A report by cybersecurity firm Armblox notes that a hacking group is using the image of the WeTransfer hosting system and Microsoft Excel to deploy ambitious phishing campaigns in order to recover the Office 365 email credentials of affected users.
As some users will remember, WeTransfer is used by millions of users to share files too large to send via email.
The emails used by the hackers are crafted in such a way that they appear to come from WeTransfer, using images and the company name. These messages appear to be similar enough to trick unsuspecting users into saying that they were sent two files and should download them via an attached link.
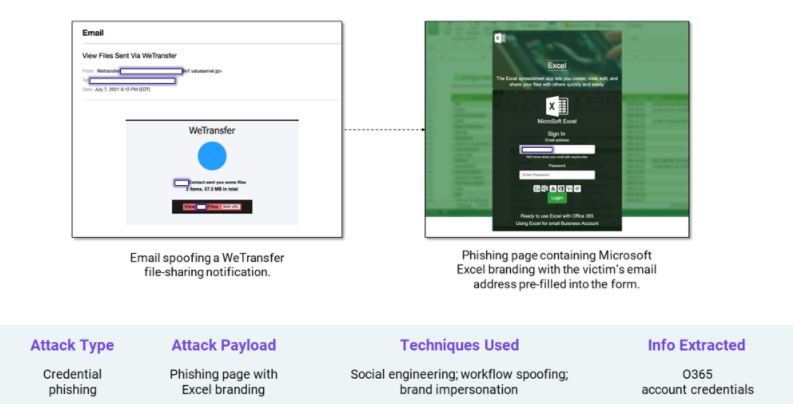
The message also makes several references to the target organization so that the user does not suspect fraudulent activity. Clicking “View Files” redirects the victims to a page with a supposed Microsoft Excel file. The page contains a blurry worksheet in the background and a form for capturing the login details in the foreground. This form already has the email address of the target user set by default, giving a sense of greater legitimacy.
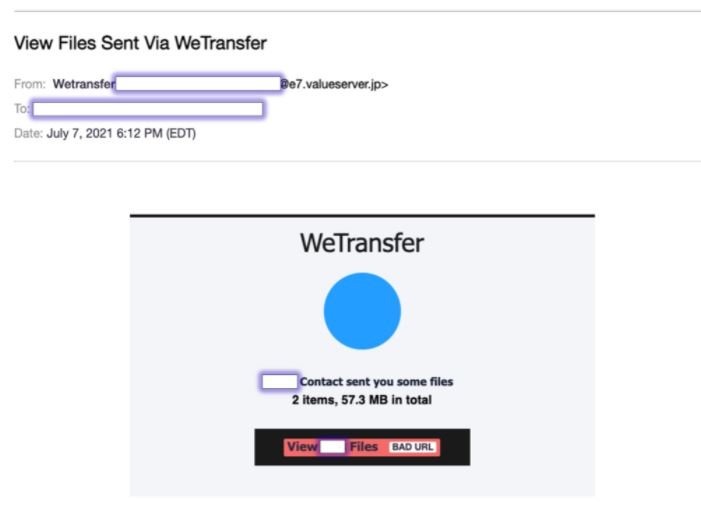
A quick analysis of this campaign reveals that the attackers’ domain is a Japan-based hosting service provider known as “valueserver.jp.” A few months ago, researcher Laur Telliskivi reported that this domain was being used to deploy a separate phishing attack.
The threat actors in charge of this campaign employ a variety of techniques to avoid detection by conventional security tools such as email filters. The attackers also engage in social engineering tactics in their scheme, as the title of the email, its content and the name of the sender were specifically set to deceive users.
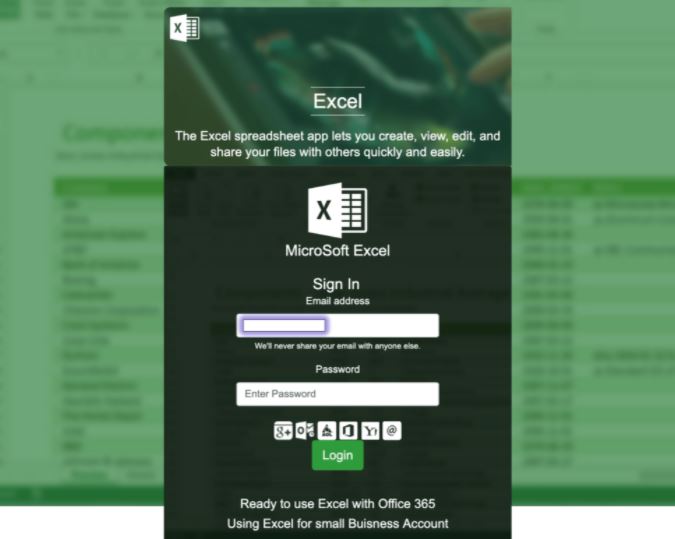
Another very popular technique used in this campaign is brand impersonation; In this attack, the HTML style of the email is incredibly similar to WeTransfer, and the phishing page is designed to appear as the legitimate Microsoft Excel login page. The only thing that makes it seem suspicious is that Microsoft is written as MicroSoft, although this can be imperceptible to many users.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
