Security mechanisms in the Google Play Store are the main anti-malware measure on Android devices, although the practice of downloading apps from unofficial sources remains the most important of the mobile security threats for users of these devices. A cybercriminal group trying to deploy malware on mobile devices should only manage to direct attacked users to malicious websites where they can find malware-laden applications; if the infected device does not have any security mechanism, the malware will operate freely on the system.
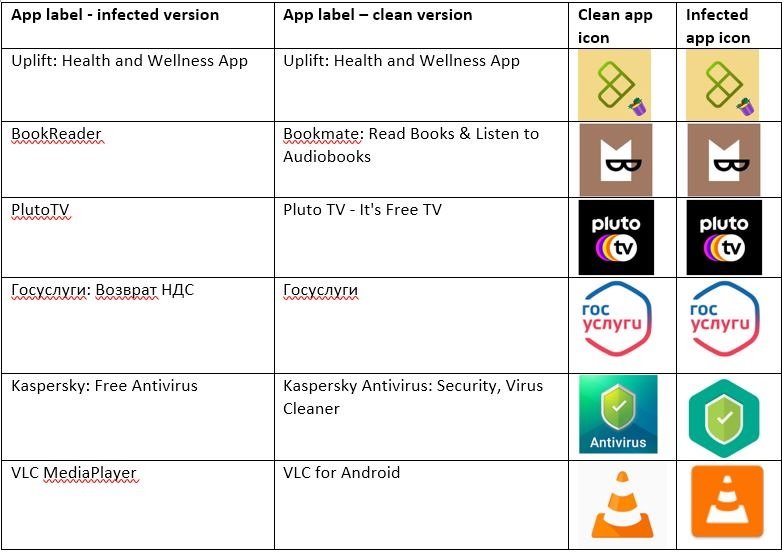
A recent mobile security report details the identification of TeaBot and Flubot, two of today’s most dangerous mobile malware variants. This is a family of banking Trojans identified in early 2021 and distributed via multiple malicious apps posing as free or “lite” versions of popular apps. This report was prepared by BitDefender researchers.
TeaBot, also identified as Anatsa, is a well-known development in the cybercriminal world. Reports issued shortly after its discovery mention that this malware can carry out overlay attacks via Android Accessibility Services to deploy malicious activities such as keystroke logging, stealing authentication codes and even allowing hackers to take full control of the affected device.
This is an efficient attack method as it is based on the imitation of some popular apps that are conventionally only available on official platforms. Many users who visit disputable websites are very likely to install these apps without knowing that they are opening the doors of their devices to malware.
Bitdefender’s report points to the identification of five new malicious Android apps that contain samples of this family of Trojans, which are often imitated by some popular apps with at least 50 million downloads on the Play Store. Despite the hard work of Google and legitimate developers, it is impossible to prevent users from downloading these apps from unofficial platforms.
Down below is a list of apps imitated by threat actors, showing that the similarities really make it difficult for users to distinguish between a legitimate app and a malicious tool.
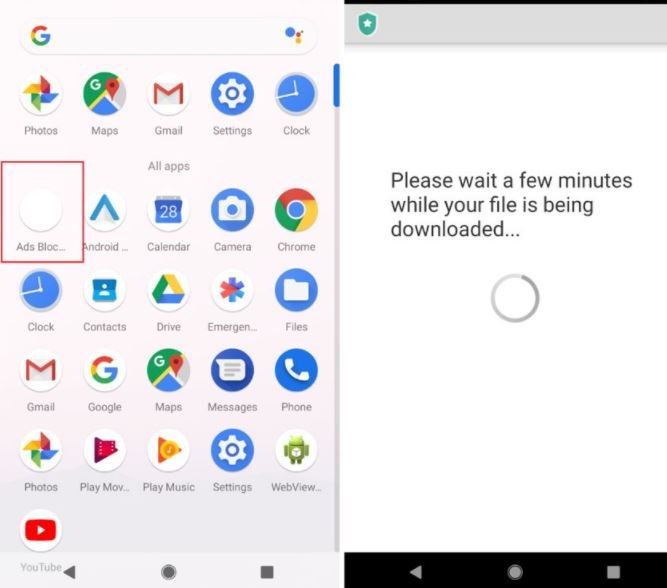
BitDefender researchers mention that this hacking campaign is still active, employing as its main attack vector a fake service to block online ads that actually operates as a “dropper” of the malicious payload. It is highly likely that hackers will employ other methods, although these have not yet been identified.
These fake ad-blocking tools do not have any of the features of the original version, and at the time of installation they ask for permission to show up on other apps, show notifications, and install apps outside of Google Play, which is the clearest indication of malicious activity.
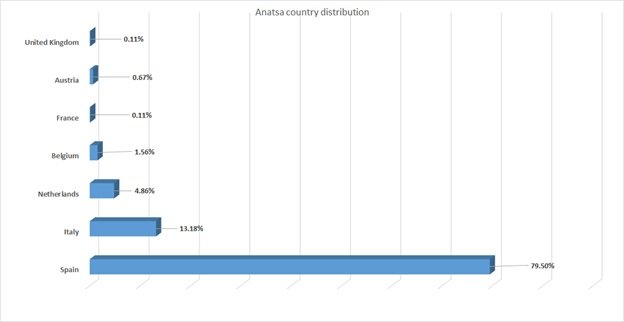
These attacks have been identified mainly in European countries such as Italy, Spain and the Netherlands.
As in most similar cases, mobile device users are advised not to download apps from unknown sources or unofficial sites, as this is the main method of injecting malware into mobile devices. Keeping the operating system and apps installed on your device updated is also recommended.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
