Introduction
Dmitry (Deepmagic information gathering tool). This tool is Preinstalled in Kali Linux. We can use this tool for the first stage of penetration testing and this tool is designed to collect the information about the target hosts by using some commands of Dmitry. We have different options in this and we will explain to you some options which show unique information about the host
Environment
OS: Kali Linux 2019, 64 Bit
Kernel-Version : 5.2.0-kali2-amd64
Steps To Execute
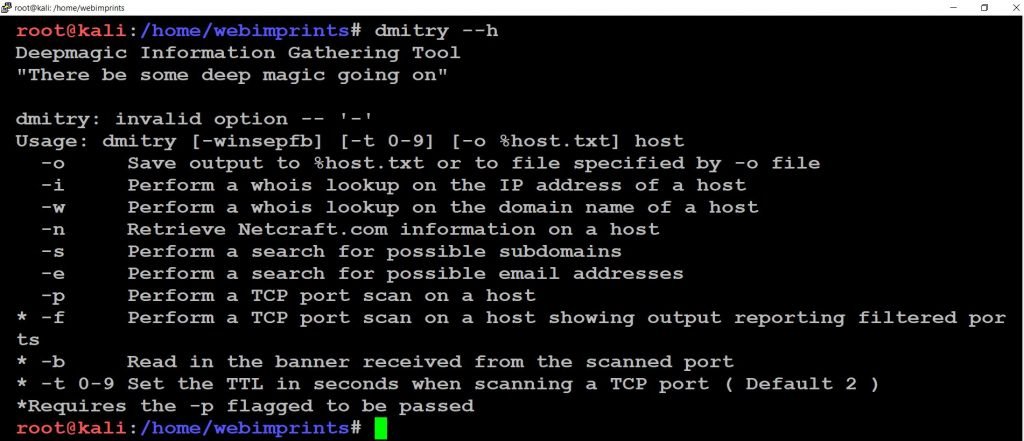
- Firstly use command dmitry –help, this command displays all the help options of Dmitry.
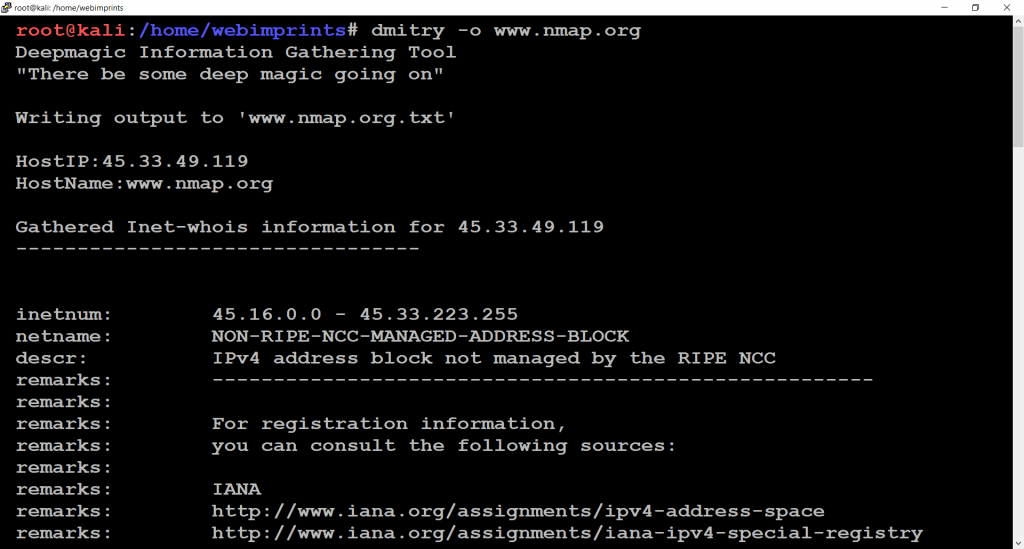
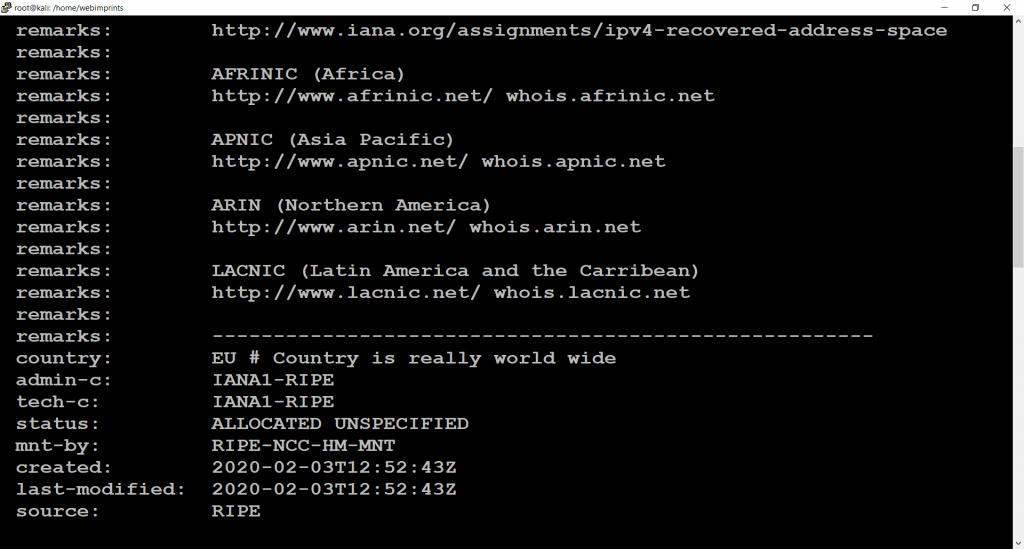
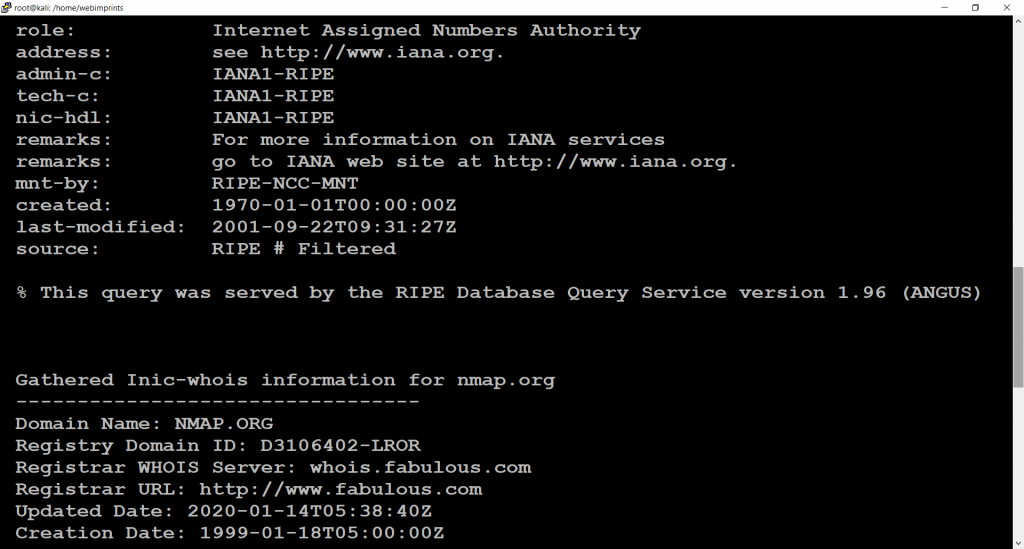
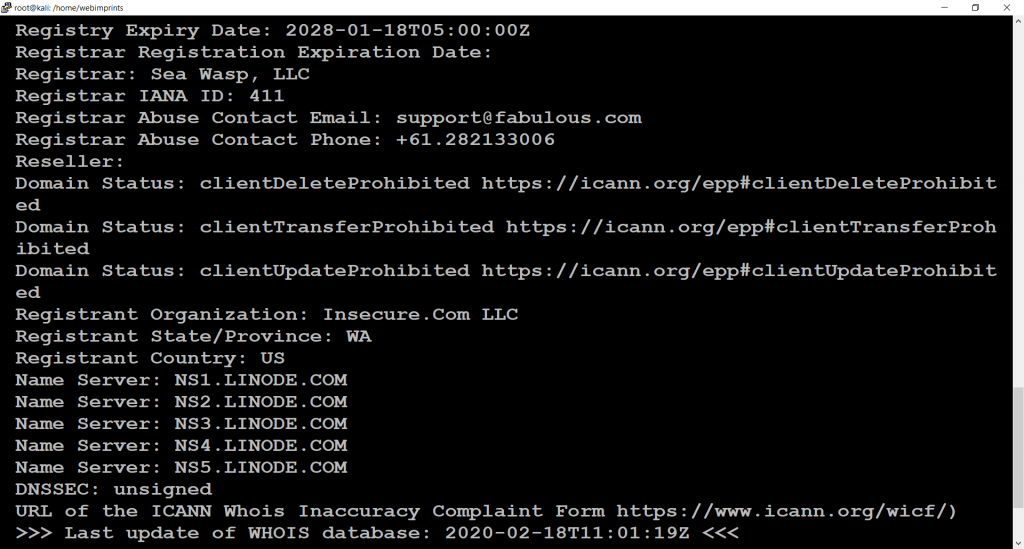
- Use command dmitry -o www.nmap.org. When we use this command we can find some unique information about host Like (Host IP, Hostname, Domain name, Registry Domain ID, Registrar WHOIS server, Registrar URL, Creation Date, Updated Date, Registry Expiry date, Contact Email, Contact Phone, Registrar IANA ID, Number of name servers)
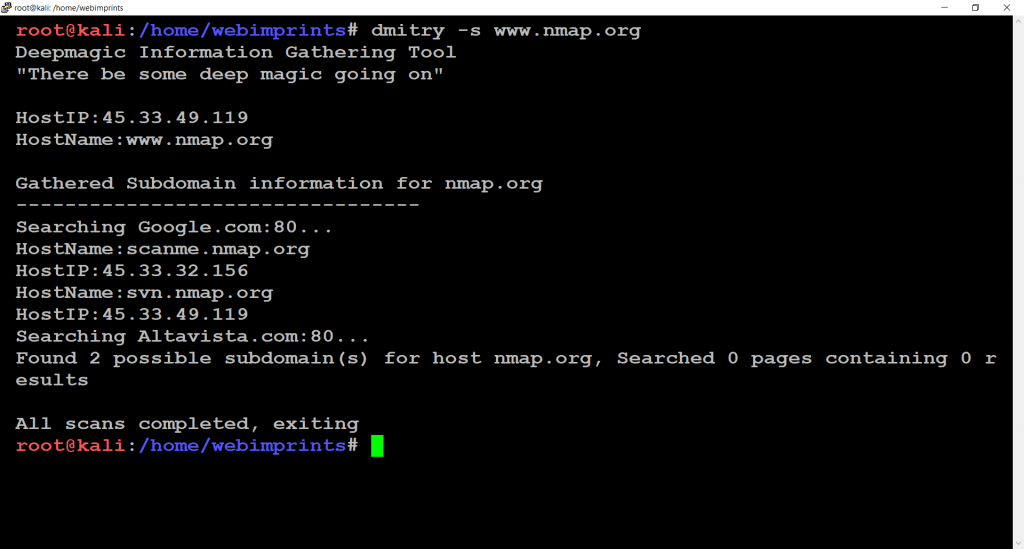
- Use command dmitry -s www.nmap.org.
- This command is used to find out the Subdomain Information of Host with a number of Host Names and Host IP
- -s to perform a search for the possible subdomains
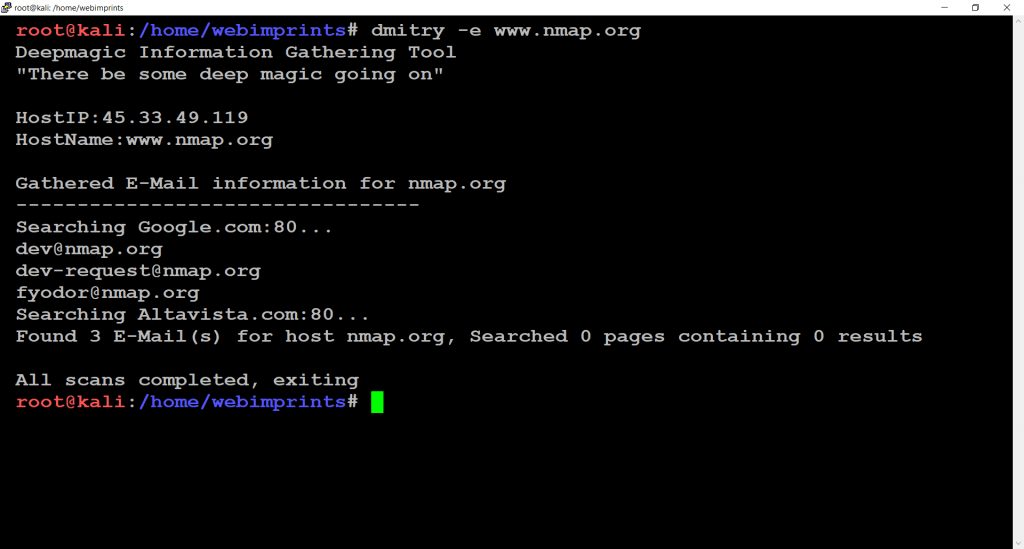
- Use command dmitry -e www.nmap.org.
- This command finds outs number of possible email addresses
- -e To perform a search for the possible email address
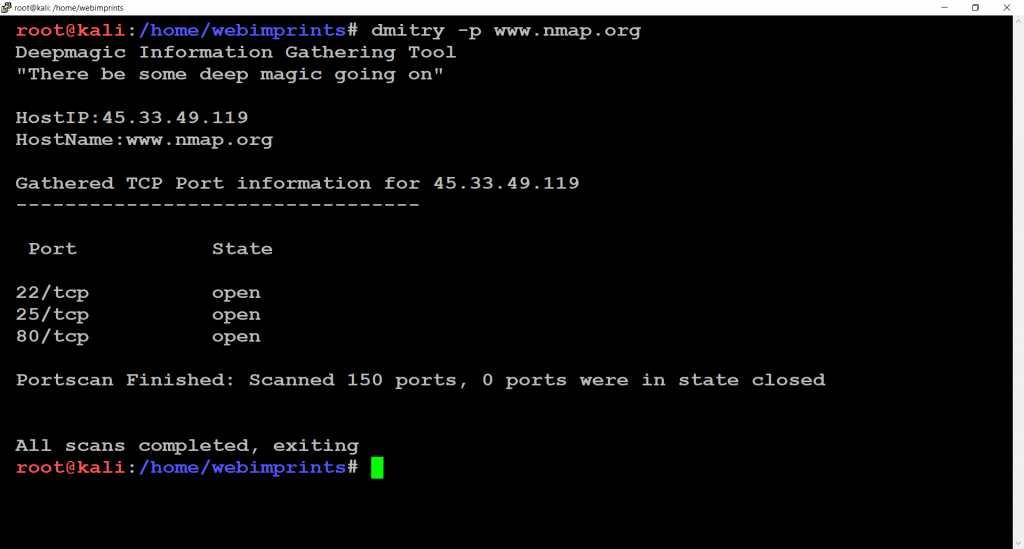
- Use command dmitry -p www.nmap.org.
- This command finds outs all TCP Open Ports
- -p is used to perform TCP port scan
- 22/tcp is used for Secure shell
- 25/tcp is used for Simple mail transfer protocol
- -p is used to perform TCP port scan
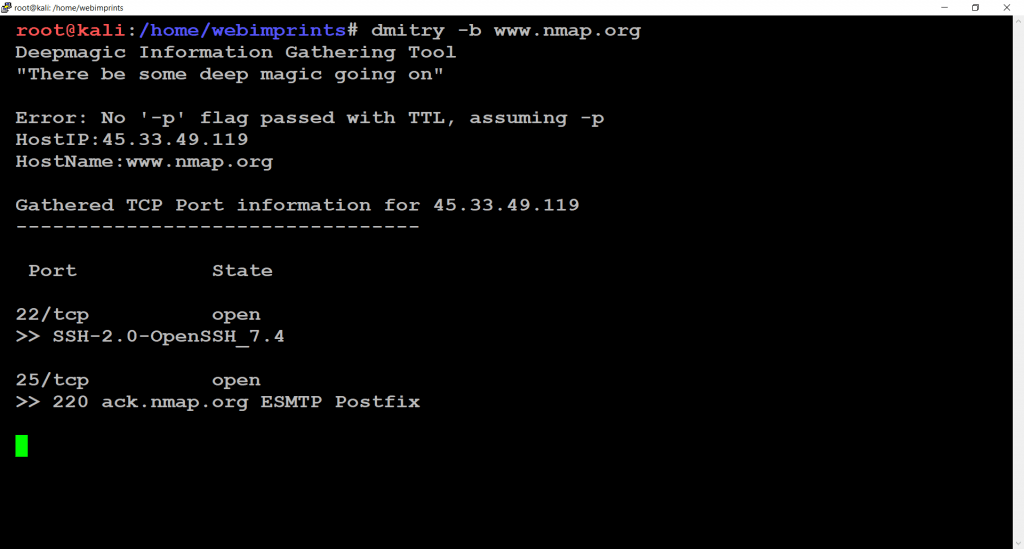
- Use command dmitry -b www.nmap.org.
- This command shows banner received from the scanned open port
- -b shows the banner received from the scanned port
- SSH – Secure Shell
- EMSTP – Enhanced Simple Mail Transport Protocol
- -b shows the banner received from the scanned port
Cyber Security Researcher. Information security specialist, currently working as risk infrastructure specialist & investigator.
He is a cyber-security researcher with over 18 years of experience. He has served with the Intelligence Agency as a Senior Intelligence Officer. He has also worked on the projects of Citrix and Google in deploying cyber security solutions. He has aided the government and many federal agencies in thwarting many cyber crimes. He has been writing for us in his free time since last 5 years.
