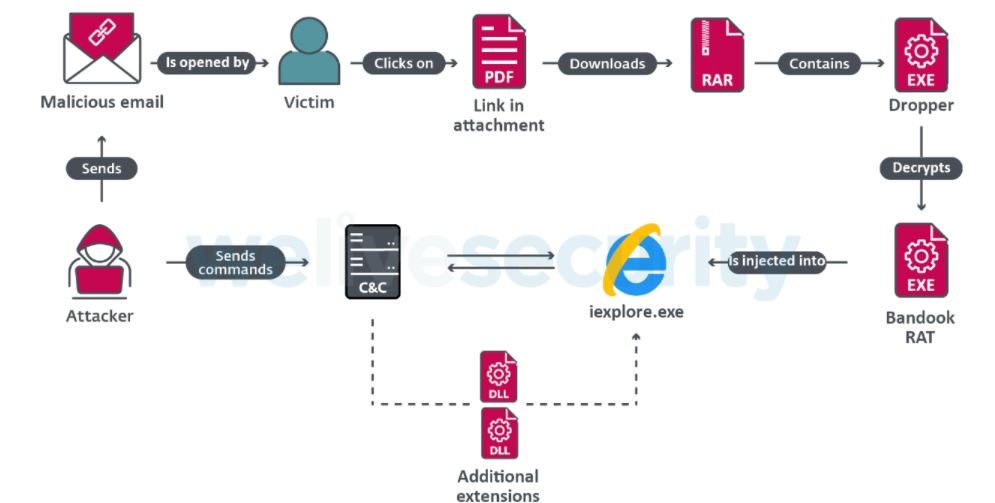
These attacks begin with sending malicious emails with a PDF file attached, which contains a link to download a compressed file and its corresponding password. Inside this file is hidden a dropper to complete the injection of Bandook in an Internet Explorer process.
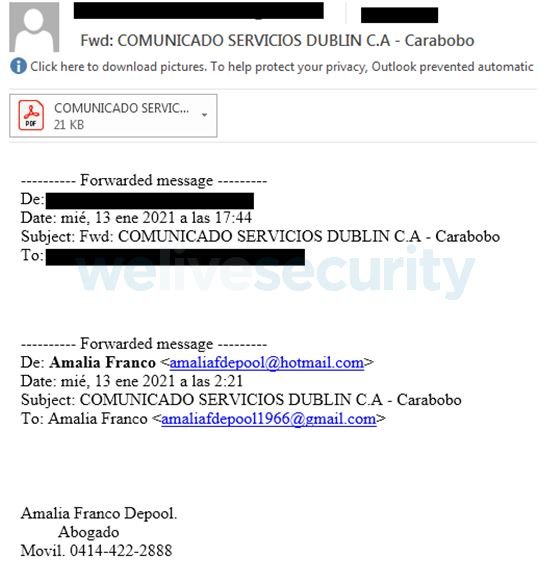
The emails received by potential victims are unclear and only contain a Header and Phone Number from Venezuela that experts believe could be invented or have nothing to do with cybercriminals.
Malicious links were trimmed with services like Rebrandly or Bitly and redirected users to cloud storage platforms like Google Cloud Storage, pCloud or SpiderOak, where the malware will be downloaded. Below are some samples of these stages of the attack.
The content of PDF files is generic and their name may vary, and the password to unzip the file is always the same (123456).
Once they gain persistence on the target system, cybercriminals can perform all sorts of malicious tasks, including intercepting and manipulating sensitive files, communicating with a malicious C&C server, WiFi connection interruption, deploying denial of service (DoS) attacks, activating camera and microphone, and many more arbitrary actions.
As mentioned above, the main target of this campaign is corporate networks in Venezuela, including construction companies, medical services, software development and even some retail stores. Once the malware is installed, the threat actors proceed to intercept the communications of the affected networks in an advanced espionage campaign. Experts mention that, due to its complex geopolitical situation, Venezuela is an ideal target for a cyber espionage campaign.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.


