The Demonic Vulnerability (CVE-2022-32969) was revealed by the Halborn team. The vulnerability exists in MetaMask, Phantom, Brave, xDefi, and others wallets.
CVE-2022-32969: Insecure permissions vulnerability in MetaMask and other browser extension cryptocurrency wallets allows a threat attacker to access a victim’s secret recovery phrase on disk via remote or physical access.
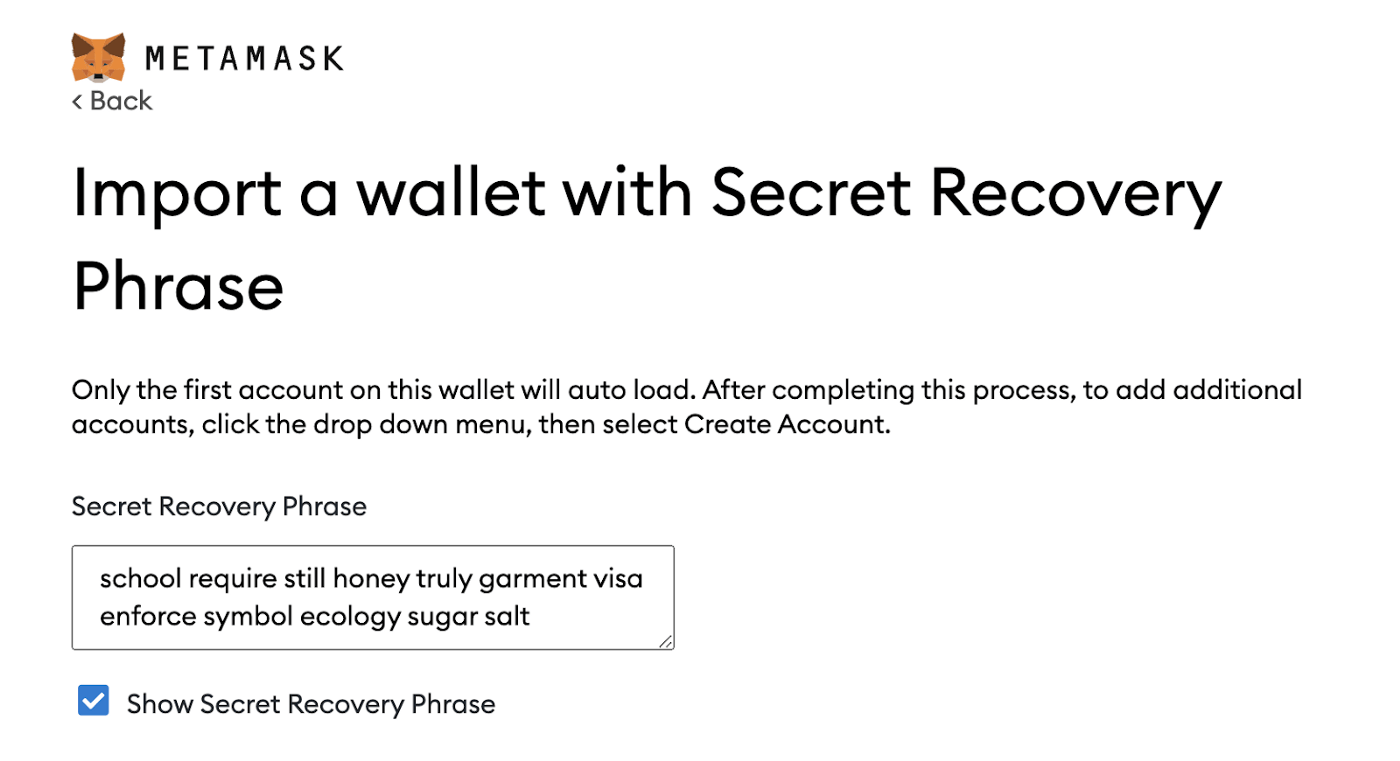
Major browsers save the text of all non-password input fields to disk unencrypted as part of the “Restore Session” characteristic. Browser extension cryptocurrency wallets that use an input field for a BIP39 mnemonic can cause the secret recovery phrase to be stored on disk in plain text. Thai text can be retrieved remotely via backdoor and then can be used to take control of the wallet.
Additionally, a threat actor with physical or remote access to the disk has equal or greater permissions than the user may be able to retrieve the secret phrase directly from memory.
The vulnerability exist if the following conditions were met:
- The Secret Recovery Phrase was imported into a browser extension wallet using a device that is no longer in the user’s possession or is logically compromised
- The hard drive is unencrypted
- The user used the “Show Secret Recovery Phrase” checkbox to view the seed phrase on-screen during import
The threat actors can steal the phrase:
- Without the user unlocking their wallet
- After a system restart
- After uninstalling the crypto wallet browser extension
- After deleting and reinstalling the browser
For Browser Wallet Providers Reproduction Of Vulnerability :
- Generate a unique secret recovery phrase
- Import the secret recovery phrase
- Wait at least 30 seconds to ensure the browser has time to record the session to disk
- Close the browser
- The secret recovery phrase can then be found in the browser session data
MITIGATION
People who use the browser extension wallet should migrate to a new set of accounts using the instructions provided by their wallet companies. They should also rotate the keys and try to use a hardware wallet.
The following mitigation measures that can be taken by wallet providers
- Split the Mnemonic Phrase input field into several fields and ensure that only one is revealed at a time.
- Alternatively of having the user enter their whole Phrase, use word selection for Mnemonic Phrase confirmation on wallet creation
- To speed up the garbage collector’s removal of the phrase from memory, clear or dereference values of variables which store Mnemonic Phrases in your code.
- Avoid showing the Mnemonic Phrase raw in the browser.
- Use an HTML5 canvas, so that the browser does not load the whole Phrase in memory.
- Another way is to obfuscate the Mnemonic Phrase as you display it. Each Mnemonic word could be displayed in a span HTML tag. In-between these spans there should be additional “fake” spans with “fake” random words. See the source for more details.
- Prevent users from directly copying/pasting the Mnemonic Phrase into the browser. The browser’s clipboard is also responsible for leaking data into memory.
- During recovery of a wallet by entering the Mnemonic Phrase, it is suggested, instead of a text area, to provide to the users one password input for each mnemonic word.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
