Multiple hacking groups have infiltrated the code of platforms like Discord and Slack to abuse some legitimate functions for malicious purposes, including stealing information and sending Trojans and other malware variants.
According to Cisco Talos experts, a key element in malware deployment campaigns is the use of files and domains that are not easily blocked or deleted, a requirement that meet platforms like Discord and Slack: “These applications are legitimate, so their use removes many of the obstacles faced by cybercriminals.”
The key to the attack is in content delivery networks (CDNs), technology used by these platforms for storing shared files back and forth from channels: “Files are uploaded to these platforms and users can create links for anyone to access, even without requiring the user to have Slack or Discord installed.”
The attack is based on sending a malicious link that the target user will need to open, allowing to bypass security measures in the system: “In the case of Slack, it is very easy for victims to click on this link, as it would appear legitimate communication from a company,” the report states. Cybercriminals can also deliver malicious payloads to the CDN via HTTPS encryption hidden in messages: “Over the past year we observed that many common compression algorithms were used, including ACE, GZ, TAR and ZIP.”
The messages, which could address topics such as offers or bank transactions, are written in multiple languages, including English, French, Spanish, German and Portuguese.
The following screenshot shows this type of attack on Discord, which shows a first-stage malware tasked with obtaining an ASCII blob from a CDN on the platform. Discord CDN data becomes the final malicious payload and is injected remotely, experts report.

On the other hand, the Discord API became a highly effective tool for threat actors to carry out data theft attacks. According to the report, C&C communications are enabled through webhooks, developed to send automated messages to specific Discord servers, usually linked to services such as GitHub: “The Discord domain helps threat actors hide a data theft process by making it look like any other type of web traffic.”
This communication flow can also be used to alert attackers when new systems are available to be hijacked and deliver updated information about those they have already infiltrated.
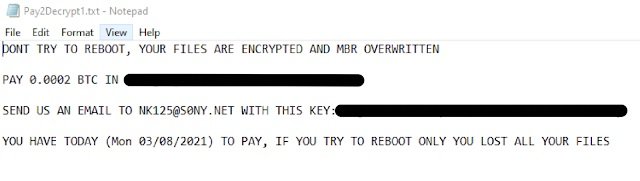
Finally, experts detected multiple hacking campaigns associated with the Pay2Decrypt LEAKGAP ransomware, which uses the Discord API to communicate with its C&C server, for data theft and bot registration: “After a successful infection, the data stored in the system becomes unavailable to victims and the ransom note is displayed.”
Mitigating these attacks involves implementing multiple measures, although it primarily requires developers of these platforms to implement better security mechanisms. To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
