Hundreds of thousands of Huawei device users suffered infection from a variant of malware identified as Joker after downloading various malicious apps available on AppGallery, the exclusive app store for Huawei devices. This malware, also known as Bread, was first detected in September 2019 by Google security teams, eliminating about 24 affected apps.
Experts point out that Joker is a malicious app disguised as an Android system tool that allows threat actors to deploy all kinds of attacks, including disabling the Google Play Protect service, installing additional malware, fraudulent ads and posting fake reviews.
A Doctor Web report revealed the finding of at least 10 applications on Huawei AppGallery compromised with malicious code: “The code found in these apps turned out to be the dangerous Android.Joker Trojan operating through unauthorized subscription to Premium services,” the report notes, adding that at least 538,000 users have installed any of these malicious applications.
After downloading and running, these apps worked as users expected to avoid raising suspicions. These apps were hidden as virtual keyboard tools, camera apps, video game launchers, messaging apps, stickers, and mobile games. Most of these apps were developed by Shanxi kuailaipai network technology, while the remaining two were created by an almost unknown Chinese company (何斌).
The following is a list of reported malicious apps:
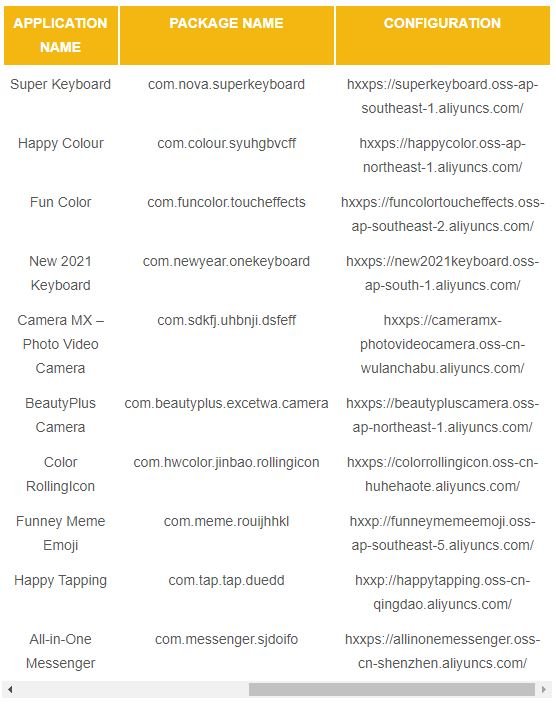
Once the malware runs, it connects to the malicious C&C server to receive the necessary configuration and download multiple additional components. One of these components is able to automatically subscribe Android device users to Premium mobile services of all kinds, which can generate million-dollar profits depending on the number of users affected.
Doctor Web experts notified Huawei of their findings, which proceeded to quickly remove these services from its AppGallery. Users who have installed any of these applications should remove them as soon as possible, in addition to verifying their statements to verify that they have not subscribed to an unauthorized service.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
