Due to the deteriorating conditions of the countries by the well known pandemic Coronavirus , many big firms such as Google , Microsoft and Facebook and many more, have asked their employees to remotely work from home. As companies shift their bases from physical office to individual’s home , this created an attractive situation for the attackers to get some hot cream from the milk and so more remote working from home creates a more vulnerable network and thus increasing chances for data breach . Though employees are asked to create strong passwords , but even a silly mistake by them to use bad or easily guessed passwords can cost a big loss to the company. So taking this point in consideration , many firms considered Multi-Factor-Authentication (MFA) the best tool to defend against cyberattacks . Microsoft said that “ There are over 300 million fraudulent sign-in attempts to our cloud services every day “ and make the statement that MFA can block over 99.9 percent of account compromise attacks.
HOW MFA (MULTI-FACTOR-AUTHENTICATION) WORKS ?
MFA is the another layer of security which is added to make network more secure . A pattern which is usually seen that user personal credentials and MFA are inter related to each other but in reality they are independent from each other which means that if somehow one of them got compromised there is no effect on the other users on the network . An example of this is Google authenticator which allows you the admin to authenticate the user’s identity . These MFAs like Google authenticator generates a MFA token which are generated on a user verified device and cannot be bypassed unless or until the verified device is in insecure hands.
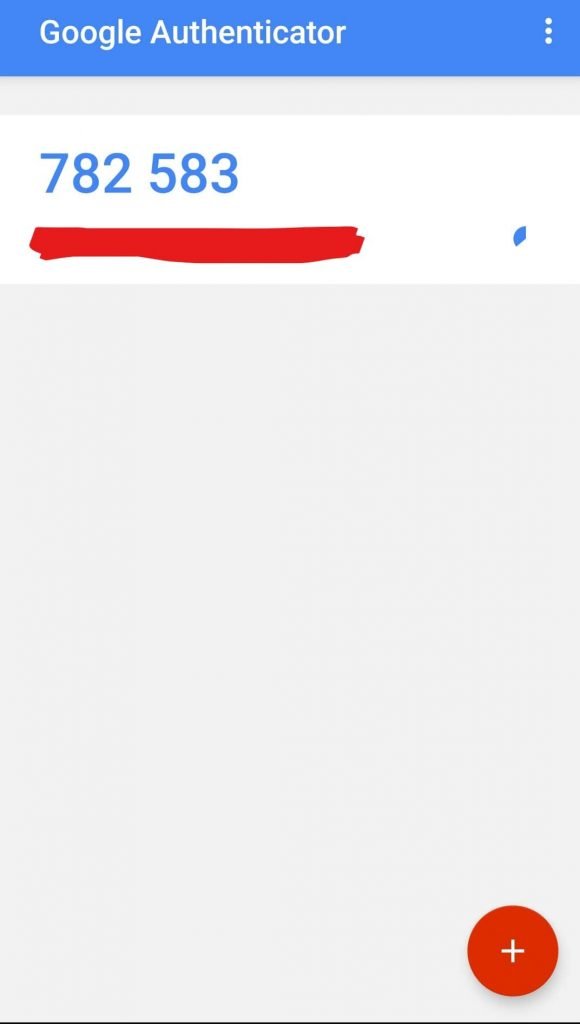
Thus the MFA token generally a time based code or Timebased-One-Time-Password (TOTP) which cannot be impenetrable verifies the user twice and thus decreasing the chances of impersonation .
IS IT VULNERABLE ?
Though we read some of the advantages of the MFA but they are limited to an extent . An attacker may be a step ahead sometimes and thus can bypass even the layers of security . In a recent paper published by SANS Software Security Institute , they listed some of the vulnerabilities :
Phishing Attacks :
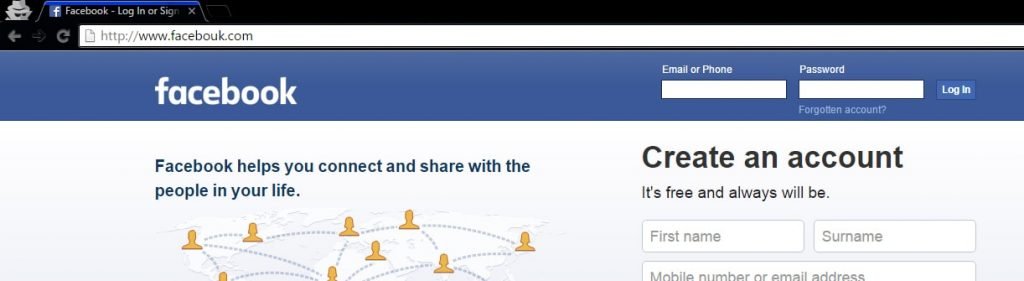
One of the most popular attacks nowadays which is similar to impersonation . Today’s generation gave this attack a new name , spoofing which means that an attacker who might be your close friend or may be contracted by someone will send you a web page and attaches a trusted mark or logo on that page that wins your trust and convince you to give your credentials to that page . Like here is the fake facebook login page which looks very much similar to that of the original one but the attacker has inserted a key logger in that page which means that every character you enter is tracked by the attacker .
Sometimes phishing attack takes place in a different way means that there are chances that attacker do not want you to enter your credentials instead he just wants you to click on the sent link to which a tool is attached which captures your current session cookies ( a session bound parameter which is used by browsers to make your surfing efficient ) automatically an when the attacker injects your cookie in the parameters , automatically it will open your login account and allows attacker to take the control of you account .
Social Engineering Attacks :
This attack is similar to that of Phishing attack but here the attacker wins you trust by physically interacting with you . Lets suppose an attacker is trying to attack on your bank and it wants the MFA token ( OTP ) which is the most secure layer and is difficult to bypass because it is generated only on your verified device . The attacker will call you Impersonating as the bank Manager or bank employee and says that our system is showing something wrong in your bank details and we need your OTP to verify you identity . Worrying about his saving , user gives the MFA code making its bank account less secure . The social engineering attack is the most common attacks nowadays because it does not require any technical knowledge and so number .
Design or Logic Flaws :
There might be chances that there is a vulnerability in the app which generate MFA tokens like which is founded in the LastPass app due to its design flaws .These are the flaws which occurs due to a mistake in the backend coding of the app . Thus a user might got attacked due to the design flaws if the attacker points out the vulnerability before the developer of the app .
Sometimes there are chances that an app is using old of basic protocols like SMTP ( Simple Mail Transfer Protocol ) which are not that much efficient with MFA and thus an attacker by using the outdated version of browser can skip the MFA and thus can decrease the security .
Simple or Reuse of Passwords :
According to the SANS , there are up to 73 percent of passwords which are duplicate and reuse by the company’s employee . The simple or reused passwords increase the chance of Brute force Attack . The common credentials obtained by the attacker during his one data breach can help them in his another data breach . Thus , simple and common password protected account are more vulnerable than harder ones .
HOW CAN YOU DEFEND THESE ATTACKS :
- Must ensure that you are entering your password in HTTPS protocol rather than HTTP protocol as encrypts your messages over the network . You can also check the green padlock next to the URL in browser.
- Check the URL of the page before entering your credentials like it should be www.facebook.com not www.facebouk.com .
- Do not give your login credentials to anyone by trusting the disguise guy .
- If the behavior of the app is not normal then immediately address the behavior to the developer
- Verify the source of the received document or the page from the authenticator

RSU is security researcher who is constantly working to make world a secure place to live. He is working day and night in Cyber Security area.
