A team of security researchers managed to inject a web shell into the entertainment system installed on Boeing 747 aircraft in order to exploit a vulnerability that has existed for more than 20 years. Experts say this is a relatively easy attack to deploy, although it can be said that the Boeing 747 is a very rare aircraft today.
“The entertainment system on these aircraft is about 25 years old, so it lacks many safety features considered standard today; Still, it was a real challenge to achieve first access to the target system,” the researchers’ report notes.

This system was running a management server on Windows NT4 SP3, a precedent for current Windows servers. The age of this system also represented a problem for experts, as they were unable to use modern pentesting tools: “These tools didn’t even exist when NT4 was no longer used,” the report notes.
One of the main drawbacks when trying to hack NT4 is that, usually, the payload is executed by the cscript function of the Windows system, present in all versions of the system and that it functions as a script execution tool: “NT4 does not have cscript, because this operating system is older than the tool and it is not possible to run any script to run code remotely.”
Another impediment is that this system is a stand-alone workstation, not a domain, so it was also unlikely to intercept hashing on the network. Another problem is that real-time testing required the aircraft to stay on.
Instead of employing a recent hacking approach, the researchers employed a small character encoding trick, performing a directory tour during system installation. Modern operating systems tend to use the UTF-8 standard, which encodes characters in one byte instead of two as UTF-16, so researchers had to recode the commands before deployment.
“In each directory attack, the attacked program must be on the same disk as the web server. In our case, we needed the system32 folder to be on the same drive as the integrated entertainment system,” the experts mention. Researchers exploited a second flaw that gave them permanent access to this system through a web shell. This flaw is identified as CVE-1999-1011 and was discovered more than 20 years ago.
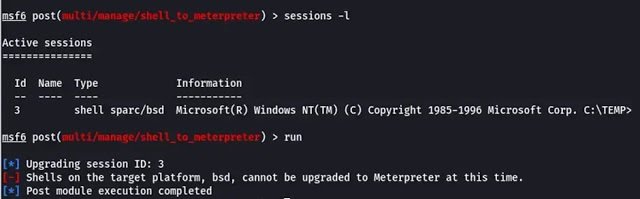
Eventually the researchers infiltrated the system using metasploit’s TFTP server module to access the command line and retrieve the hashing of the administrator password.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
