Shadowserver Foundation, a non-profit security organization dedicated to collecting and analyzing data on malicious Internet activities, undertook a project to scan the Internet for Kubernetes API servers, finding some 380k implementations vulnerable to some form of access.
The organization performs daily scans of the IPv4 space on ports 443 and 6443, looking for IP addresses that respond with an HTTP status of “200 OK”, indicating that a successful request has been made.
Of the more than 450k Kubernetes API instances identified by Shadowserver, a total of 381,645 responded with “200 OK.” While this does not necessarily imply that these servers are completely vulnerable to some kind of cyberattack, Shadowserver considers this to be a large enough attack surface to be considered a problem, plus the exposure is unnecessary and most likely unintended conditions.
More than half of these conditions were identified in the United States, although there are also notable pockets of activity in some regions of Europe and South Asia.
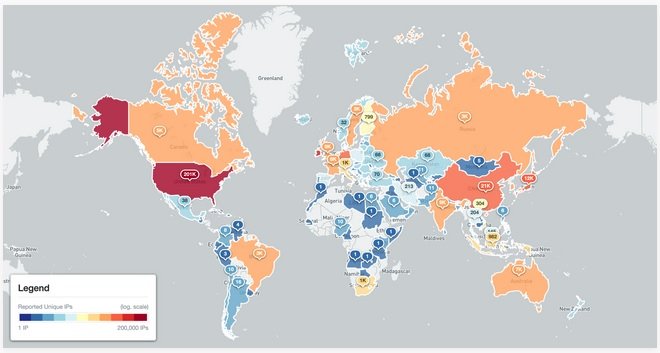
The analyses performed by Shadowserver also show the Kubernetes version (versions between 1.17 and 1.22 are the most popular) and the platform, with Linux/amd64 accounting for the vast majority of exposed instances.
The Shadowserver team added that its subscribers will get free data about Kubernetes instances accessible on their network. Users who receive notifications about potentially exposed instances are encouraged to review the official guide to secure access to the Kubernetes API.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
