As many will already know, most ransomware groups currently operate as ransomware as a service (RaaS) platforms, meaning that they are comprised of a set of malware developers who partner with third parties to attack a target. The profits made from these attacks are divided among the threat actors, although it is almost always the end attackers who get most of the money.
Compromising the systems of an affected organization is a complex task and working with intermediaries allows malware developers to deal with other issues equally important to cybercriminal operations, although some ransomware creators have been trying to find models that represent greater profits for them.
Such is the case of LockBit 2.0, the new iteration of a dangerous and well-known ransomware that is trying to eliminate the intermediary with the recruitment of accomplices within organizations, which would considerably facilitate access to the affected networks.
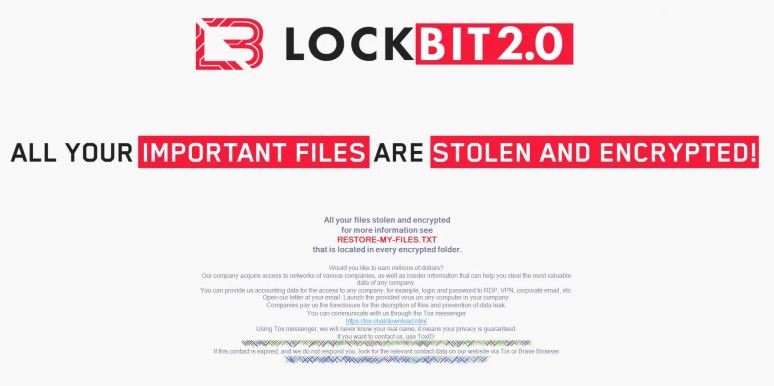
A few weeks ago LockBit operators released the new version of their RaaS platform, which included the creation of new websites in Tor and more advanced features than in the first version, including automatic encryption of devices using group policies.
One of the most striking features in this new version of ransomware is the inclusion of a message on encrypted Windows systems offering internal network administrators the ability to give hackers access to more resources in the affected organization in exchange for “millions of dollars.”
“Would you like to make millions of dollars? Our company acquires access to various companies’ networks and inside information. You can provide us with accounting data for access to any company, for example, remote desktop username and password, VPN, corporate email, etc.,” the hackers’ message states.
The message also specifies that data subjects should open the letter in their email, run the virus on the affected computer and let the infection flow. This message includes a link to the Tox Messenger chat platform, which provides anonymity to its users.
Although this method of attack seems somewhat unprecedented, similar practices have been detected on previous occasions. Such is the case of a Russian hacker who was arrested a year ago for recruiting Tesla employees in order to inject a dangerous malware variant into the company’s premises.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
