Cybersecurity specialists report the detection of a denial of service (DoS) attack with very interesting features. According to Imperva researchers, this attack reaches a rate of 2.5 million requests per second, in addition to showing a ransom note to victims.
DoS attacks that demand ransoms from victims are not unusual and they are often very effective due to the sense of urgency of not being able to access the affected systems. In this case, the attackers had left various ransom notes even before starting the attack.
The security firm managed to mitigate more than 12 million embedded requests targeting random URLs on the same site. The following message was incorporated into one of the affected URLs:
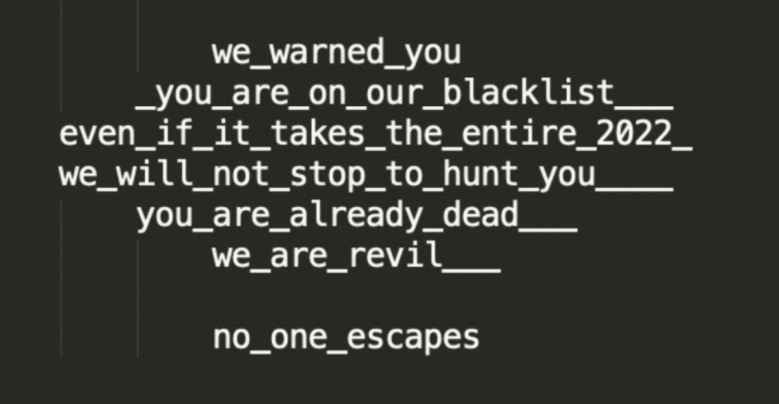
Hours later, more than 15 million requests were mitigated, this time with the URL containing a different message but using the same intimidation tactics, warning website administrators that they would face disastrous consequences if they refused to pay.
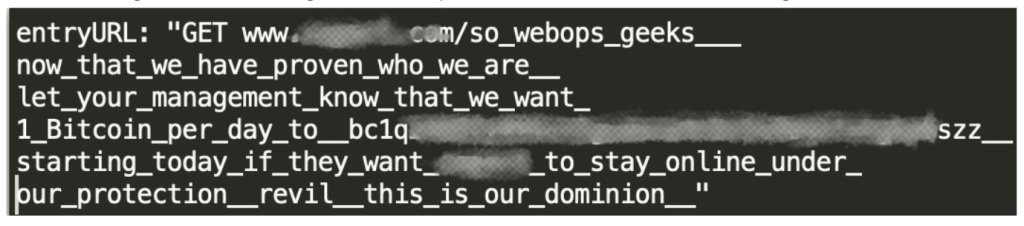
According to the report, the attack originated from 34,815 sources, with 2 million requests per IP sent from major sources during the attack. The main source locations of the attack of 2.5 million requests were identified in Indonesia and the United States, with a pattern of nearly identical source locations for different attacks, indicating that the same botnet was used multiple times.
These attacks relate to CVE-2018-14847, a MikroTik vulnerability in which thousands of Internet of Things (IoT) devices were manipulated to create a botnet capable of deploying DoS attacks and other hacking variants.
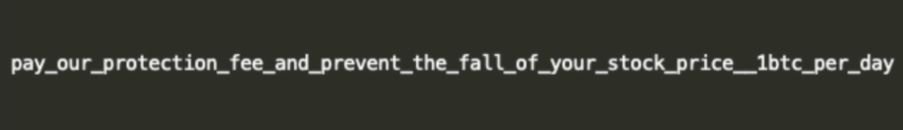
Most of the targets of this campaign appear to be located in the United States or Europe and, according to the report, the companies targeted are publicly traded and threat actors use this to their own advantage.
Other ransom notes that appear later more closely resemble tactics related to ransomware attacks.
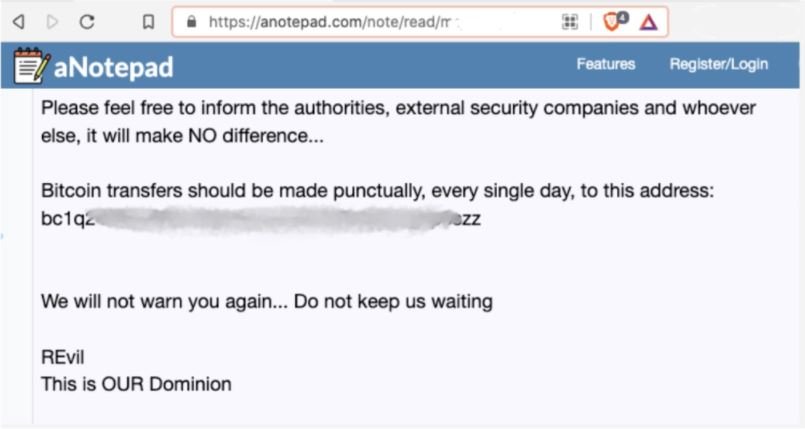
The researchers mention that the best way to protect against these attacks is to prevent the exploitation of known vulnerabilities in network devices, keeping your systems always up to date and proof of malicious botnet activity.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) websites.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
