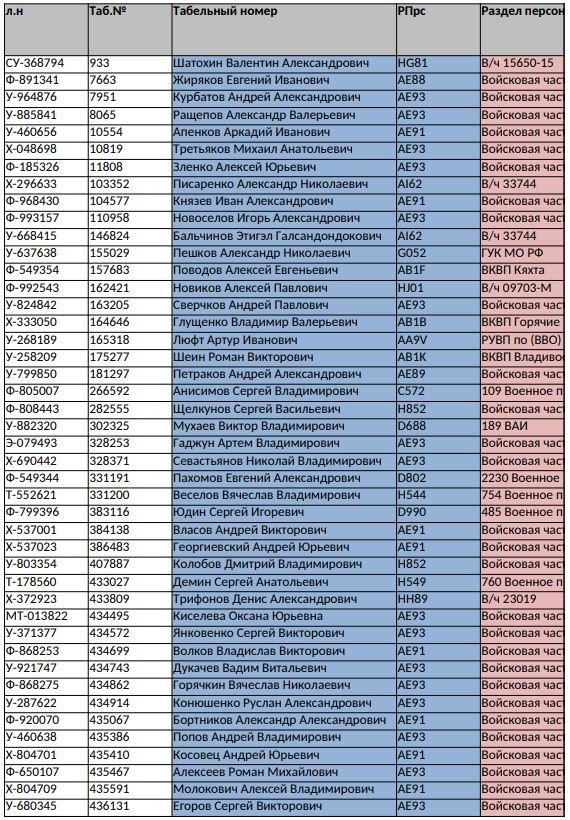
A recent report says that specialists from the Center for Defense Strategies of Ukraine obtained the personal data of some 120,000 Russian military personnel in retaliation for the invasion ordered from the Kremlin. Apparently, these records include details such as full names, addresses, passport numbers, and phone numbers.
Although independent investigators say that the leak is legitimate and other sources mention that there is a group of activists behind this leak, more details are unknown so far. However, specialists believe that this could have a severe impact on some active members of the Russian military.
Over the past week, hundreds of cyberattacks have been reported between Russia and Ukraine, amid the international crisis over the armed conflict. Former director of the UK’s National Cyber Security Centre (NCSC) Ciaran Martin said: “The online cyberattacks against Ukraine in recent days represent only part of the long-running harassment campaign ordered by Russia.”
The leak of information from Putin’s troops is not the only counterattack measure pushed by Ukraine. Just a few hours ago, Ukraine’s digital transformation minister called for the formation of what he defined as a “computer army of volunteers.”
The official hopes that this measure can contain cyberattacks orchestrated by Russia and Belarus, in addition to undertaking offensive measures against the critical infrastructure of rival nations.
On the other hand, some sources close to the UK government report a notable increase in malicious traffic on its territory, which has tested its firewalls in recent days. Although government organizations claim to be in compliance with the NCSC’s cybersecurity recommendations, this could be the prelude to a wave of cyberattacks.
Given this scenario, it is best for public and private organizations to realistically assess their operational resilience during a prolonged period of heightened anxiety around cyberattacks. Creating stressed and fatigued teams before a crisis occurs will only lead to poor performance when it’s time to implement defense systems.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
