Cybersecurity specialists have revealed a new method of social engineering attack on the Cisco WebEx video conferencing platform. In this attack, threat actors pose as a Cisco notification to steal target user login credentials.
As we know, thousands of companies have made enormous efforts to maintain their operations remotely amid the coronavirus pandemic, so video conferencing platforms have become a really useful resource. However, this also poses a risk, as threat actors are taking advantage of the extensive use of services such as Webex to deploy large information theft campaigns.
To begin with, the attacker sends an email impersonating an automated Cisco Webex email address, copying the format and graphics used by the company. In the message, the threat actor states that the user cannot use the service, as their account has been blocked. In addition, hackers mention to the user that they will need to log in to an attached link to unlock their account.
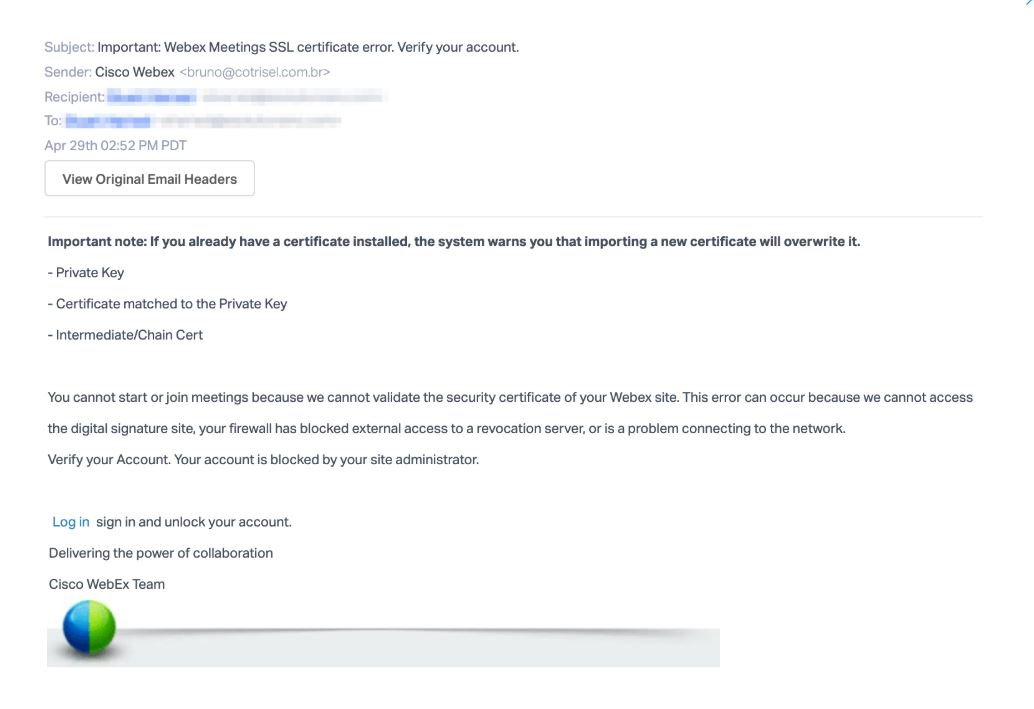
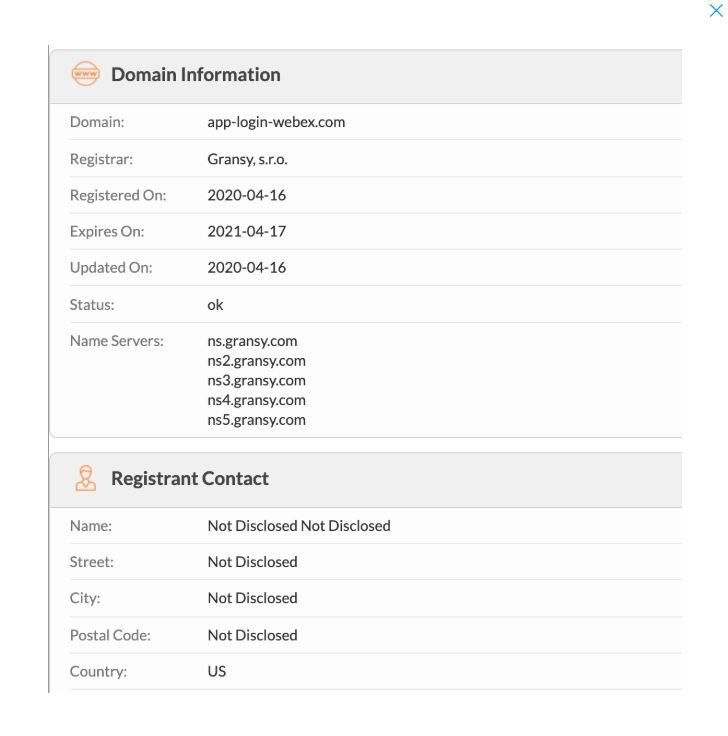
This link redirects the target user to a Cisco WebEx phishing credential site hosted in “https://app-login-webex.com/”. The domain of this website was recently registered by a Czech firm.
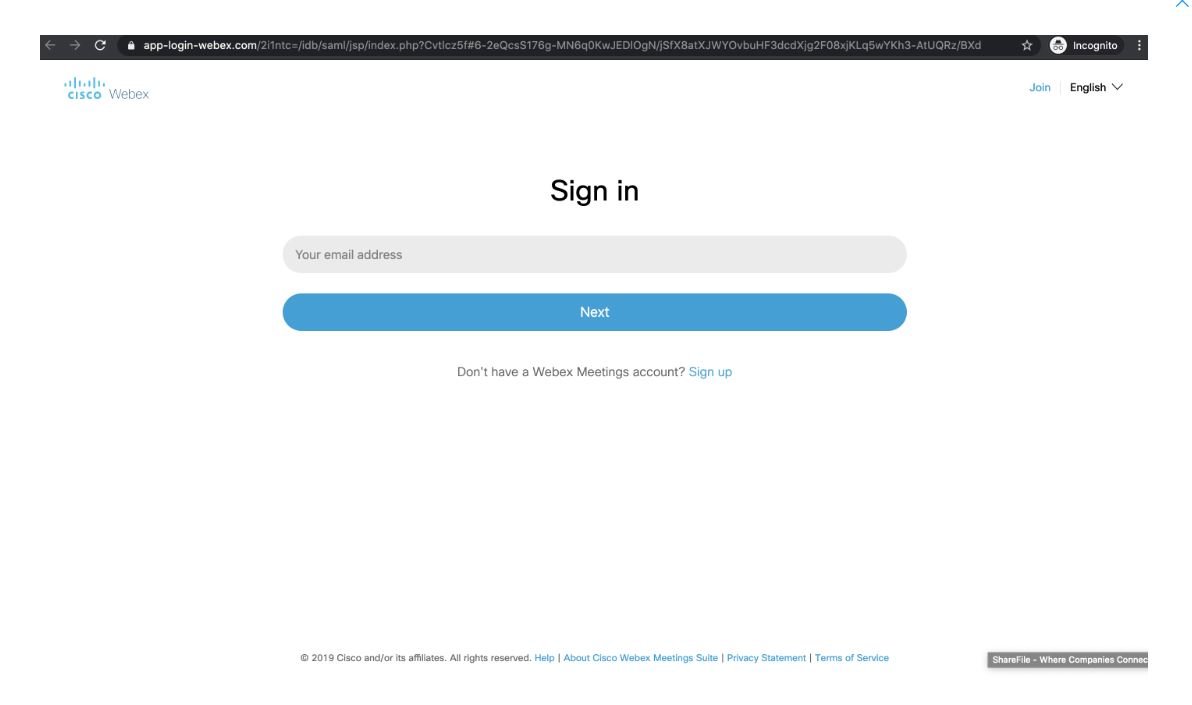
If the user falls into the trap and enters their login credentials on this phishing page, their Cisco Webex account and all the information stored there will be compromised. Threat actors could use Webex accounts to deploy subsequent attacks on an organization’s networks.
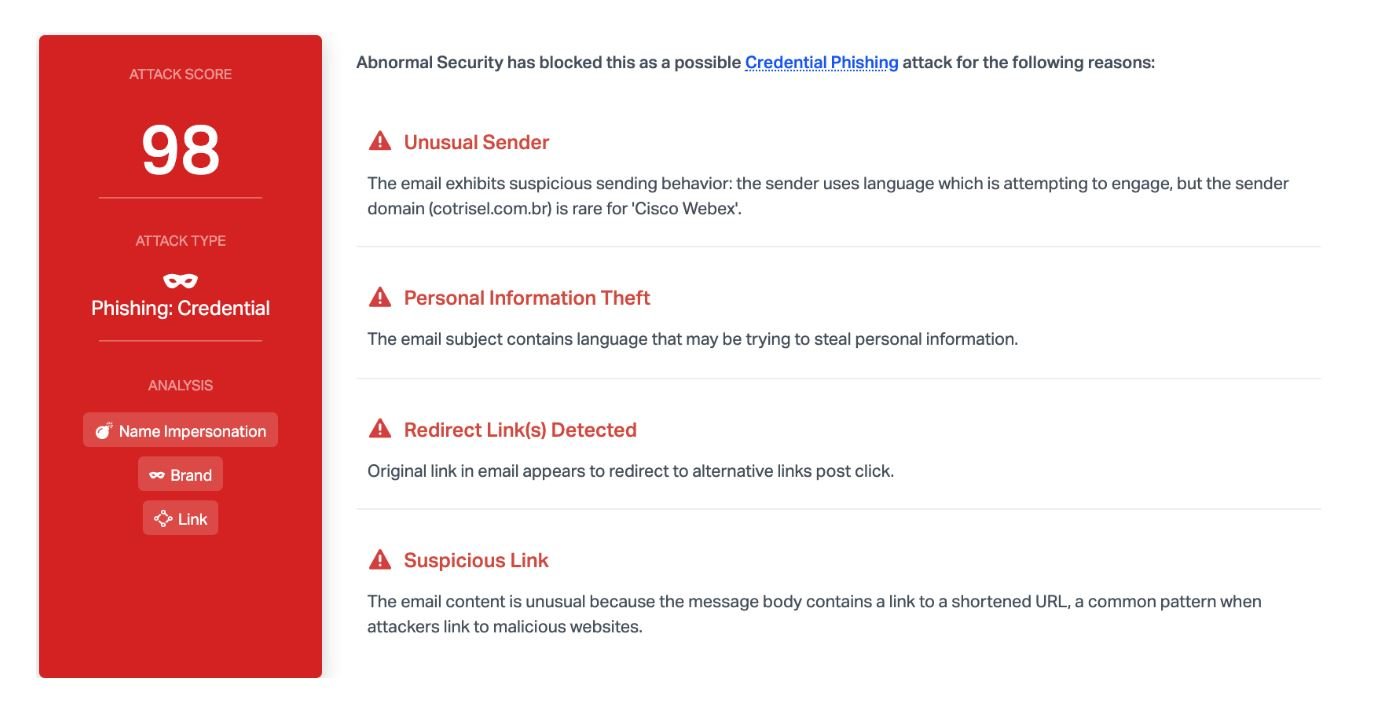
Cybersecurity experts consider this attack to be highly effective because of the global context; as Webex has become a fundamental tool for remote work, users are alarmed that their account could be blocked for some unknown reason. Threat actors take advantage of the sense of urgency that users experience, so there is a greater chance of success in the attack.
Another risk factor is the similarity between the messages and the website used by hackers and authentic Cisco material, making it really easy for a user to be tricked. At first glance, it may seem that the link is authentic because “webex” is included in the URL title of the hackers. However, paying a little attention, it can be seen that the domain is not registered with Cisco or its affiliates.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
