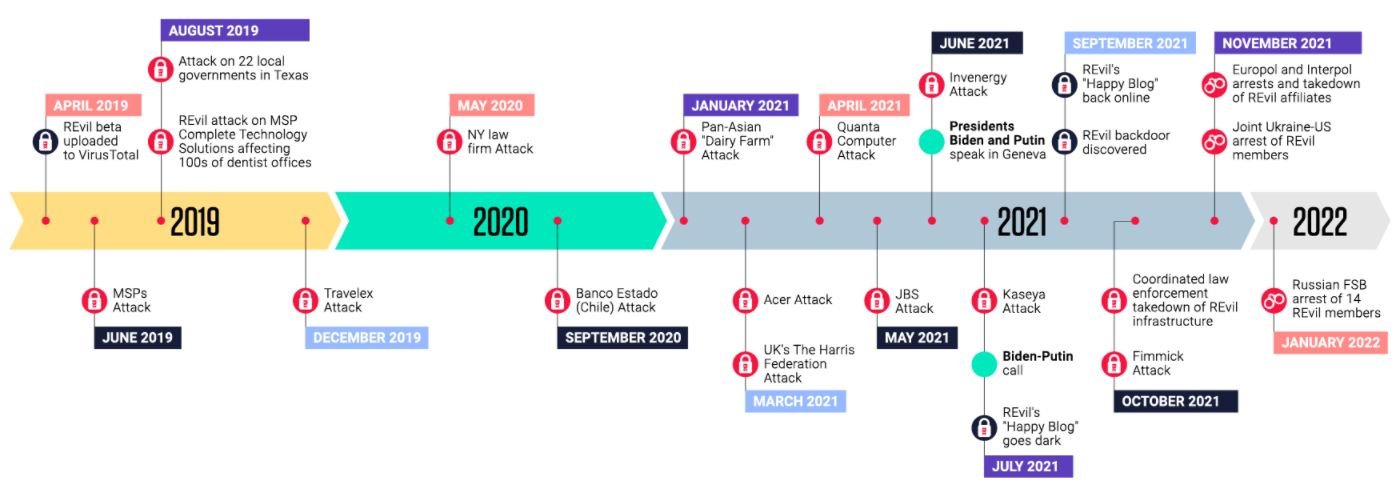
Although law enforcement in Russia, the United States and other countries believed that the recent arrest of some members of the cybercriminal group REvil would represent a severe blow to this malicious operation, specialists report that these arrests have not generated considerable changes.
In the latest report by ReversingLabs, he points out that, in fact, reports of REvil activities have increased during the last week, denying the reports of the Russian Federal Security Service (FSB) regarding the interruption of this malicious operation and its potential disappearance.
As you may recall, a couple of weeks ago the Russian government arrested 14 individuals associated with REvil (also known as Sodinokibi), in an operation allegedly deployed in collaboration with law enforcement in the United States and after Joe Biden’s administration called on Russia to crack down on ransomware operations. Despite their significant geopolitical implications, these arrests did not diminish the strength of this hacking group.
The researchers note that, since a week ago, an average of 26 samples of REvil ransomware have been detected per day, which equates to about 360 attacks since the FSB announced the arrests; the average number of weekly attacks before the arrests was 160. Although experts believe that it is necessary to analyze this behavior for a few more weeks, they also believe that REvil hackers will be able to maintain this level of activity without problem.
For some cybersecurity specialists, ransomware operations like REvil are not affected by the efforts of law enforcement agencies because Maksim Yakubets, the alleged founder of this malicious operation, has not been arrested.
Other hypotheses hold that the persistence of these groups is explained by the fact that they work as corporations, leaving much of their operations to affiliated organizations. Arrests actually affect affiliated groups, so the infrastructure that keeps ransomware active isn’t really affected.
That is why experts believe that protection depends largely on organizations, which must develop the capacity to identify and contain potential security threats, in addition to constantly evaluating their defenses to mitigate the consequences of these attacks to the minimum possible.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
