Cybersecurity specialists report the finding of CVE-2022-0185, a severe vulnerability in the Linux kernel that can be exploited to evade containers in Kubernetes, allowing threat actors to access resources on the host system. Experts say that the exploitation of this error is relatively easy and an attack could have disastrous consequences, so it is necessary to find immediate solutions.
A container escape attack can prove highly dangerous because it would allow threat actors to pave the way for deeper infiltration and even perform side-moving attacks on the affected network.
The flaw was described as a heap-based buffer overflow in the “File System Context” component of the Linux kernel. Triggering the attack flow allows malicious hackers to change the values in the kernel memory and access any process running on the same node.
Several Linux distributions published security alerts, mentioning that a local user can exploit the flaw to escalate privileges on the system. For the attack to be successful, the attacker must take advantage of an unprivileged namespace or use “unshare” to enter a namespace with permission CAP_SYS_ADMIN.
This capability is not the default setting in Docker, and it is not common practice to use the “-privileged” flag when starting the container. In addition, the “unshare” command is blocked by Docker’s “seccomp” filter by default, so running the command is not allowed. One report notes that when Docker or other containers are used in a Kubernetes cluster, the seccomp filter is disabled by default, so the “unshare” command is not blocked.
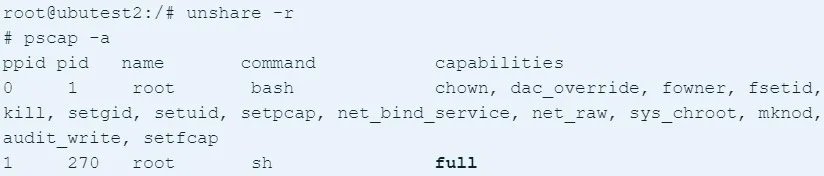
Threat actors could execute the command and obtain a shell with full capabilities, including running code as root user on the compromised system.
The buffer overflow flaw affects all versions of the Linux kernel from 5.1-rc1 to the latest versions, while also residing in Ubuntu 20/21, Debian 11, and some Red Hat packages.
Upgrading the Linux kernel to version 5.16.2 or later should be sufficient to address the issue. However, the update is not yet available for all Linux distributions and creating the kernel from the source is not an option for most system administrators.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
