Cybersecurity experts report that what seems to be the complete source code for the Paradise ransomware was posted on a hacking forum, allowing any group of threat actors to develop their own malicious code from the leaked information. This information was posted on the illegal XSS forum and is only accessible to users active on the site.
Tom Malka, a researcher specializing in ransomware, shared the source code with the cybersecurity community, describing how he compiled the package and how this malware works. According to his report, Paradise creates three executables: a ransomware configuration generator, an encryption tool, and a decryption tool.
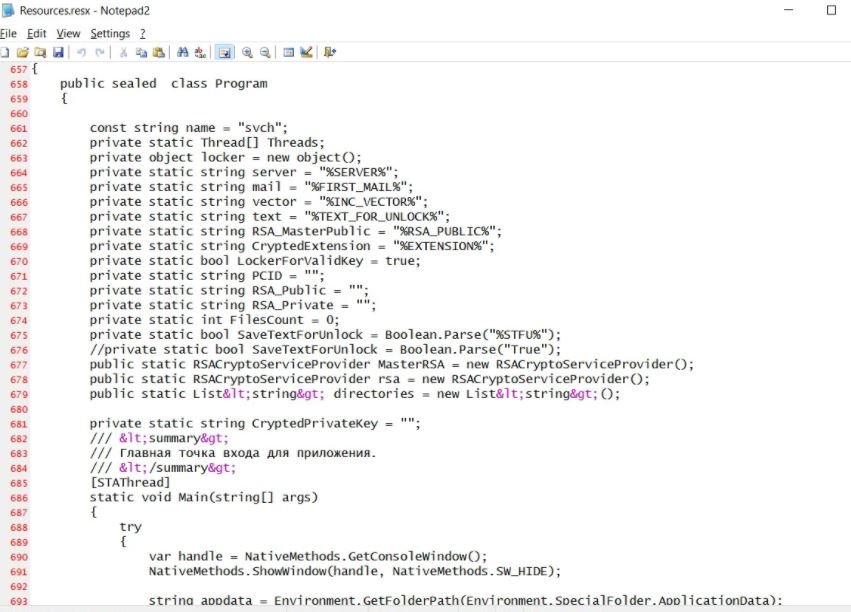
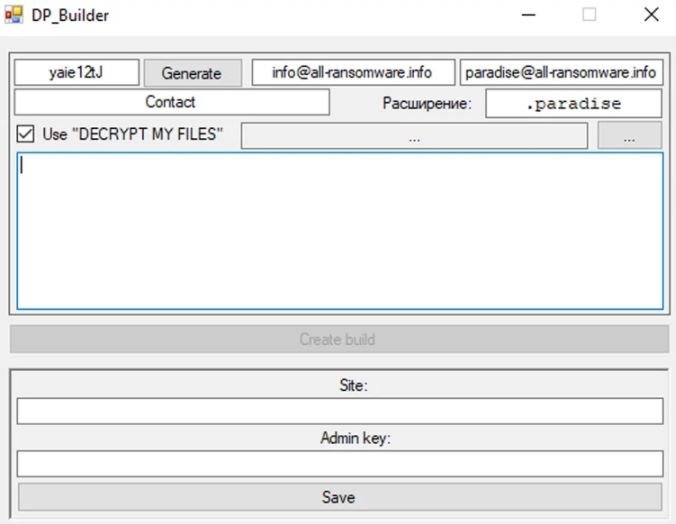
The source code of the malware is full of comments written in Russian, which clearly indicates the origin of this malicious development. Another characteristic feature is that the affiliates of this ransomware can use a construction tool to create customized versions of Paradise, including their own C&C server, a new encrypted file extension and an email address to contact the victims.
This ransomware group began operating at the end of 2017 by sending massive phishing emails with malicious IQY files to download and install the malware. During the following months, new customized versions began to appear, including bug fixes that allowed free decryption of infected files.
Michael Gillespie, the expert who created the original Paradise Ransomware decryption tool, mentions that he detected at least three versions of the malware:
- Paradise: Native version with multiple flaws that allowed files to be decrypted without paying the ransom
- Paradise .NET: Fixed version that changed the encryption algorithms to use RSA encryption.
- Paradise B29: New variant that focuses on encrypting only the end of affected files
The researcher has not been able to confirm if all the Paradise variants were created by the same group, as this malware knowledge actually operated as a kind of ransomware-as-a-service (RaaS) platform.
Data collected by the ID Ransomware security project indicates that Paradise was widely distributed between September 2017 and January 2020. Nonetheless, during the second quarter of 2020 the operators of this ransomware reduced their activity considerably, possibly due to constant failures or the appearance of other RaaS platforms.
Finally, Gillespie believes that the leaked source code would allow the appearance of new and more dangerous variants of this ransomware, although so far this is only speculation as there is no indication of new activity related to the original code.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
