During the last couple of weeks, dozens of notes and reports have been published about the cybercriminal group Killnet, described as a pro-Russia hacking operation and which has become relevant in the context of the military invasion of Ukraine, engaging in a cyberwarfare campaign against alleged Anonymous hackers.
While much of what has been said about Killnet is mere guesswork, some of these assumptions have been confirmed by well-known researchers. An example of this is the work of the team behind Cyberknow, an initiative dedicated to monitoring security threats that have published a report on what is known about Killnet, including its origin, how it operates, and the main characteristics of its attacks.
Origins
It is known that Killnet started operating a few months ago, selling powerful hacking tools through Telegram. It wasn’t until early 2022 that Killnet focused its efforts on pro-Russian hacktivism, declaring war on Anonymous and any associated initiatives.
From this point, the group began to gain real relevance internationally, carrying out massive denial of service (DoS) attacks and other hacking variants, in addition to reaching some 70,000 members on its Telegram channels.
Structure
CyberKnow analyzed the channels operated by this group, concluding that Killnet has created a structure identical to that of a conventional organization, establishing hierarchical ranks, work areas, professional profiles, and affiliated groups. In the diagram shown below we can see an example of this command structure:
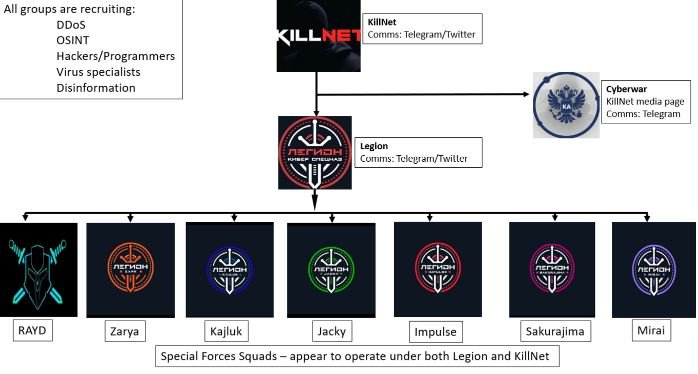
Although it is unknown how dependent the affiliated groups are on the central command, it has been confirmed that all secondary operations have participated in the attacks deployed by Killnet. Among these affiliated groups, Legion stands out, which seems to enjoy autonomy to act without receiving direct orders from Killnet, as happened in the recent attack on Eurovision.
Hacking techniques
While the report does not include great specifications on the tactics and procedures of this group, Cyberknow reports that Killnet hackers put a lot of effort into reconnaissance, targeting, and planning stages, in addition to employing sophisticated tools against politically-motivated targets outside of Russia, thus posing a considerable threat at a time of high international tensions.
To learn more about information security risks, malware variants, vulnerabilities, and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
