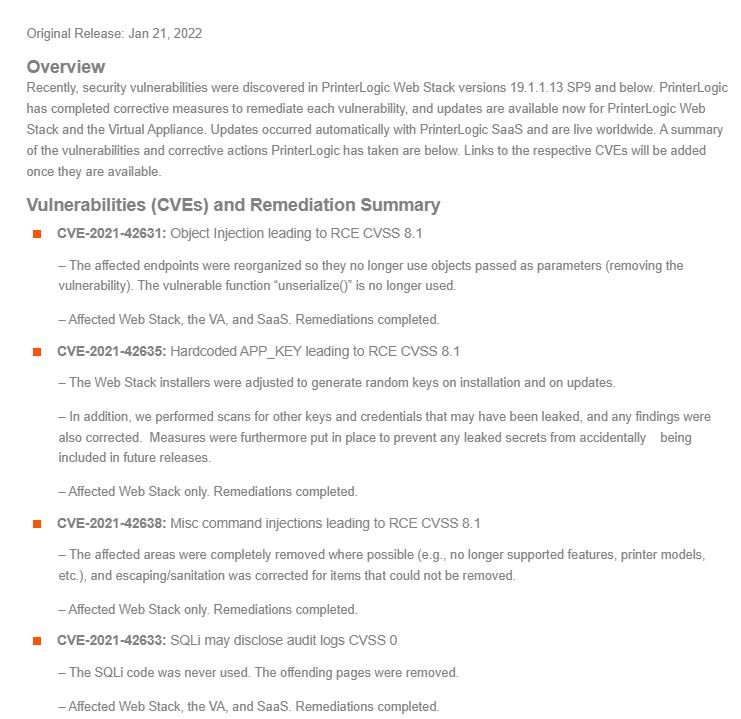
Cybersecurity specialists reported the detection of three vulnerabilities in PrinterLogic whose exploitation would allow threat actors to trace a remote code execution path on any connected endpoint. As you may remember, this is quite a widely used print management software for enterprise environments.
Below are brief descriptions of the detected flaws, in addition to their respective identification keys and scores assigned by the Common Vulnerability Scoring System (CVSS):
- CVE-2021-42631: An Object Injection Problem with 8.1/10 CVSS
- CVE-2021-42631: Coding Error APP_KEY with CVSS Score of 8.1/10
- CVE-2021-42638: Command injection failure with CVSS score of 8.1/10
The report was presented by Yahoo’s The Paranoids vulnerability analysis team. Vasion, suppliers of the PrinterLogic software, corrected these flaws with the release of version 19.1.1.13-SP10, available a few days ago. This update also fixes other medium-severity flaws in PrinterLogic.
Blaine Herro, a member of The Paranoids, notes that PrinterLogic is an attractive attack target as it has an agent that can run on many endpoints for component installation or configuration of other endpoints with administrator privileges: “If an attacker finds a severe vulnerability, more than 140 high-profile organizations could be affected.”
The severity of failures can be reduced due to attackers requiring a privileged network position through a VPN or abusing applicable vulnerability on a device at the perimeter.
The expert went on to detail an exploit that begins with an injection of unauthenticated PHP objects; Once the server is compromised and persistent access is secured, attackers could move laterally to arbitrary workstations when users perform a one-click installation, prompting the PrinterLogic workstation client to deploy and install the driver package.
Herro controls the contents of a driver package sent to an endpoint on macOS and Linux or Windows by manipulating the database, thus obtaining an arbitrary write of the file system to the connected endpoints. The researcher also explains how to do this on macOS by injecting a script between the scheduled maintenance scripts that the periodic service runs.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
