Specialists from security firm Vedere Labs published research detailing how a ransomware variant could spread across an enterprise network using vulnerable Internet of Things (IoT) devices.
For their research, the experts developed a proof of concept (PoC) malware variant identified as R4IoT; after initial access, this strain can move laterally through a computer network to deliver ransomware and cryptojacking software and steal sensitive information, while disrupting critical business operations.
The researchers note that this idea was developed considering the evolutionary nature of ransomware groups, which are no longer limited to encrypting information and demanding ransoms in exchange for a decryption key. Instead, ransomware operations now encrypt data, demand ransoms, steal sensitive information before encrypting it, and sell it on the dark web, as well as launch denial of service (DoS) attacks against affected organizations.
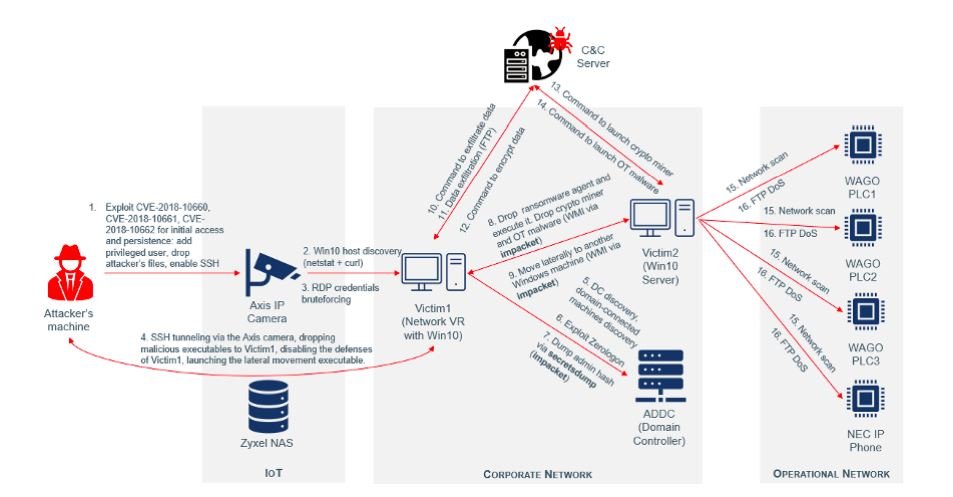
An attack combining ransomware techniques and abuse of IoT devices could be highly disruptive to an affected network, allowing for the rapid deployment of the infection. R4IoT is capable of exploiting the flaws in these devices, so it was proven that this is a real attack vector and that it should worry the technology industry.
Luckily, this malware exists only as a concept, developed in test environments to demonstrate a potential IoT exploit attempt using ransomware. Still, testing could take little time to reach in the wild scenarios.
Time trial
As mentioned above, the determining factor in facilitating these kinds of hacking scenarios could be the growing number of IoT devices in enterprise networks, as they could easily become the ideal entry point for threat actors.
At the time of writing, IoT devices represent more than 40% of technological devices connected to business networks. Researchers believe that cybercriminals will start targeting these devices for ransomware attacks when they exceed 50% of computers on a network, which could happen in less than two years.
Before it’s too late, organizations could begin to identify potential vulnerabilities and more obvious entry points, including IoT devices and conventional technology equipment. Once these threats have been identified, it is best to implement all the necessary security controls to prevent exploitation, in addition to correcting known vulnerabilities in IoT plugins.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
He is a cyber security and malware researcher. He studied Computer Science and started working as a cyber security analyst in 2006. He is actively working as an cyber security investigator. He also worked for different security companies. His everyday job includes researching about new cyber security incidents. Also he has deep level of knowledge in enterprise security implementation.
